mirror of
https://github.com/jeecgboot/JeecgBoot.git
synced 2026-01-03 20:35:29 +08:00
Compare commits
35 Commits
44b48ad916
...
springboot
| Author | SHA1 | Date | |
|---|---|---|---|
| 3e107d766e | |||
| cac4121209 | |||
| 26087172df | |||
| 281c3ff3c8 | |||
| 38d44c2487 | |||
| 8c88f8adf5 | |||
| 526734c5a5 | |||
| 3599120c94 | |||
| cf9b407a18 | |||
| a194d4e9b2 | |||
| 21585e4d25 | |||
| 0489d30296 | |||
| ed87ac3bff | |||
| 761dbf0343 | |||
| 23c628057b | |||
| 2ac14709ba | |||
| f9cff08716 | |||
| a6feb2fd9d | |||
| b84eb25d41 | |||
| 4326cecad4 | |||
| ec5810176b | |||
| aff307c3ff | |||
| acfd3bb3e4 | |||
| 52082fb256 | |||
| 736515f63a | |||
| a250163198 | |||
| 1ed1f315a4 | |||
| f7670dca3a | |||
| b24ac544c8 | |||
| c7c31e0945 | |||
| 468af57489 | |||
| c85bb1f62d | |||
| b4fa11a605 | |||
| b2240848e0 | |||
| 4a888a4e19 |
@ -3,9 +3,6 @@ AIGC应用平台介绍
|
||||
|
||||
一个全栈式 AI 开发平台,旨在帮助开发者快速构建和部署个性化的 AI 应用。
|
||||
|
||||
> JDK说明:AI流程编排引擎暂时不支持jdk21,所以目前只能使用jdk8或者jdk17启动项目。
|
||||
|
||||
|
||||
JeecgBoot平台的AIGC功能模块,是一套类似`Dify`的`AIGC应用开发平台`+`知识库问答`,是一款基于LLM大语言模型AI应用平台和 RAG 的知识库问答系统。
|
||||
其直观的界面结合了 AI 流程编排、RAG 管道、知识库管理、模型管理、对接向量库、实时运行可观察等,让您可以快速从原型到生产,拥有AI服务能力。
|
||||
|
||||
|
||||
@ -1,126 +0,0 @@
|
||||
|
||||
JeecgBoot低代码平台(商业版介绍)
|
||||
===============
|
||||
|
||||
|
||||
|
||||
项目介绍
|
||||
-----------------------------------
|
||||
|
||||
<h3 align="center">企业级AI低代码平台</h3>
|
||||
|
||||
|
||||
JeecgBoot是一款集成AI应用的,基于BPM流程的低代码平台,旨在帮助企业快速实现低代码开发和构建个性化AI应用,支持MCP和插件,实现聊天式业务操作(如 “一句话创建用户”)!
|
||||
|
||||
前后端分离架构Ant Design&Vue3,SpringBoot,SpringCloud Alibaba,Mybatis-plus,Shiro。强大的代码生成器让前后端代码一键生成,无需写任何代码! 引领AI低代码开发模式: AI生成->OnlineCoding-> 代码生成-> 手工MERGE, 帮助Java项目解决80%的重复工作,让开发更多关注业务,提高效率、节省成本,同时又不失灵活性!低代码能力:Online表单、表单设计、流程设计、Online报表、大屏/仪表盘设计、报表设计; AI应用平台功能:AI知识库问答、AI模型管理、AI流程编排、AI聊天等,支持含ChatGPT、DeepSeek、Ollama等多种AI大模型
|
||||
|
||||
JeecgBoot 提供了一系列 `低代码能力`,实现`真正的零代码`在线开发:Online表单开发、Online报表、复杂报表设计、打印设计、在线图表设计、仪表盘设计、大屏设计、移动图表能力、表单设计器、在线设计流程、流程自动化配置、插件能力(可插拔)
|
||||
|
||||
`AI赋能低代码:` 目前提供了AI应用、AI模型管理、AI流程编排、AI对话助手,AI建表、AI写文章、AI知识库问答、AI字段建议等功能;支持各种AI大模型ChatGPT、DeepSeek、Ollama、智普、千问等.
|
||||
|
||||
`JEECG宗旨是:` 简单功能由OnlineCoding配置实现,做到`零代码开发`;复杂功能由代码生成器生成进行手工Merge 实现`低代码开发`,既保证了`智能`又兼顾`灵活`;实现了低代码开发的同时又支持灵活编码,解决了当前低代码产品普遍不灵活的弊端!
|
||||
|
||||
`JEECG业务流程:` 采用工作流来实现、扩展出任务接口,供开发编写业务逻辑,表单提供多种解决方案: 表单设计器、online配置表单、编码表单。同时实现了流程与表单的分离设计(松耦合)、并支持任务节点灵活配置,既保证了公司流程的保密性,又减少了开发人员的工作量。
|
||||
|
||||
|
||||
|
||||
#### JeecgBoot商业版与同类产品区别
|
||||
-----------------------------------
|
||||
|
||||
- 灵活性:jeecgboot基于开源技术栈,设计初考虑到可插拔性和集成灵活性,确保平台的智能性与灵活性,避免因平台过于庞大而导致的扩展困难。
|
||||
- 流程管理:支持一个表单挂接多个流程,同时一个流程可以连接多个表单,增强了流程的灵活性和复杂性管理。
|
||||
- 符合中国国情的流程:针对中国市场的特定需求,jeecgboot能够实现各种符合中国国情的业务流程。
|
||||
- 强大的表单设计器:jeecgboot的表单设计器与敲敲云共享,具备高质量和智能化的特点,能够满足零代码应用的需求,业内同类产品中不多见。
|
||||
- 报表功能:自主研发的报表工具,拥有独立知识产权,功能上比业内老牌产品如帆软更智能,操作简便。
|
||||
- BI产品整合:提供大屏、仪表盘、门户等功能,完美解决这些需求,并支持移动面板的设计与渲染。
|
||||
- 自主研发的模块:jeecgboot的所有模块均为自主研发,具有独立的知识产权。
|
||||
- 颗粒度和功能细致:在功能细致度和颗粒度上,jeecgboot远超同类产品,尤其在零代码能力方面表现突出。
|
||||
- 零代码应用管理:最新版支持与敲敲云的零代码应用管理能力的集成,使得jeecgboot既具备低代码,又具备零代码的应用能力,业内独一无二。
|
||||
- 强大的代码生成器:作为开源代码生成器的先锋,jeecgboot在代码生成的智能化和在线低代码与代码生成的结合方面,优势明显。
|
||||
- 精细化权限管理:提供行级和列级的数据权限控制,满足企业在ERP和OA领域对权限管理的严格需求。
|
||||
- 多平台支持的APP:目前采用uniapp3实现,支持小程序、H5、App及鸿蒙、鸿蒙Next、Electron桌面应用等多种终端。
|
||||
|
||||
> 综上所述,jeecgboot不仅在功能上具备丰富性和灵活性,还在技术架构、权限管理和用户体验等方面展现出明显的优势,是一个综合性能强大的低代码平台。
|
||||
|
||||
|
||||
|
||||
商业版演示
|
||||
-----------------------------------
|
||||
|
||||
JeecgBoot vs 敲敲云
|
||||
> - JeecgBoot是低代码产品拥有系列低代码能力,比如流程设计、表单设计、大屏设计,代码生成器,适合半开发模式(开发+低代码结合),也可以集成零代码应用管理模块.
|
||||
> - 敲敲云是零代码产品,完全不写代码,通过配置搭建业务系统,其在jeecgboot基础上研发而成,删除了online、代码生成、OA等需要编码功能,只保留应用管理功能和聊天、日程、文件三个OA组件.
|
||||
|
||||
|
||||
- JeecgBoot低代码: https://boot3.jeecg.com
|
||||
- 敲敲云零代码:https://app.qiaoqiaoyun.com
|
||||
- APP演示(多端): http://jeecg.com/appIndex
|
||||
|
||||
|
||||
### 流程视频介绍
|
||||
|
||||
[](https://www.bilibili.com/video/BV1Nk4y1o7Qc)
|
||||
|
||||
|
||||
|
||||
### 商业版功能简述
|
||||
|
||||
> 详细的功能介绍,[请联系官方](https://jeecg.com/vip)
|
||||
|
||||
```
|
||||
│─更多商业功能
|
||||
│ ├─流程设计器
|
||||
│ ├─简流设计器(类钉钉版)
|
||||
│ ├─门户设计(NEW)
|
||||
│ ├─表单设计器
|
||||
│ ├─大屏设计器
|
||||
│ └─我的任务
|
||||
│ └─历史流程
|
||||
│ └─历史流程
|
||||
│ └─流程实例管理
|
||||
│ └─流程监听管理
|
||||
│ └─流程表达式
|
||||
│ └─我发起的流程
|
||||
│ └─我的抄送
|
||||
│ └─流程委派、抄送、跳转
|
||||
│ └─OA办公组件
|
||||
│ └─零代码应用管理(无需编码,在线搭建应用系统)
|
||||
│ ├─积木报表企业版(含jimureport、jimubi)
|
||||
│ ├─AI流程设计器源码
|
||||
│ ├─Online全模块功能和源码
|
||||
│ ├─AI写文章(CMS)
|
||||
│ ├─AI表单字段建议(表单设计器)
|
||||
│ ├─OA办公协同组件
|
||||
│ ├─在线聊天功能
|
||||
│ ├─设计表单移动适配
|
||||
│ ├─设计表单支持外部填报
|
||||
│ ├─设计表单AI字段建议
|
||||
│ ├─设计表单视图功能(支持多种类型含日历、表格、看板、甘特图)
|
||||
│ └─。。。
|
||||
|
||||
```
|
||||
|
||||
|
||||
|
||||
|
||||
##### 流程设计
|
||||
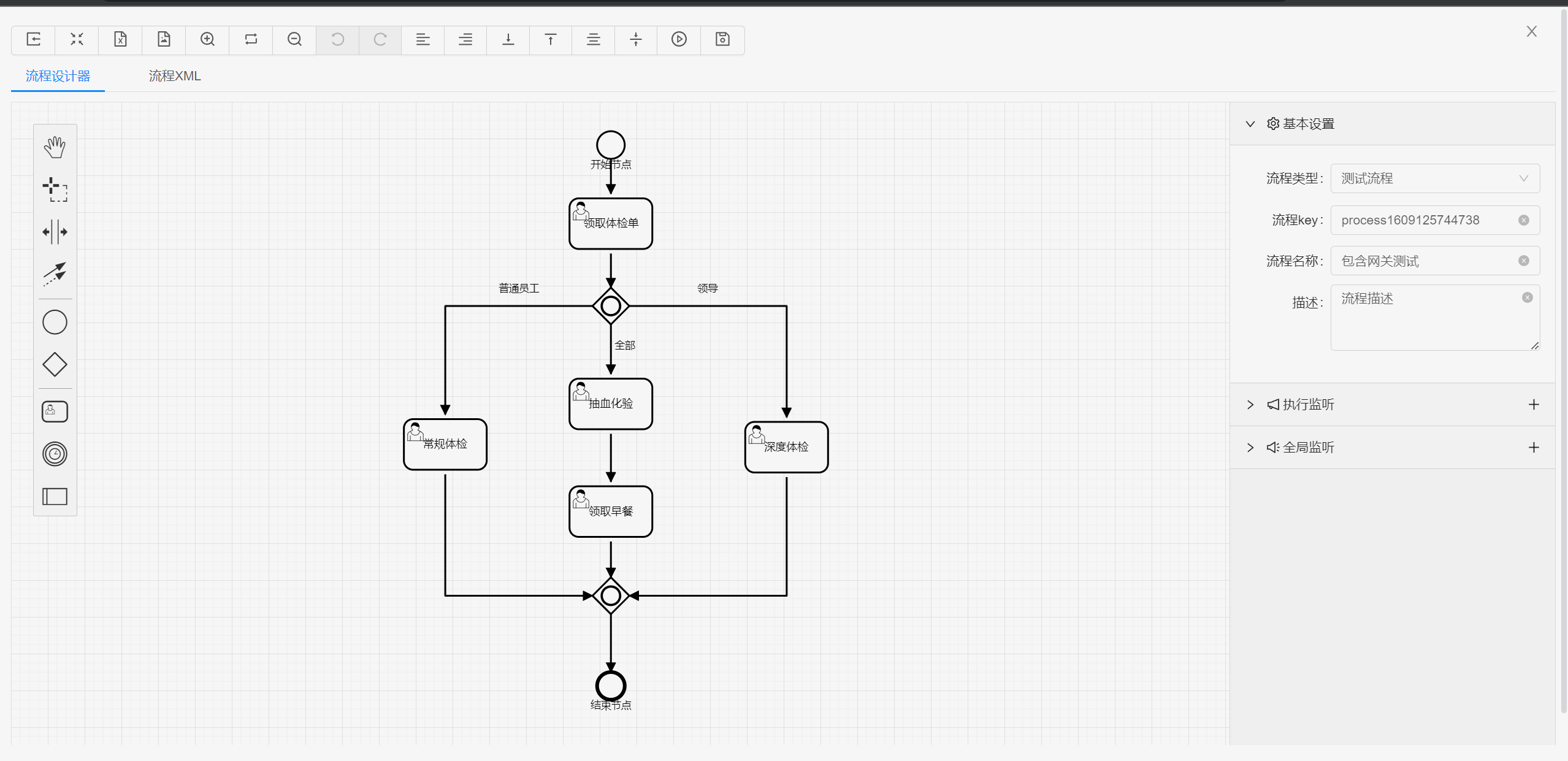
|
||||
|
||||
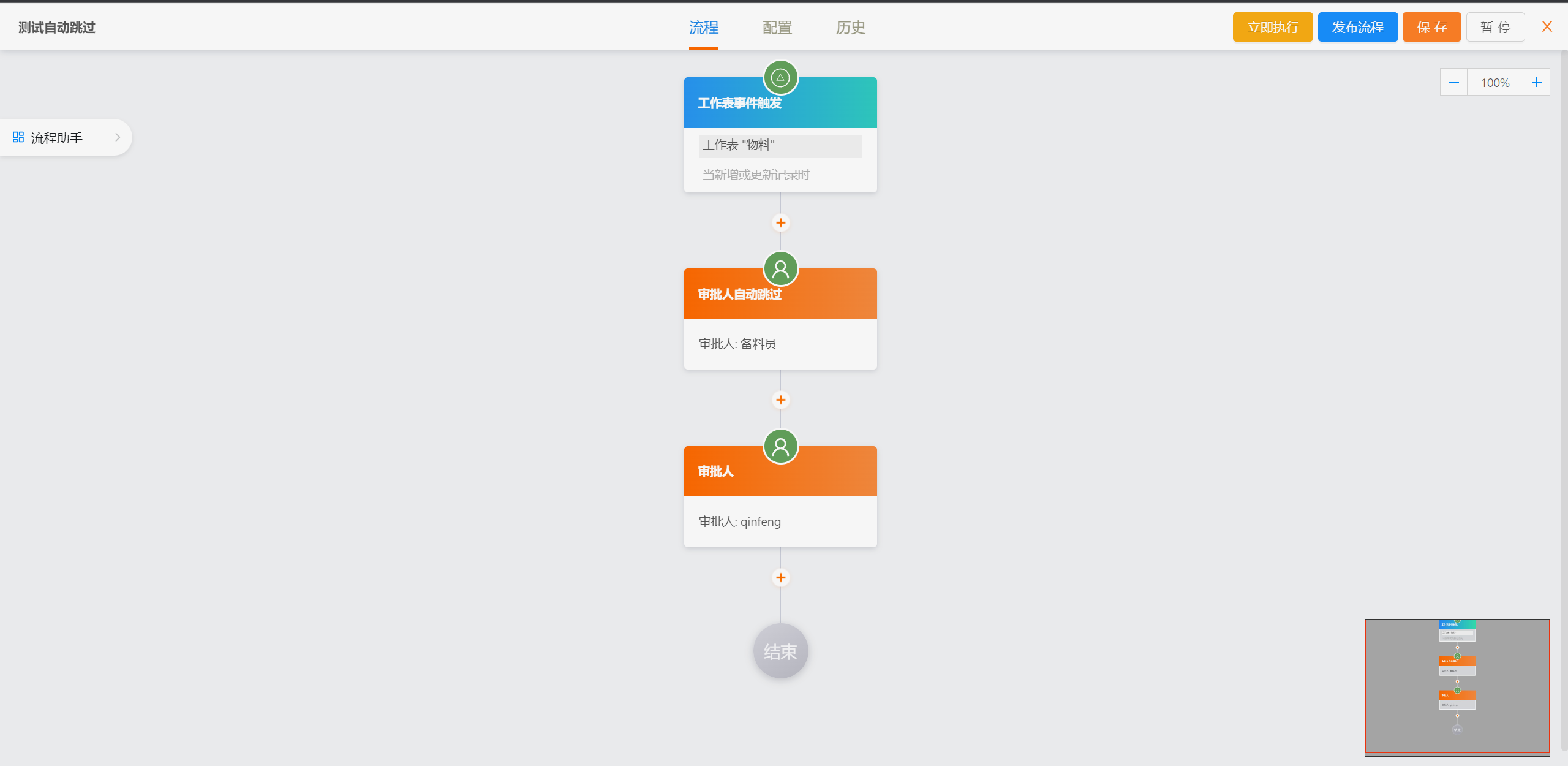
|
||||
|
||||
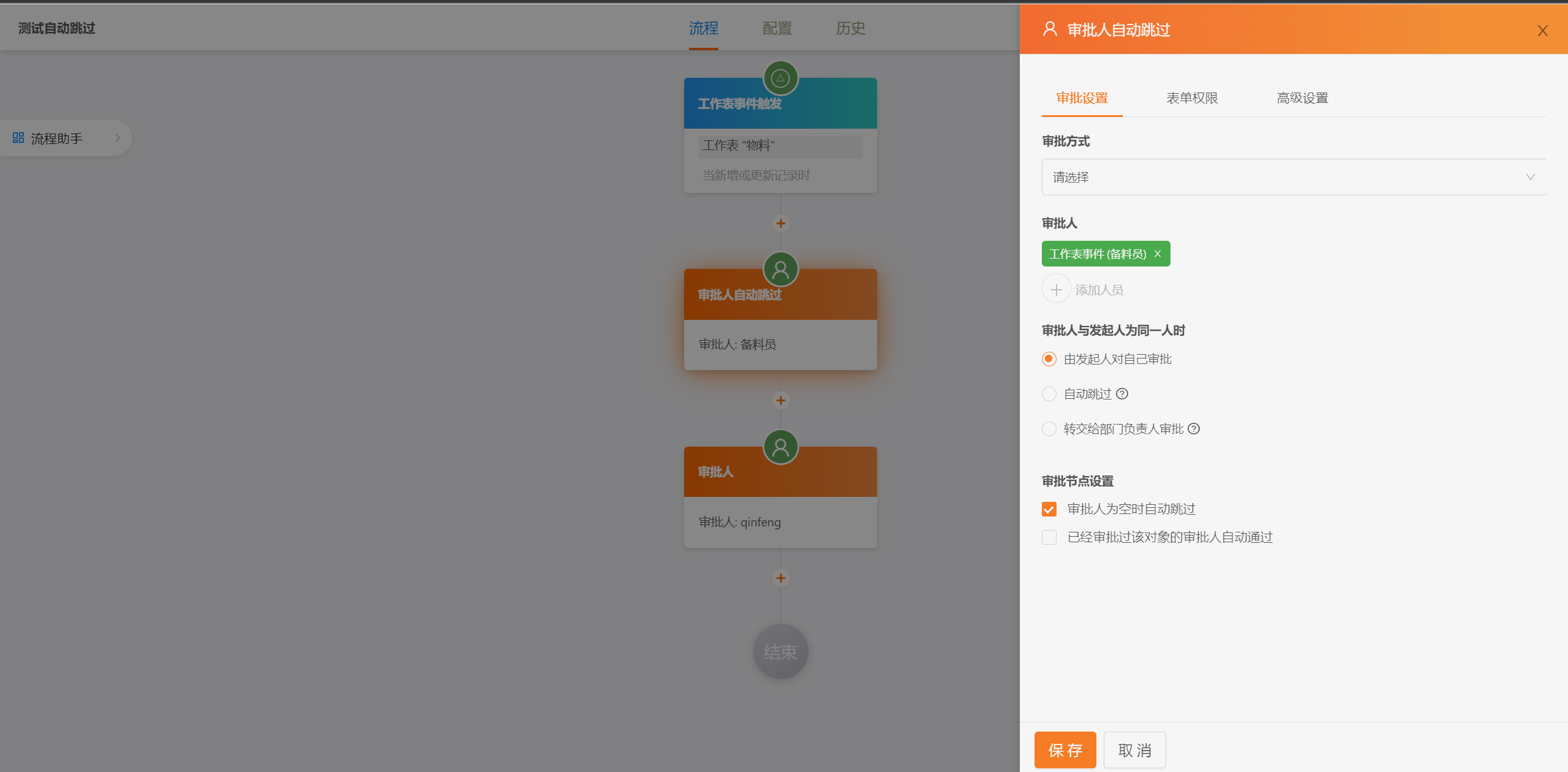
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
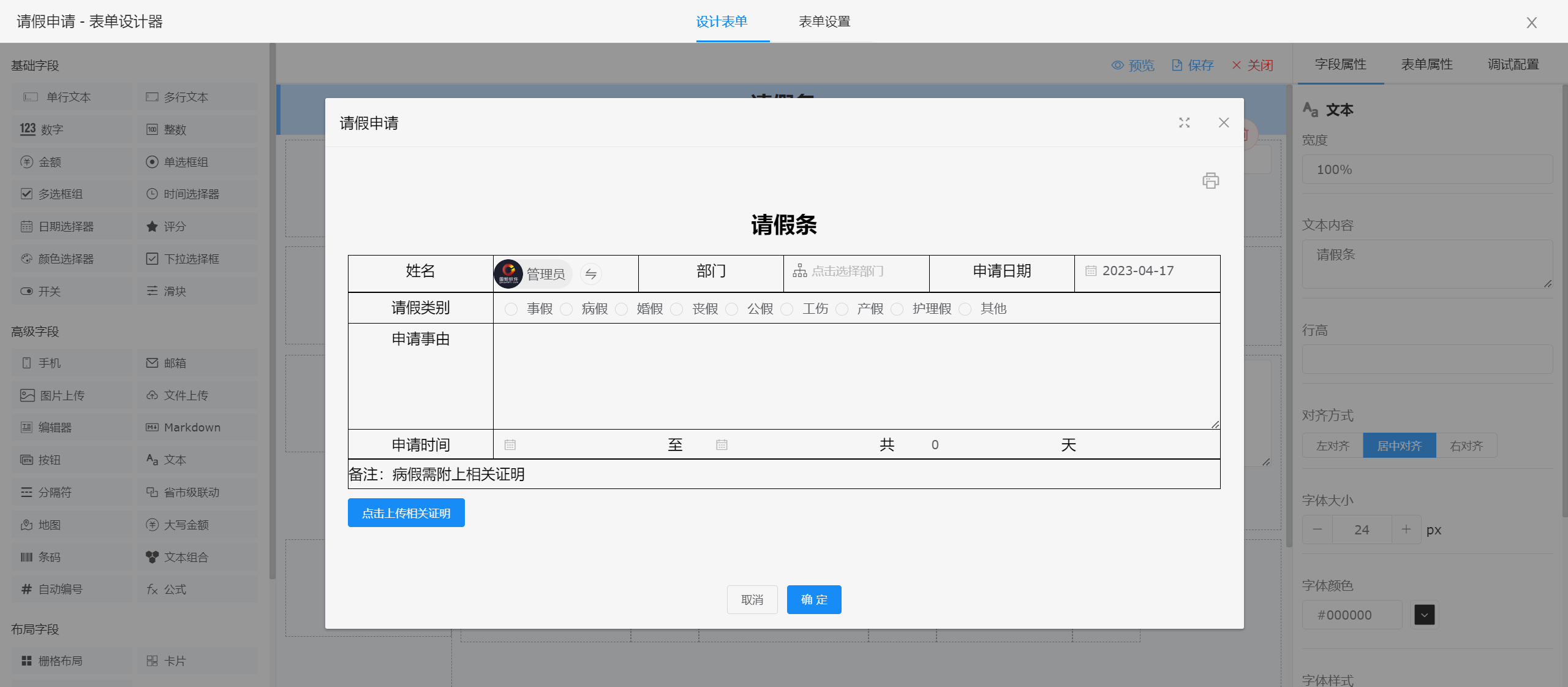
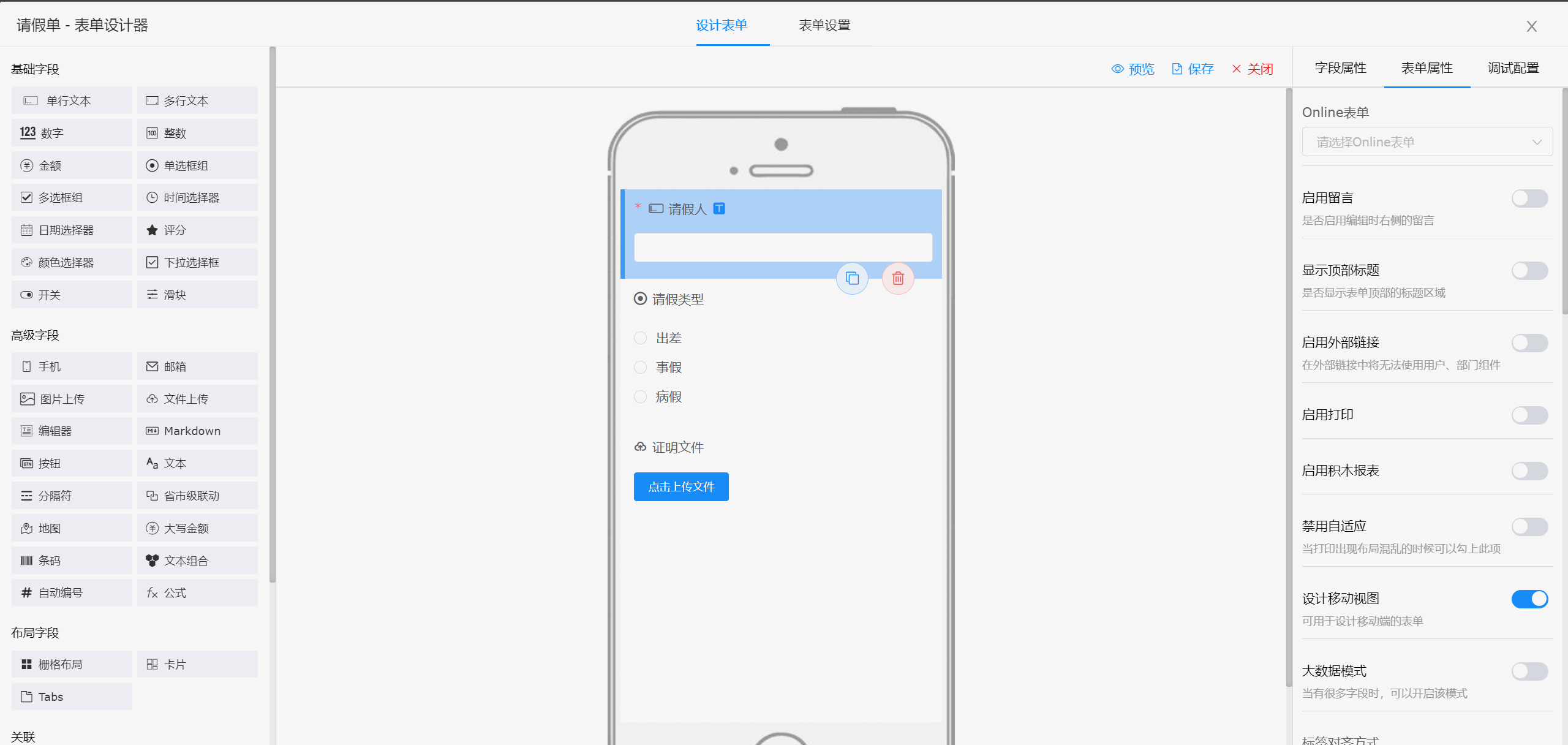
##### 表单设计器
|
||||
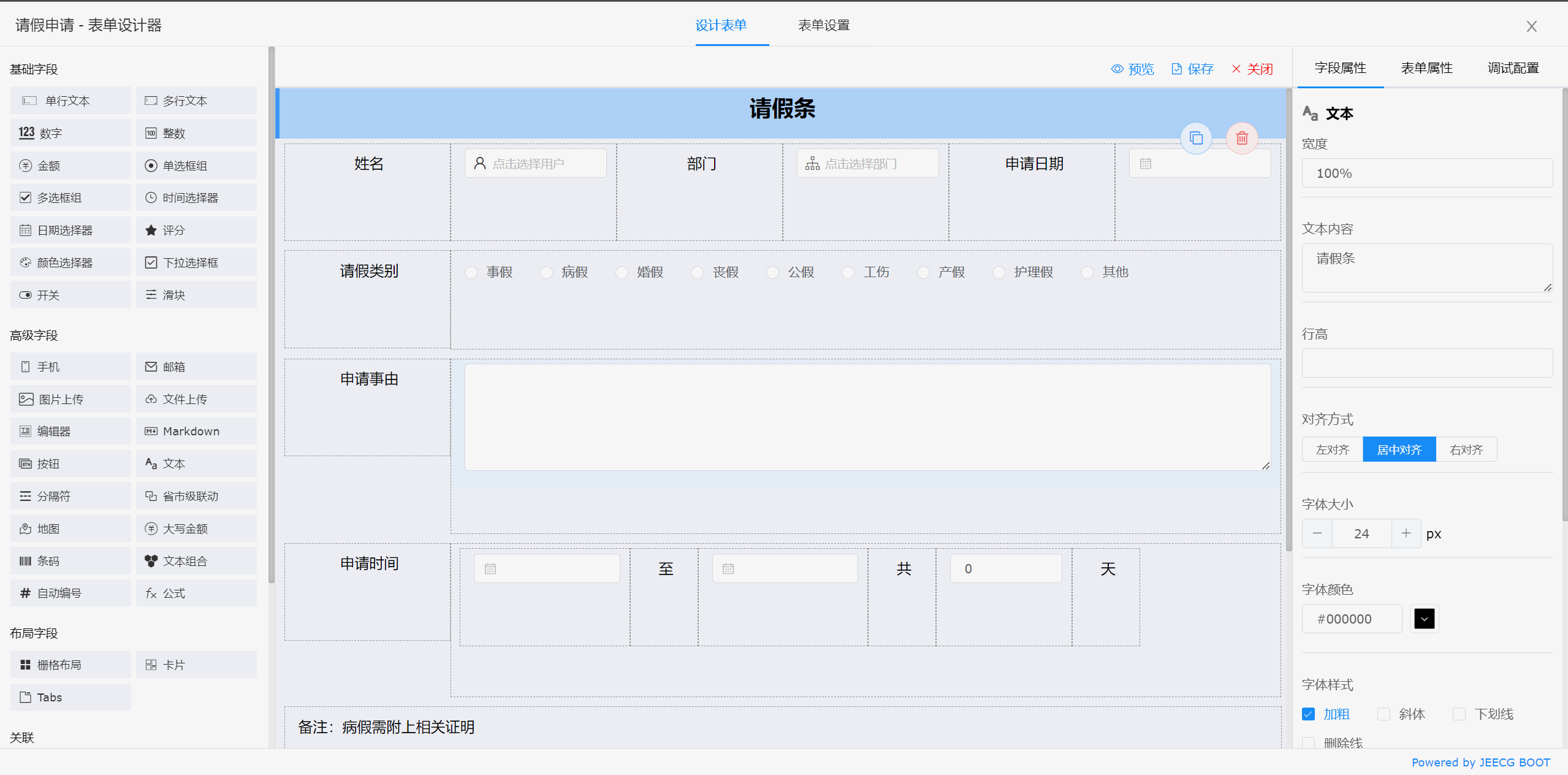
|
||||
|
||||
|
||||
|
||||
|
||||
14
README.md
14
README.md
@ -232,20 +232,6 @@ JeecgBoot平台提供了一套完善的AI应用管理系统模块,是一套类
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
开源版与企业版区别?
|
||||
-----------------------------------
|
||||
|
||||
- JeecgBoot开源版采用 [Apache-2.0 license](LICENSE) 协议附加补充条款:允许商用使用,不会造成侵权行为,允许基于本平台软件开展业务系统开发(但在任何情况下,您不得使用本软件开发可能被认为与本软件竞争的软件).
|
||||
- 商业版与开源版主要区别在于商业版提供了技术支持 和 更多的企业级功能(例如:Online图表、流程监控、流程设计、流程审批、表单设计器、表单视图、积木报表企业版、OA办公、商业APP、零代码应用、Online模块源码等功能). [更多商业功能介绍,点击查看](README-Enterprise.md)
|
||||
- JeecgBoot未来发展方向是:零代码平台的建设,也就是团队的另外一款产品 [敲敲云零代码](https://www.qiaoqiaoyun.com) ,无需编码即可通过拖拽快速搭建企业级应用,与JeecgBoot低代码平台形成互补,满足从简单业务到复杂系统的全场景开发需求,目前已经开源,[欢迎下载](https://qiaoqiaoyun.com/downloadCode)
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
### Jeecg Boot 产品功能蓝图
|
||||

|
||||
|
||||
|
||||
368
jeecg-boot/Shiro到Sa-Token迁移指南.md
Normal file
368
jeecg-boot/Shiro到Sa-Token迁移指南.md
Normal file
@ -0,0 +1,368 @@
|
||||
# `Shiro 到 Sa-Token 迁移指南`
|
||||
|
||||
本项目已从 **Apache Shiro 2.0.4** 迁移到 **Sa-Token 1.44.0**,采用 JWT-Simple 模式,完全兼容原 JWT token 格式。
|
||||
|
||||
---
|
||||
|
||||
## 📦 1. 依赖配置
|
||||
|
||||
### 1.1 Maven 依赖
|
||||
|
||||
移除 Shiro 相关依赖,新增:
|
||||
|
||||
```xml
|
||||
<dependency>
|
||||
<groupId>cn.dev33</groupId>
|
||||
<artifactId>sa-token-spring-boot3-starter</artifactId>
|
||||
<version>1.44.0</version>
|
||||
</dependency>
|
||||
<dependency>
|
||||
<groupId>cn.dev33</groupId>
|
||||
<artifactId>sa-token-redis-jackson</artifactId>
|
||||
<version>1.44.0</version>
|
||||
</dependency>
|
||||
<dependency>
|
||||
<groupId>cn.dev33</groupId>
|
||||
<artifactId>sa-token-jwt</artifactId>
|
||||
<version>1.44.0</version>
|
||||
</dependency>
|
||||
```
|
||||
|
||||
### 1.2 配置文件(application.yml)
|
||||
|
||||
```yaml
|
||||
sa-token:
|
||||
token-name: X-Access-Token
|
||||
timeout: 2592000 # token有效期30天
|
||||
is-concurrent: true # 允许同账号并发登录
|
||||
token-style: jwt-simple # JWT模式(兼容原格式)
|
||||
jwt-secret-key: "your-secret-key-here"
|
||||
```
|
||||
|
||||
---
|
||||
|
||||
## 💡 2. 核心代码实现
|
||||
|
||||
### 2.1 登录逻辑(⚠️ 使用 username 作为 loginId)
|
||||
|
||||
```java
|
||||
// 从数据库查询用户信息
|
||||
SysUser sysUser = userService.getUserByUsername(username);
|
||||
|
||||
// 执行登录(自动完成:Sa-Token登录 + 存储Session + 返回token)
|
||||
String token = LoginUserUtils.doLogin(sysUser);
|
||||
|
||||
// 返回token给前端
|
||||
return Result.ok(token);
|
||||
```
|
||||
|
||||
**💡 设计说明:**
|
||||
- `doLogin()` 方法自动完成:
|
||||
1. 调用 `StpUtil.login(username)` (使用 username 而非 userId)
|
||||
2. 调用 `setSessionUser()` 存储用户信息(自动清除 password 等15个字段)
|
||||
3. 返回生成的 token
|
||||
- 减少 Redis 存储约 50%,密码不再存储到 Session
|
||||
|
||||
### 2.2 权限认证接口(⚠️ 必须手动实现缓存)
|
||||
|
||||
```java
|
||||
@Component
|
||||
public class StpInterfaceImpl implements StpInterface {
|
||||
|
||||
@Lazy @Resource
|
||||
private CommonAPI commonApi;
|
||||
|
||||
private static final long CACHE_TIMEOUT = 60 * 60 * 24 * 30; // 30天
|
||||
private static final String PERMISSION_CACHE_PREFIX = "satoken:user-permission:";
|
||||
private static final String ROLE_CACHE_PREFIX = "satoken:user-role:";
|
||||
|
||||
@Override
|
||||
@SuppressWarnings("unchecked")
|
||||
public List<String> getPermissionList(Object loginId, String loginType) {
|
||||
String username = loginId.toString();
|
||||
String cacheKey = PERMISSION_CACHE_PREFIX + username;
|
||||
SaTokenDao dao = SaManager.getSaTokenDao();
|
||||
|
||||
// 1. 先从缓存获取
|
||||
List<String> permissionList = (List<String>) dao.getObject(cacheKey);
|
||||
|
||||
if (permissionList == null) {
|
||||
// 2. 缓存未命中,查询数据库
|
||||
log.warn("权限缓存未命中,查询数据库 [ username={} ]", username);
|
||||
|
||||
String userId = commonApi.getUserIdByName(username);
|
||||
Set<String> permissionSet = commonApi.queryUserAuths(userId);
|
||||
permissionList = new ArrayList<>(permissionSet);
|
||||
|
||||
// 3. 将结果缓存起来
|
||||
dao.setObject(cacheKey, permissionList, CACHE_TIMEOUT);
|
||||
}
|
||||
|
||||
return permissionList;
|
||||
}
|
||||
|
||||
@Override
|
||||
public List<String> getRoleList(Object loginId, String loginType) {
|
||||
// 实现类似 getPermissionList(),使用 ROLE_CACHE_PREFIX
|
||||
// 详见:StpInterfaceImpl.java
|
||||
}
|
||||
|
||||
// 清除缓存的静态方法
|
||||
public static void clearUserCache(List<String> usernameList) {
|
||||
SaTokenDao dao = SaManager.getSaTokenDao();
|
||||
for (String username : usernameList) {
|
||||
dao.deleteObject(PERMISSION_CACHE_PREFIX + username);
|
||||
dao.deleteObject(ROLE_CACHE_PREFIX + username);
|
||||
}
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
**⚠️ 关键:** Sa-Token 的 `StpInterface` **不提供自动缓存**,必须手动实现,否则每次请求都会查询数据库!
|
||||
|
||||
### 2.3 Filter 配置(支持 URL 参数传递 token)
|
||||
|
||||
```java
|
||||
@Bean
|
||||
@Primary
|
||||
public StpLogic getStpLogicJwt() {
|
||||
return new StpLogicJwtForSimple() {
|
||||
@Override
|
||||
public String getTokenValue() {
|
||||
SaRequest request = SaHolder.getRequest();
|
||||
|
||||
// 优先级:Header > URL参数"token" > URL参数"X-Access-Token"
|
||||
String tokenValue = request.getHeader(getConfigOrGlobal().getTokenName());
|
||||
if (isEmpty(tokenValue)) {
|
||||
tokenValue = request.getParam("token"); // 兼容 WebSocket、积木报表
|
||||
}
|
||||
if (isEmpty(tokenValue)) {
|
||||
tokenValue = request.getParam(getConfigOrGlobal().getTokenName());
|
||||
}
|
||||
|
||||
return isEmpty(tokenValue) ? super.getTokenValue() : tokenValue;
|
||||
}
|
||||
};
|
||||
}
|
||||
|
||||
@Bean
|
||||
public SaServletFilter getSaServletFilter() {
|
||||
return new SaServletFilter()
|
||||
.addInclude("/**")
|
||||
.setExcludeList(getExcludeUrls()) // 排除登录、静态资源等
|
||||
.setAuth(obj -> {
|
||||
// 检查是否是免认证路径
|
||||
String servletPath = SaHolder.getRequest().getRequestPath();
|
||||
if (InMemoryIgnoreAuth.contains(servletPath)) {
|
||||
return;
|
||||
}
|
||||
|
||||
// ⚠️ 关键:如果请求带 token,先切换到对应的登录会话
|
||||
try {
|
||||
String token = StpUtil.getTokenValue();
|
||||
if (isNotEmpty(token)) {
|
||||
Object loginId = StpUtil.getLoginIdByToken(token);
|
||||
if (loginId != null) {
|
||||
StpUtil.switchTo(loginId); // 切换登录会话
|
||||
}
|
||||
}
|
||||
} catch (Exception e) {
|
||||
log.debug("切换登录会话失败: {}", e.getMessage());
|
||||
}
|
||||
|
||||
// 最终校验登录状态
|
||||
StpUtil.checkLogin();
|
||||
})
|
||||
.setError(e -> {
|
||||
// 返回401 JSON响应
|
||||
SaHolder.getResponse()
|
||||
.setStatus(401)
|
||||
.setHeader("Content-Type", "application/json;charset=UTF-8");
|
||||
return JwtUtil.responseErrorJson(401, "Token失效,请重新登录!");
|
||||
});
|
||||
}
|
||||
```
|
||||
|
||||
### 2.4 全局异常处理
|
||||
|
||||
```java
|
||||
@ExceptionHandler(NotLoginException.class)
|
||||
public Result<?> handleNotLoginException(NotLoginException e) {
|
||||
log.warn("用户未登录或Token失效: {}", e.getMessage());
|
||||
return Result.error(401, "Token失效,请重新登录!");
|
||||
}
|
||||
|
||||
@ExceptionHandler(NotPermissionException.class)
|
||||
public Result<?> handleNotPermissionException(NotPermissionException e) {
|
||||
log.warn("权限不足: {}", e.getMessage());
|
||||
return Result.error(403, "用户权限不足,无法访问!");
|
||||
}
|
||||
```
|
||||
|
||||
---
|
||||
|
||||
## 🔄 3. API 迁移对照表
|
||||
|
||||
### 3.1 注解替换
|
||||
|
||||
| Shiro | Sa-Token | 说明 |
|
||||
|-------|----------|------|
|
||||
| `@RequiresPermissions("user:add")` | `@SaCheckPermission("user:add")` | 权限校验 |
|
||||
| `@RequiresRoles("admin")` | `@SaCheckRole("admin")` | 角色校验 |
|
||||
|
||||
### 3.2 API 替换
|
||||
|
||||
| Shiro | Sa-Token | 说明 |
|
||||
|-------|----------|------|
|
||||
| `SecurityUtils.getSubject().getPrincipal()` | `LoginUserUtils.getSessionUser()` | 获取登录用户 |
|
||||
| `Subject.login(token)` | `LoginUserUtils.doLogin(sysUser)` | 登录(推荐) |
|
||||
| `Subject.login(token)` | `StpUtil.login(username)` | 登录(底层API) |
|
||||
| `Subject.logout()` | `StpUtil.logout()` | 退出登录 |
|
||||
| `Subject.isAuthenticated()` | `StpUtil.isLogin()` | 判断是否登录 |
|
||||
| `Subject.hasRole("admin")` | `StpUtil.hasRole("admin")` | 判断角色 |
|
||||
| `Subject.isPermitted("user:add")` | `StpUtil.hasPermission("user:add")` | 判断权限 |
|
||||
|
||||
---
|
||||
|
||||
## ⚠️ 4. 重要特性说明
|
||||
|
||||
### 4.1 JWT-Simple 模式特性
|
||||
|
||||
- ✅ **生成标准 JWT token**:与原 Shiro JWT 格式完全兼容
|
||||
- ✅ **仍然检查 Redis Session**:支持强制退出(与纯 JWT 无状态模式不同)
|
||||
- ✅ **支持 URL 参数传递**:兼容 WebSocket、积木报表等场景
|
||||
- ⚠️ **非完全无状态**:依赖 Redis 存储会话和权限缓存
|
||||
|
||||
### 4.2 Session 数据优化
|
||||
|
||||
`LoginUserUtils.setSessionUser()` 会自动清除以下字段:
|
||||
|
||||
```
|
||||
password, workNo, birthday, sex, email, phone, status,
|
||||
delFlag, activitiSync, createTime, userIdentity, post,
|
||||
telephone, clientId, mainDepPostId
|
||||
```
|
||||
|
||||
**优势:**
|
||||
- 减少 Redis 存储约 **50%**
|
||||
- 密码不再存储在 Session 中,**安全性提升**
|
||||
|
||||
### 4.3 权限缓存动态更新
|
||||
|
||||
修改角色权限后,系统会自动清除受影响用户的权限缓存:
|
||||
|
||||
```java
|
||||
// SysPermissionController.saveRolePermission() 中
|
||||
@RequestMapping(value = "/saveRolePermission", method = RequestMethod.POST)
|
||||
public Result<String> saveRolePermission(@RequestBody JSONObject json) {
|
||||
String roleId = json.getString("roleId");
|
||||
String permissionIds = json.getString("permissionIds");
|
||||
String lastPermissionIds = json.getString("lastpermissionIds");
|
||||
|
||||
// 保存角色权限关系
|
||||
sysRolePermissionService.saveRolePermission(roleId, permissionIds, lastPermissionIds);
|
||||
|
||||
// ⚠️ 关键:清除拥有该角色的所有用户的权限缓存
|
||||
clearRolePermissionCache(roleId);
|
||||
|
||||
return Result.ok("保存成功!");
|
||||
}
|
||||
|
||||
// 实现:查询该角色下的所有用户,批量清除缓存
|
||||
private void clearRolePermissionCache(String roleId) {
|
||||
List<String> usernameList = new ArrayList<>();
|
||||
|
||||
// 分页查询拥有该角色的用户
|
||||
int pageNo = 1, pageSize = 100;
|
||||
while (true) {
|
||||
Page<SysUser> page = new Page<>(pageNo, pageSize);
|
||||
IPage<SysUser> userPage = sysUserService.getUserByRoleId(page, roleId, null, null);
|
||||
|
||||
if (userPage.getRecords().isEmpty()) break;
|
||||
|
||||
for (SysUser user : userPage.getRecords()) {
|
||||
usernameList.add(user.getUsername());
|
||||
}
|
||||
|
||||
if (pageNo >= userPage.getPages()) break;
|
||||
pageNo++;
|
||||
}
|
||||
|
||||
// 批量清除用户权限和角色缓存
|
||||
if (!usernameList.isEmpty()) {
|
||||
StpInterfaceImpl.clearUserCache(usernameList);
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
**结果:** 权限变更立即生效,用户无需重新登录。
|
||||
|
||||
|
||||
## ✅ 6. 测试清单
|
||||
|
||||
### 6.1 登录功能测试
|
||||
|
||||
| 测试项 | 测试状态 | 说明 |
|
||||
|--------|---------|------|
|
||||
| 账号密码登录 | ✅ 通过 | 验证 `/sys/login` 接口 |
|
||||
| 手机号登录 | ✅ 通过 | 验证 `/sys/phoneLogin` 接口 |
|
||||
| APP 登录 | ✅ 通过 | 验证 APP 端登录流程 |
|
||||
| 扫码登录 | ✅ 通过 | 验证二维码扫码登录 |
|
||||
| 第三方登录 | ⏳ 待测试 | 微信、QQ 等第三方登录 |
|
||||
| 钉钉 OAuth2.0 登录 | ⏳ 待测试 | 钉钉授权登录流程 |
|
||||
| 企业微信 OAuth2.0 登录 | ⏳ 待测试 | 企业微信授权登录流程 |
|
||||
| CAS 单点登录 | ⏳ 待测试 | CAS 单点登录集成 |
|
||||
|
||||
### 6.2 核心功能测试
|
||||
|
||||
| 测试项 | 测试状态 | 说明 |
|
||||
|--------|---------|------|
|
||||
| Token 权限拦截 | ✅ 通过 | 无 token 或失效 token 返回 401 |
|
||||
| 权限注解 `@SaCheckPermission` | ✅ 通过 | 无权限返回 403 |
|
||||
| 角色注解 `@SaCheckRole` | ✅ 通过 | 无角色返回 403 |
|
||||
| `@IgnoreAuth` 免认证 | ✅ 通过 | 无 token 也能正常访问 |
|
||||
| 自动续期(操作不掉线) | ✅ 通过 | 活跃用户 token 自动续期 |
|
||||
| 用户权限变更即刻生效 | ✅ 通过 | 修改角色权限后无需重新登录 |
|
||||
| 积木报表 token 参数模式 | ✅ 通过 | `/jmreport/**?token=xxx` 正常访问 |
|
||||
|
||||
### 6.3 异步和网关测试
|
||||
|
||||
| 测试项 | 测试状态 | 说明 |
|
||||
|--------|---------|------|
|
||||
| 异步接口(`@Async`) | ❌ 有问题 | **需排查:异步线程中获取登录用户失败** |
|
||||
| Gateway 模式权限验证 | ⏳ 待测试 | 网关模式下的权限拦截 |
|
||||
|
||||
### 6.4 多租户测试
|
||||
|
||||
| 测试项 | 测试状态 | 说明 |
|
||||
|--------|---------|------|
|
||||
| 租户 ID 校验 | ⚠️ 缺失 | **需补充:校验用户 tenant_id 和前端传参一致性** |
|
||||
|
||||
### 6.5 测试说明
|
||||
|
||||
**✅ 通过** - 功能正常,符合预期
|
||||
**❌ 有问题** - 功能异常,需要修复
|
||||
**⏳ 待测试** - 尚未测试
|
||||
**⚠️ 缺失** - 功能缺失,需要补充
|
||||
|
||||
|
||||
---
|
||||
|
||||
## 📊 7. 迁移总结
|
||||
|
||||
| 优化项 | 说明 | 收益 |
|
||||
|--------|------|------|
|
||||
| **loginId 设计** | 使用 `username` 而非 `userId` | 语义清晰,与业务逻辑一致 |
|
||||
| **Session 优化** | 清除 15 个不必要字段 | Redis 存储减少 50%,安全性提升 |
|
||||
| **权限缓存** | 手动实现 30 天缓存 | 性能提升 99%,降低 DB 压力 |
|
||||
| **权限实时更新** | 角色权限修改后自动清除缓存 | 无需重新登录即生效 |
|
||||
| **URL Token 支持** | Filter 中实现 `switchTo` | 兼容 WebSocket、积木报表等场景 |
|
||||
| **JWT 兼容** | JWT-Simple 模式 | 完全兼容原 JWT token 格式 |
|
||||
|
||||
---
|
||||
|
||||
## 📚 参考资料
|
||||
|
||||
- [Sa-Token 官方文档](https://sa-token.cc/)
|
||||
- [Sa-Token JWT-Simple 模式](https://sa-token.cc/doc.html#/plugin/jwt-extend)
|
||||
- [Sa-Token 权限缓存最佳实践](https://sa-token.cc/doc.html#/fun/jur-cache)
|
||||
Binary file not shown.
File diff suppressed because one or more lines are too long
@ -12,7 +12,7 @@
|
||||
Target Server Version : 130003 (130003)
|
||||
File Encoding : 65001
|
||||
|
||||
Date: 28/11/2025 10:57:57
|
||||
Date: 02/12/2025 12:17:13
|
||||
*/
|
||||
|
||||
|
||||
@ -1592,6 +1592,7 @@ INSERT INTO "public"."flyway_schema_history" VALUES (8, '3.8.3.1', 'upgrade jimu
|
||||
INSERT INTO "public"."flyway_schema_history" VALUES (9, '3.9.0.0', 'all upgrade', 'SQL', 'V3.9.0_0__all_upgrade.sql', -758666487, 'root', '2025-11-26 13:40:20', 48, 1);
|
||||
INSERT INTO "public"."flyway_schema_history" VALUES (10, '3.9.0.1', 'mcp demo', 'SQL', 'V3.9.0_1__mcp_demo.sql', -790563395, 'root', '2025-11-27 18:16:00', 18, 1);
|
||||
INSERT INTO "public"."flyway_schema_history" VALUES (11, '3.9.0.2', 'upd dep category', 'SQL', 'V3.9.0_2__upd_dep_category.sql', -71250240, 'root', '2025-11-27 18:45:48', 19, 1);
|
||||
INSERT INTO "public"."flyway_schema_history" VALUES (12, '3.9.0.3', 'add aiflow permission', 'SQL', 'V3.9.0_3__add_aiflow_permission.sql', 1502182637, 'root', '2025-12-01 15:13:59', 9, 1);
|
||||
|
||||
-- ----------------------------
|
||||
-- Table structure for jeecg_order_customer
|
||||
@ -23122,6 +23123,15 @@ INSERT INTO "public"."sys_log" VALUES ('1993993270212014081', 1, '用户名: 管
|
||||
INSERT INTO "public"."sys_log" VALUES ('1993993307381936129', 1, '用户名: admin,登录成功!', NULL, 'admin', '管理员', '0:0:0:0:0:0:0:1', NULL, NULL, NULL, NULL, NULL, NULL, '2025-11-27 18:40:26', NULL, NULL, NULL, 'pc');
|
||||
INSERT INTO "public"."sys_log" VALUES ('1994221554447179778', 1, '用户名: 管理员,退出成功!', NULL, 'admin', '管理员', '127.0.0.1', NULL, NULL, NULL, NULL, NULL, NULL, '2025-11-28 09:47:24', NULL, NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_log" VALUES ('1994221985936203777', 1, '用户名: admin,登录成功!', NULL, 'admin', '管理员', '0:0:0:0:0:0:0:1', NULL, NULL, NULL, NULL, NULL, NULL, '2025-11-28 09:49:07', NULL, NULL, NULL, 'pc');
|
||||
INSERT INTO "public"."sys_log" VALUES ('1994302211463241729', 1, '用户名: admin,登录成功!', NULL, 'admin', '管理员', '172.28.208.1', NULL, NULL, NULL, NULL, NULL, NULL, '2025-11-28 15:07:54', NULL, NULL, NULL, 'pc');
|
||||
INSERT INTO "public"."sys_log" VALUES ('1995371606017015810', 1, '用户名: admin,登录成功!', NULL, 'admin', '管理员', '0:0:0:0:0:0:0:1', NULL, NULL, NULL, NULL, NULL, NULL, '2025-12-01 13:57:18', NULL, NULL, NULL, 'pc');
|
||||
INSERT INTO "public"."sys_log" VALUES ('1995371961282953217', 2, '职务表-分页列表查询', 1, 'admin', '管理员', '0:0:0:0:0:0:0:1', 'org.jeecg.modules.system.controller.SysPositionController.queryPageList()', NULL, ' sysPosition: SysPosition(id=null, code=null, name=null, postLevel=null, companyId=null, createBy=null, createTime=null, updateBy=null, updateTime=null, sysOrgCode=null, tenantId=null) pageNo: 1 pageSize: 10 req: org.springframework.web.servlet.resource.ResourceUrlEncodingFilter$ResourceUrlEncodingRequestWrapper@13d8a219', NULL, 22, NULL, '2025-12-01 13:58:42', NULL, NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_log" VALUES ('1995373087231307777', 1, '用户名: 管理员,退出成功!', NULL, 'admin', '管理员', '127.0.0.1', NULL, NULL, NULL, NULL, NULL, NULL, '2025-12-01 14:03:11', NULL, NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_log" VALUES ('1995373105824657409', 1, '用户名: admin,登录成功!', NULL, 'admin', '管理员', '0:0:0:0:0:0:0:1', NULL, NULL, NULL, NULL, NULL, NULL, '2025-12-01 14:03:15', NULL, NULL, NULL, 'pc');
|
||||
INSERT INTO "public"."sys_log" VALUES ('1995373168957321217', 1, '用户名: admin,登录成功!', NULL, 'admin', '管理员', '0:0:0:0:0:0:0:1', NULL, NULL, NULL, NULL, NULL, NULL, '2025-12-01 14:03:30', NULL, NULL, NULL, 'pc');
|
||||
INSERT INTO "public"."sys_log" VALUES ('1995391198043041794', 2, '修改角色ID: 1501570619841810433 的权限配置,操作人: admin', 2, 'admin', '管理员', '0:0:0:0:0:0:0:1', NULL, NULL, NULL, NULL, NULL, NULL, '2025-12-01 15:15:09', NULL, NULL, NULL, 'pc');
|
||||
INSERT INTO "public"."sys_log" VALUES ('1995391279496425474', 2, '修改角色ID: f6817f48af4fb3af11b9e8bf182f618b 的权限配置,操作人: admin', 2, 'admin', '管理员', '0:0:0:0:0:0:0:1', NULL, NULL, NULL, NULL, NULL, NULL, '2025-12-01 15:15:28', NULL, NULL, NULL, 'pc');
|
||||
INSERT INTO "public"."sys_log" VALUES ('1995391337268768770', 2, '修改角色ID: f6817f48af4fb3af11b9e8bf182f618b 的权限配置,操作人: admin', 2, 'admin', '管理员', '0:0:0:0:0:0:0:1', NULL, NULL, NULL, NULL, NULL, NULL, '2025-12-01 15:15:42', NULL, NULL, NULL, 'pc');
|
||||
|
||||
-- ----------------------------
|
||||
-- Table structure for sys_permission
|
||||
@ -23599,6 +23609,7 @@ INSERT INTO "public"."sys_permission" VALUES ('1930222679269376001', '1892553778
|
||||
INSERT INTO "public"."sys_permission" VALUES ('1930222862556266498', '1890213291321749505', '新增AI流程', NULL, NULL, 0, NULL, NULL, 2, 'airag:flow:add', '1', NULL, 0, NULL, 1, 0, 0, 0, NULL, 'admin', '2025-06-04 19:19:27', 'admin', '2025-06-04 19:21:08', 0, 0, '1', 0);
|
||||
INSERT INTO "public"."sys_permission" VALUES ('1930222953853681666', '1890213291321749505', '编辑AI流程', NULL, NULL, 0, NULL, NULL, 2, 'airag:flow:edit', '1', NULL, 0, NULL, 1, 0, 0, 0, NULL, 'admin', '2025-06-04 19:19:49', NULL, NULL, 0, 0, '1', 0);
|
||||
INSERT INTO "public"."sys_permission" VALUES ('1930223034757611522', '1890213291321749505', '保存AI流程设计', NULL, NULL, 0, NULL, NULL, 2, 'airag:flow:designSave', '1', NULL, 0, NULL, 1, 0, 0, 0, NULL, 'admin', '2025-06-04 19:20:08', NULL, NULL, 0, 0, '1', 0);
|
||||
INSERT INTO "public"."sys_permission" VALUES ('1930223114757611522', '1890213291321749505', 'AI流程测试', NULL, NULL, 0, NULL, NULL, 2, 'airag:flow:debug', '1', NULL, 0, NULL, 1, 0, 0, 0, NULL, 'admin', '2025-12-01 19:20:08', NULL, NULL, 0, 0, '1', 0);
|
||||
INSERT INTO "public"."sys_permission" VALUES ('1930223132619112449', '1890213291321749505', '删除AI流程', NULL, NULL, 0, NULL, NULL, 2, 'airag:flow:delete', '1', NULL, 0, NULL, 1, 0, 0, 0, NULL, 'admin', '2025-06-04 19:20:31', NULL, NULL, 0, 0, '1', 0);
|
||||
INSERT INTO "public"."sys_permission" VALUES ('1939572818833301506', 'd7d6e2e4e2934f2c9385a623fd98c6f3', '首页配置', '/system/homeConfig', 'system/homeConfig/index', 1, '', NULL, 1, NULL, '0', 1, 0, 'ant-design:appstore-outlined', 0, 0, 0, 0, NULL, 'admin', '2025-06-30 14:32:50', 'admin', '2025-07-01 20:13:22', 0, 0, NULL, 0);
|
||||
INSERT INTO "public"."sys_permission" VALUES ('1941349246536998913', '1939572818833301506', '首页配置-添加', NULL, NULL, 0, NULL, NULL, 2, 'system:roleindex:add', '1', NULL, 0, NULL, 1, 0, 0, 0, NULL, 'admin', '2025-07-05 12:11:44', NULL, NULL, 0, 0, '1', 0);
|
||||
@ -24331,7 +24342,7 @@ INSERT INTO "public"."sys_role_permission" VALUES ('1693199779570098187', 'f6817
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1693199779570098188', 'f6817f48af4fb3af11b9e8bf182f618b', '1438108176932265985', NULL, '2023-08-20 17:54:20', '127.0.0.1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1693199779570098189', 'f6817f48af4fb3af11b9e8bf182f618b', '1438108178421243905', NULL, '2023-08-20 17:54:20', '127.0.0.1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1693199779570098190', 'f6817f48af4fb3af11b9e8bf182f618b', '1438108188034588674', NULL, '2023-08-20 17:54:20', '127.0.0.1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780756140032', '496138616573952', '56911328312299520', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780441567232', '496138616573952', '76216264070008832', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1693199779570098191', 'f6817f48af4fb3af11b9e8bf182f618b', '1438108189754253313', NULL, '2023-08-20 17:54:20', '127.0.0.1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1693199779578486786', 'f6817f48af4fb3af11b9e8bf182f618b', '1438108195487866881', NULL, '2023-08-20 17:54:20', '127.0.0.1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1693199779578486787', 'f6817f48af4fb3af11b9e8bf182f618b', '1438108196855209985', NULL, '2023-08-20 17:54:20', '127.0.0.1');
|
||||
@ -24393,7 +24404,7 @@ INSERT INTO "public"."sys_role_permission" VALUES ('1693199779595264016', 'f6817
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1693199779595264017', 'f6817f48af4fb3af11b9e8bf182f618b', '1438108204576923649', NULL, '2023-08-20 17:54:20', '127.0.0.1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1693199779595264018', 'f6817f48af4fb3af11b9e8bf182f618b', '1438108206086873089', NULL, '2023-08-20 17:54:20', '127.0.0.1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1693199779603652610', 'f6817f48af4fb3af11b9e8bf182f618b', '1439542701152575489', NULL, '2023-08-20 17:54:20', '127.0.0.1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780764528640', '496138616573952', '41378916912336896', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780449955840', '496138616573952', '76216459709124608', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1693199779603652611', 'f6817f48af4fb3af11b9e8bf182f618b', '1580877743141933058', NULL, '2023-08-20 17:54:20', '127.0.0.1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1693199779603652612', 'f6817f48af4fb3af11b9e8bf182f618b', '1438108179381739521', NULL, '2023-08-20 17:54:20', '127.0.0.1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1693199779603652613', 'f6817f48af4fb3af11b9e8bf182f618b', '1438108197958311677', NULL, '2023-08-20 17:54:20', '127.0.0.1');
|
||||
@ -24455,7 +24466,7 @@ INSERT INTO "public"."sys_role_permission" VALUES ('1693199779624624144', 'f6817
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1693199779624624145', 'f6817f48af4fb3af11b9e8bf182f618b', '1438108201150177281', NULL, '2023-08-20 17:54:20', '127.0.0.1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1693199779624624146', 'f6817f48af4fb3af11b9e8bf182f618b', '1438108201502498817', NULL, '2023-08-20 17:54:20', '127.0.0.1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1693199779624624147', 'f6817f48af4fb3af11b9e8bf182f618b', '1438108183395688450', NULL, '2023-08-20 17:54:20', '127.0.0.1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780768722944', '496138616573952', '63482475359244288', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780458344448', '496138616573952', '76216594207870976', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1693199779624624148', 'f6817f48af4fb3af11b9e8bf182f618b', '1438108178010202113', NULL, '2023-08-20 17:54:20', '127.0.0.1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1693199779633012738', 'f6817f48af4fb3af11b9e8bf182f618b', '1438108183492157442', NULL, '2023-08-20 17:54:20', '127.0.0.1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1693199779633012739', 'f6817f48af4fb3af11b9e8bf182f618b', '1438108202060341249', NULL, '2023-08-20 17:54:20', '127.0.0.1');
|
||||
@ -24770,6 +24781,26 @@ INSERT INTO "public"."sys_role_permission" VALUES ('1993532192269012993', '15015
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1993532373655883778', '1501570619841810433', '1972617196420993025', NULL, '2025-11-26 12:08:51', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1993532463099416577', 'f6817f48af4fb3af11b9e8bf182f618b', '1972617196420993025', NULL, '2025-11-26 12:09:12', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1993532463099416578', 'f6817f48af4fb3af11b9e8bf182f618b', '1972645086223814657', NULL, '2025-11-26 12:09:12', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1995391197980127234', '1501570619841810433', '1930223114757611522', NULL, '2025-12-01 15:15:09', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1995391279299293186', 'f6817f48af4fb3af11b9e8bf182f618b', '1930222862556266498', NULL, '2025-12-01 15:15:28', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1995391279299293187', 'f6817f48af4fb3af11b9e8bf182f618b', '1930222953853681666', NULL, '2025-12-01 15:15:28', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1995391279299293188', 'f6817f48af4fb3af11b9e8bf182f618b', '1930223034757611522', NULL, '2025-12-01 15:15:28', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1995391279299293189', 'f6817f48af4fb3af11b9e8bf182f618b', '1930223114757611522', NULL, '2025-12-01 15:15:28', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1995391279299293190', 'f6817f48af4fb3af11b9e8bf182f618b', '1930223132619112449', NULL, '2025-12-01 15:15:28', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1995391279362207745', 'f6817f48af4fb3af11b9e8bf182f618b', '1930222295012409345', NULL, '2025-12-01 15:15:28', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1995391279362207746', 'f6817f48af4fb3af11b9e8bf182f618b', '1930222395180777474', NULL, '2025-12-01 15:15:28', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1995391279362207747', 'f6817f48af4fb3af11b9e8bf182f618b', '1930222218734796802', NULL, '2025-12-01 15:15:28', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1995391279362207748', 'f6817f48af4fb3af11b9e8bf182f618b', '1930222066120851457', NULL, '2025-12-01 15:15:28', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1995391279362207749', 'f6817f48af4fb3af11b9e8bf182f618b', '1930221983555977217', NULL, '2025-12-01 15:15:28', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1995391279362207750', 'f6817f48af4fb3af11b9e8bf182f618b', '1930221774230847490', NULL, '2025-12-01 15:15:28', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1995391279362207751', 'f6817f48af4fb3af11b9e8bf182f618b', '1930221702164316161', NULL, '2025-12-01 15:15:28', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1995391279362207752', 'f6817f48af4fb3af11b9e8bf182f618b', '1930221637551063042', NULL, '2025-12-01 15:15:28', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1995391279362207753', 'f6817f48af4fb3af11b9e8bf182f618b', '1930221570324758530', NULL, '2025-12-01 15:15:28', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1995391337201659906', 'f6817f48af4fb3af11b9e8bf182f618b', '1930221213607591937', NULL, '2025-12-01 15:15:42', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1995391337201659907', 'f6817f48af4fb3af11b9e8bf182f618b', '1930221335938662401', NULL, '2025-12-01 15:15:42', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1995391337201659908', 'f6817f48af4fb3af11b9e8bf182f618b', '1930222679269376001', NULL, '2025-12-01 15:15:42', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1995391337201659909', 'f6817f48af4fb3af11b9e8bf182f618b', '1930222617197871105', NULL, '2025-12-01 15:15:42', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1995391337201659910', 'f6817f48af4fb3af11b9e8bf182f618b', '1930222558582472705', NULL, '2025-12-01 15:15:42', '0:0:0:0:0:0:0:1');
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1ac1688ef8456f384091a03d88a89ab1', '52b0cf022ac4187b2a70dfa4f8b2d940', '693ce69af3432bd00be13c3971a57961', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1af4babaa4227c3cbb830bc5eb513abb', 'ee8626f80f7c2619917b6236f3a7f02b', 'e08cb190ef230d5d4f03824198773950', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('1ba162bbc2076c25561f8622f610d5bf', 'ee8626f80f7c2619917b6236f3a7f02b', 'aedbf679b5773c1f25e9f7b10111da73', NULL, NULL, NULL);
|
||||
@ -24790,7 +24821,6 @@ INSERT INTO "public"."sys_role_permission" VALUES ('37112f4d372541e105473f18da3d
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('37789f70cd8bd802c4a69e9e1f633eaa', 'ee8626f80f7c2619917b6236f3a7f02b', 'ae4fed059f67086fd52a73d913cf473d', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('381504a717cb3ce77dcd4070c9689a7e', 'ee8626f80f7c2619917b6236f3a7f02b', '4f84f9400e5e92c95f05b554724c2b58', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('3e563751942b0879c88ca4de19757b50', '1750a8fb3e6d90cb7957c02de1dc8e59', '58857ff846e61794c69208e9d3a85466', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780772917249', '496138616573952', '64290663792906240', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('412e2de37a35b3442d68db8dd2f3c190', '52b0cf022ac4187b2a70dfa4f8b2d940', 'f1cb187abf927c88b89470d08615f5ac', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('4204f91fb61911ba8ce40afa7c02369f', 'f6817f48af4fb3af11b9e8bf182f618b', '3f915b2769fc80648e92d04e84ca059d', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('44b5a73541bcb854dd5d38c6d1fb93a1', 'ee8626f80f7c2619917b6236f3a7f02b', '418964ba087b90a84897b62474496b93', NULL, NULL, NULL);
|
||||
@ -24851,9 +24881,6 @@ INSERT INTO "public"."sys_role_permission" VALUES ('77277780412207104', '4961386
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780420595712', '496138616573952', '75002207560273920', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780428984320', '496138616573952', '76215889006956544', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780433178624', '496138616573952', '76216071333351424', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780441567232', '496138616573952', '76216264070008832', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780449955840', '496138616573952', '76216459709124608', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780458344448', '496138616573952', '76216594207870976', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780466733056', '496138616573952', '76216702639017984', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780475121664', '496138616573952', '58480609315524608', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780483510272', '496138616573952', '61394706252173312', NULL, NULL, NULL);
|
||||
@ -24881,6 +24908,10 @@ INSERT INTO "public"."sys_role_permission" VALUES ('77277780722585600', '4961386
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780730974208', '496138616573952', '42082442672082944', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780739362816', '496138616573952', '41376192166629376', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780747751424', '496138616573952', '41377034236071936', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780756140032', '496138616573952', '56911328312299520', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780764528640', '496138616573952', '41378916912336896', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780768722944', '496138616573952', '63482475359244288', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780772917249', '496138616573952', '64290663792906240', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780785500160', '496138616573952', '66790433014943744', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780789694464', '496138616573952', '42087054753927168', NULL, NULL, NULL);
|
||||
INSERT INTO "public"."sys_role_permission" VALUES ('77277780798083072', '496138616573952', '67027338952445952', NULL, NULL, NULL);
|
||||
|
||||
@ -12,7 +12,7 @@
|
||||
Target Server Version : 15004188 (15.00.4188)
|
||||
File Encoding : 65001
|
||||
|
||||
Date: 28/11/2025 10:24:13
|
||||
Date: 02/12/2025 12:11:34
|
||||
*/
|
||||
|
||||
|
||||
@ -2473,6 +2473,9 @@ GO
|
||||
INSERT INTO [dbo].[flyway_schema_history] ([installed_rank], [version], [description], [type], [script], [checksum], [installed_by], [installed_on], [execution_time], [success]) VALUES (N'11', N'3.9.0.2', N'upd dep category', N'SQL', N'V3.9.0_2__upd_dep_category.sql', N'-71250240', N'root', N'2025-11-27 18:45:48.0000000', N'19', N'1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[flyway_schema_history] ([installed_rank], [version], [description], [type], [script], [checksum], [installed_by], [installed_on], [execution_time], [success]) VALUES (N'12', N'3.9.0.3', N'add aiflow permission', N'SQL', N'V3.9.0_3__add_aiflow_permission.sql', N'1502182637', N'root', N'2025-12-01 15:13:59.0000000', N'9', N'1')
|
||||
GO
|
||||
|
||||
|
||||
-- ----------------------------
|
||||
-- Table structure for jeecg_order_customer
|
||||
@ -39310,6 +39313,33 @@ GO
|
||||
INSERT INTO [dbo].[sys_log] ([id], [log_type], [log_content], [operate_type], [userid], [username], [ip], [method], [request_url], [request_param], [request_type], [cost_time], [create_by], [create_time], [update_by], [update_time], [tenant_id], [client_type]) VALUES (N'1994221985936203777', N'1', N'用户名: admin,登录成功!', NULL, N'admin', N'管理员', N'0:0:0:0:0:0:0:1', NULL, NULL, NULL, NULL, NULL, NULL, N'2025-11-28 09:49:07.0000000', NULL, NULL, NULL, N'pc')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_log] ([id], [log_type], [log_content], [operate_type], [userid], [username], [ip], [method], [request_url], [request_param], [request_type], [cost_time], [create_by], [create_time], [update_by], [update_time], [tenant_id], [client_type]) VALUES (N'1994302211463241729', N'1', N'用户名: admin,登录成功!', NULL, N'admin', N'管理员', N'172.28.208.1', NULL, NULL, NULL, NULL, NULL, NULL, N'2025-11-28 15:07:54.0000000', NULL, NULL, NULL, N'pc')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_log] ([id], [log_type], [log_content], [operate_type], [userid], [username], [ip], [method], [request_url], [request_param], [request_type], [cost_time], [create_by], [create_time], [update_by], [update_time], [tenant_id], [client_type]) VALUES (N'1995371606017015810', N'1', N'用户名: admin,登录成功!', NULL, N'admin', N'管理员', N'0:0:0:0:0:0:0:1', NULL, NULL, NULL, NULL, NULL, NULL, N'2025-12-01 13:57:18.0000000', NULL, NULL, NULL, N'pc')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_log] ([id], [log_type], [log_content], [operate_type], [userid], [username], [ip], [method], [request_url], [request_param], [request_type], [cost_time], [create_by], [create_time], [update_by], [update_time], [tenant_id], [client_type]) VALUES (N'1995371961282953217', N'2', N'职务表-分页列表查询', N'1', N'admin', N'管理员', N'0:0:0:0:0:0:0:1', N'org.jeecg.modules.system.controller.SysPositionController.queryPageList()', NULL, N' sysPosition: SysPosition(id=null, code=null, name=null, postLevel=null, companyId=null, createBy=null, createTime=null, updateBy=null, updateTime=null, sysOrgCode=null, tenantId=null) pageNo: 1 pageSize: 10 req: org.springframework.web.servlet.resource.ResourceUrlEncodingFilter$ResourceUrlEncodingRequestWrapper@13d8a219', NULL, N'22', NULL, N'2025-12-01 13:58:42.0000000', NULL, NULL, NULL, NULL)
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_log] ([id], [log_type], [log_content], [operate_type], [userid], [username], [ip], [method], [request_url], [request_param], [request_type], [cost_time], [create_by], [create_time], [update_by], [update_time], [tenant_id], [client_type]) VALUES (N'1995373087231307777', N'1', N'用户名: 管理员,退出成功!', NULL, N'admin', N'管理员', N'127.0.0.1', NULL, NULL, NULL, NULL, NULL, NULL, N'2025-12-01 14:03:11.0000000', NULL, NULL, NULL, NULL)
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_log] ([id], [log_type], [log_content], [operate_type], [userid], [username], [ip], [method], [request_url], [request_param], [request_type], [cost_time], [create_by], [create_time], [update_by], [update_time], [tenant_id], [client_type]) VALUES (N'1995373105824657409', N'1', N'用户名: admin,登录成功!', NULL, N'admin', N'管理员', N'0:0:0:0:0:0:0:1', NULL, NULL, NULL, NULL, NULL, NULL, N'2025-12-01 14:03:15.0000000', NULL, NULL, NULL, N'pc')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_log] ([id], [log_type], [log_content], [operate_type], [userid], [username], [ip], [method], [request_url], [request_param], [request_type], [cost_time], [create_by], [create_time], [update_by], [update_time], [tenant_id], [client_type]) VALUES (N'1995373168957321217', N'1', N'用户名: admin,登录成功!', NULL, N'admin', N'管理员', N'0:0:0:0:0:0:0:1', NULL, NULL, NULL, NULL, NULL, NULL, N'2025-12-01 14:03:30.0000000', NULL, NULL, NULL, N'pc')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_log] ([id], [log_type], [log_content], [operate_type], [userid], [username], [ip], [method], [request_url], [request_param], [request_type], [cost_time], [create_by], [create_time], [update_by], [update_time], [tenant_id], [client_type]) VALUES (N'1995391198043041794', N'2', N'修改角色ID: 1501570619841810433 的权限配置,操作人: admin', N'2', N'admin', N'管理员', N'0:0:0:0:0:0:0:1', NULL, NULL, NULL, NULL, NULL, NULL, N'2025-12-01 15:15:09.0000000', NULL, NULL, NULL, N'pc')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_log] ([id], [log_type], [log_content], [operate_type], [userid], [username], [ip], [method], [request_url], [request_param], [request_type], [cost_time], [create_by], [create_time], [update_by], [update_time], [tenant_id], [client_type]) VALUES (N'1995391279496425474', N'2', N'修改角色ID: f6817f48af4fb3af11b9e8bf182f618b 的权限配置,操作人: admin', N'2', N'admin', N'管理员', N'0:0:0:0:0:0:0:1', NULL, NULL, NULL, NULL, NULL, NULL, N'2025-12-01 15:15:28.0000000', NULL, NULL, NULL, N'pc')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_log] ([id], [log_type], [log_content], [operate_type], [userid], [username], [ip], [method], [request_url], [request_param], [request_type], [cost_time], [create_by], [create_time], [update_by], [update_time], [tenant_id], [client_type]) VALUES (N'1995391337268768770', N'2', N'修改角色ID: f6817f48af4fb3af11b9e8bf182f618b 的权限配置,操作人: admin', N'2', N'admin', N'管理员', N'0:0:0:0:0:0:0:1', NULL, NULL, NULL, NULL, NULL, NULL, N'2025-12-01 15:15:42.0000000', NULL, NULL, NULL, N'pc')
|
||||
GO
|
||||
|
||||
|
||||
-- ----------------------------
|
||||
-- Table structure for sys_permission
|
||||
@ -40781,6 +40811,9 @@ GO
|
||||
INSERT INTO [dbo].[sys_permission] ([id], [parent_id], [name], [url], [component], [is_route], [component_name], [redirect], [menu_type], [perms], [perms_type], [sort_no], [always_show], [icon], [is_leaf], [keep_alive], [hidden], [hide_tab], [description], [create_by], [create_time], [update_by], [update_time], [del_flag], [rule_flag], [status], [internal_or_external]) VALUES (N'1930223034757611522', N'1890213291321749505', N'保存AI流程设计', NULL, NULL, N'0', NULL, NULL, N'2', N'airag:flow:designSave', N'1', NULL, N'0', NULL, N'1', N'0', N'0', N'0', NULL, N'admin', N'2025-06-04 19:20:08.0000000', NULL, NULL, N'0', N'0', N'1', N'0')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_permission] ([id], [parent_id], [name], [url], [component], [is_route], [component_name], [redirect], [menu_type], [perms], [perms_type], [sort_no], [always_show], [icon], [is_leaf], [keep_alive], [hidden], [hide_tab], [description], [create_by], [create_time], [update_by], [update_time], [del_flag], [rule_flag], [status], [internal_or_external]) VALUES (N'1930223114757611522', N'1890213291321749505', N'AI流程测试', NULL, NULL, N'0', NULL, NULL, N'2', N'airag:flow:debug', N'1', NULL, N'0', NULL, N'1', N'0', N'0', N'0', NULL, N'admin', N'2025-12-01 19:20:08.0000000', NULL, NULL, N'0', N'0', N'1', N'0')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_permission] ([id], [parent_id], [name], [url], [component], [is_route], [component_name], [redirect], [menu_type], [perms], [perms_type], [sort_no], [always_show], [icon], [is_leaf], [keep_alive], [hidden], [hide_tab], [description], [create_by], [create_time], [update_by], [update_time], [del_flag], [rule_flag], [status], [internal_or_external]) VALUES (N'1930223132619112449', N'1890213291321749505', N'删除AI流程', NULL, NULL, N'0', NULL, NULL, N'2', N'airag:flow:delete', N'1', NULL, N'0', NULL, N'1', N'0', N'0', N'0', NULL, N'admin', N'2025-06-04 19:20:31.0000000', NULL, NULL, N'0', N'0', N'1', N'0')
|
||||
GO
|
||||
|
||||
@ -44297,6 +44330,66 @@ GO
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1993532463099416578', N'f6817f48af4fb3af11b9e8bf182f618b', N'1972645086223814657', NULL, N'2025-11-26 12:09:12.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1995391197980127234', N'1501570619841810433', N'1930223114757611522', NULL, N'2025-12-01 15:15:09.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1995391279299293186', N'f6817f48af4fb3af11b9e8bf182f618b', N'1930222862556266498', NULL, N'2025-12-01 15:15:28.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1995391279299293187', N'f6817f48af4fb3af11b9e8bf182f618b', N'1930222953853681666', NULL, N'2025-12-01 15:15:28.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1995391279299293188', N'f6817f48af4fb3af11b9e8bf182f618b', N'1930223034757611522', NULL, N'2025-12-01 15:15:28.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1995391279299293189', N'f6817f48af4fb3af11b9e8bf182f618b', N'1930223114757611522', NULL, N'2025-12-01 15:15:28.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1995391279299293190', N'f6817f48af4fb3af11b9e8bf182f618b', N'1930223132619112449', NULL, N'2025-12-01 15:15:28.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1995391279362207745', N'f6817f48af4fb3af11b9e8bf182f618b', N'1930222295012409345', NULL, N'2025-12-01 15:15:28.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1995391279362207746', N'f6817f48af4fb3af11b9e8bf182f618b', N'1930222395180777474', NULL, N'2025-12-01 15:15:28.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1995391279362207747', N'f6817f48af4fb3af11b9e8bf182f618b', N'1930222218734796802', NULL, N'2025-12-01 15:15:28.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1995391279362207748', N'f6817f48af4fb3af11b9e8bf182f618b', N'1930222066120851457', NULL, N'2025-12-01 15:15:28.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1995391279362207749', N'f6817f48af4fb3af11b9e8bf182f618b', N'1930221983555977217', NULL, N'2025-12-01 15:15:28.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1995391279362207750', N'f6817f48af4fb3af11b9e8bf182f618b', N'1930221774230847490', NULL, N'2025-12-01 15:15:28.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1995391279362207751', N'f6817f48af4fb3af11b9e8bf182f618b', N'1930221702164316161', NULL, N'2025-12-01 15:15:28.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1995391279362207752', N'f6817f48af4fb3af11b9e8bf182f618b', N'1930221637551063042', NULL, N'2025-12-01 15:15:28.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1995391279362207753', N'f6817f48af4fb3af11b9e8bf182f618b', N'1930221570324758530', NULL, N'2025-12-01 15:15:28.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1995391337201659906', N'f6817f48af4fb3af11b9e8bf182f618b', N'1930221213607591937', NULL, N'2025-12-01 15:15:42.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1995391337201659907', N'f6817f48af4fb3af11b9e8bf182f618b', N'1930221335938662401', NULL, N'2025-12-01 15:15:42.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1995391337201659908', N'f6817f48af4fb3af11b9e8bf182f618b', N'1930222679269376001', NULL, N'2025-12-01 15:15:42.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1995391337201659909', N'f6817f48af4fb3af11b9e8bf182f618b', N'1930222617197871105', NULL, N'2025-12-01 15:15:42.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1995391337201659910', N'f6817f48af4fb3af11b9e8bf182f618b', N'1930222558582472705', NULL, N'2025-12-01 15:15:42.0000000', N'0:0:0:0:0:0:0:1')
|
||||
GO
|
||||
|
||||
INSERT INTO [dbo].[sys_role_permission] ([id], [role_id], [permission_id], [data_rule_ids], [operate_date], [operate_ip]) VALUES (N'1ac1688ef8456f384091a03d88a89ab1', N'52b0cf022ac4187b2a70dfa4f8b2d940', N'693ce69af3432bd00be13c3971a57961', NULL, NULL, NULL)
|
||||
GO
|
||||
|
||||
@ -48086,7 +48179,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table airag_app
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[airag_app] ADD CONSTRAINT [PK__airag_ap__3213E83F894375E5] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[airag_app] ADD CONSTRAINT [PK__airag_ap__3213E83FD59E8C70] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48095,7 +48188,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table airag_flow
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[airag_flow] ADD CONSTRAINT [PK__airag_fl__3213E83FC3F22A3E] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[airag_flow] ADD CONSTRAINT [PK__airag_fl__3213E83F05F82B1F] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48104,7 +48197,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table airag_knowledge
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[airag_knowledge] ADD CONSTRAINT [PK__airag_kn__3213E83FA6545F70] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[airag_knowledge] ADD CONSTRAINT [PK__airag_kn__3213E83FF7F5053F] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48113,7 +48206,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table airag_knowledge_doc
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[airag_knowledge_doc] ADD CONSTRAINT [PK__airag_kn__3213E83F37837E84] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[airag_knowledge_doc] ADD CONSTRAINT [PK__airag_kn__3213E83F02128919] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48122,7 +48215,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table airag_mcp
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[airag_mcp] ADD CONSTRAINT [PK__airag_mc__3213E83F09237EE5] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[airag_mcp] ADD CONSTRAINT [PK__airag_mc__3213E83F18E093FB] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48131,7 +48224,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table airag_model
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[airag_model] ADD CONSTRAINT [PK__airag_mo__3213E83F8E4E192A] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[airag_model] ADD CONSTRAINT [PK__airag_mo__3213E83F0584B09A] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48140,7 +48233,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table demo
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[demo] ADD CONSTRAINT [PK__demo__3213E83F2E133723] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[demo] ADD CONSTRAINT [PK__demo__3213E83F547F3673] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48159,7 +48252,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table flyway_schema_history
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[flyway_schema_history] ADD CONSTRAINT [PK__flyway_s__A1286B1CB7C9545E] PRIMARY KEY CLUSTERED ([installed_rank])
|
||||
ALTER TABLE [dbo].[flyway_schema_history] ADD CONSTRAINT [PK__flyway_s__A1286B1CE07B6FB0] PRIMARY KEY CLUSTERED ([installed_rank])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48168,7 +48261,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table jeecg_order_customer
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[jeecg_order_customer] ADD CONSTRAINT [PK__jeecg_or__3213E83F3DB575A9] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[jeecg_order_customer] ADD CONSTRAINT [PK__jeecg_or__3213E83FABB49CBC] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48177,7 +48270,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table jeecg_order_main
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[jeecg_order_main] ADD CONSTRAINT [PK__jeecg_or__3213E83F8A9B9027] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[jeecg_order_main] ADD CONSTRAINT [PK__jeecg_or__3213E83FA30664DC] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48186,7 +48279,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table jeecg_order_ticket
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[jeecg_order_ticket] ADD CONSTRAINT [PK__jeecg_or__3213E83F1E05B90F] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[jeecg_order_ticket] ADD CONSTRAINT [PK__jeecg_or__3213E83FDEC45172] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48205,7 +48298,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table jimu_dict
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[jimu_dict] ADD CONSTRAINT [PK__jimu_dic__3213E83FD334D461] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[jimu_dict] ADD CONSTRAINT [PK__jimu_dic__3213E83F1D1298A3] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48243,7 +48336,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table jimu_dict_item
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[jimu_dict_item] ADD CONSTRAINT [PK__jimu_dic__3213E83FEAA99799] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[jimu_dict_item] ADD CONSTRAINT [PK__jimu_dic__3213E83F1A7F88D9] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48274,7 +48367,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table jimu_report
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[jimu_report] ADD CONSTRAINT [PK__jimu_rep__3213E83F6C2EDAB7] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[jimu_report] ADD CONSTRAINT [PK__jimu_rep__3213E83FC82C5844] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48283,7 +48376,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table jimu_report_category
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[jimu_report_category] ADD CONSTRAINT [PK__jimu_rep__3213E83F21183D42] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[jimu_report_category] ADD CONSTRAINT [PK__jimu_rep__3213E83FA2835298] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48308,7 +48401,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table jimu_report_data_source
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[jimu_report_data_source] ADD CONSTRAINT [PK__jimu_rep__3213E83FC3B9EAB4] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[jimu_report_data_source] ADD CONSTRAINT [PK__jimu_rep__3213E83FDA793E6A] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48339,7 +48432,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table jimu_report_db
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[jimu_report_db] ADD CONSTRAINT [PK__jimu_rep__3213E83FD1C46E5D] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[jimu_report_db] ADD CONSTRAINT [PK__jimu_rep__3213E83F9DABEC77] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48364,7 +48457,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table jimu_report_db_field
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[jimu_report_db_field] ADD CONSTRAINT [PK__jimu_rep__3213E83F94850626] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[jimu_report_db_field] ADD CONSTRAINT [PK__jimu_rep__3213E83FE5AABCE5] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48383,7 +48476,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table jimu_report_db_param
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[jimu_report_db_param] ADD CONSTRAINT [PK__jimu_rep__3213E83FF4B87E26] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[jimu_report_db_param] ADD CONSTRAINT [PK__jimu_rep__3213E83FEE928BBD] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48392,7 +48485,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table jimu_report_export_job
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[jimu_report_export_job] ADD CONSTRAINT [PK__jimu_rep__3213E83F20D1205D] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[jimu_report_export_job] ADD CONSTRAINT [PK__jimu_rep__3213E83F4B3AE7CB] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48401,7 +48494,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table jimu_report_export_log
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[jimu_report_export_log] ADD CONSTRAINT [PK__jimu_rep__3213E83FB25A2C77] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[jimu_report_export_log] ADD CONSTRAINT [PK__jimu_rep__3213E83FB3145AF5] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48410,7 +48503,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table jimu_report_icon_lib
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[jimu_report_icon_lib] ADD CONSTRAINT [PK__jimu_rep__3213E83F2702C00A] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[jimu_report_icon_lib] ADD CONSTRAINT [PK__jimu_rep__3213E83FCFCDD201] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48429,7 +48522,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table jimu_report_link
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[jimu_report_link] ADD CONSTRAINT [PK__jimu_rep__3213E83F1902BB11] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[jimu_report_link] ADD CONSTRAINT [PK__jimu_rep__3213E83F786F2A51] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48448,7 +48541,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table jimu_report_map
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[jimu_report_map] ADD CONSTRAINT [PK__jimu_rep__3213E83F7166E735] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[jimu_report_map] ADD CONSTRAINT [PK__jimu_rep__3213E83F3CA780A1] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48486,7 +48579,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table jimu_report_share
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[jimu_report_share] ADD CONSTRAINT [PK__jimu_rep__3213E83FD7B0F0F6] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[jimu_report_share] ADD CONSTRAINT [PK__jimu_rep__3213E83F45B0C400] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48495,7 +48588,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table oauth2_registered_client
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[oauth2_registered_client] ADD CONSTRAINT [PK__oauth2_r__3213E83FE0E65C91] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[oauth2_registered_client] ADD CONSTRAINT [PK__oauth2_r__3213E83FB569651E] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48504,7 +48597,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_auth_data
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_auth_data] ADD CONSTRAINT [PK__onl_auth__3213E83FAA802EC4] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_auth_data] ADD CONSTRAINT [PK__onl_auth__3213E83F5F4610C1] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48529,7 +48622,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_auth_page
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_auth_page] ADD CONSTRAINT [PK__onl_auth__3213E83F1A584903] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_auth_page] ADD CONSTRAINT [PK__onl_auth__3213E83F85A3BA39] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48538,7 +48631,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_auth_relation
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_auth_relation] ADD CONSTRAINT [PK__onl_auth__3213E83FB6475679] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_auth_relation] ADD CONSTRAINT [PK__onl_auth__3213E83F993DE902] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48575,7 +48668,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_cgform_button
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_cgform_button] ADD CONSTRAINT [PK__onl_cgfo__3213E83F1358FD14] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_cgform_button] ADD CONSTRAINT [PK__onl_cgfo__3213E83F2F9D6D35] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48606,7 +48699,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_cgform_enhance_java
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_cgform_enhance_java] ADD CONSTRAINT [PK__onl_cgfo__3213E83F50E2B881] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_cgform_enhance_java] ADD CONSTRAINT [PK__onl_cgfo__3213E83F0685BE50] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48631,7 +48724,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_cgform_enhance_js
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_cgform_enhance_js] ADD CONSTRAINT [PK__onl_cgfo__3213E83FF145EA43] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_cgform_enhance_js] ADD CONSTRAINT [PK__onl_cgfo__3213E83FE0F35590] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48650,7 +48743,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_cgform_enhance_sql
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_cgform_enhance_sql] ADD CONSTRAINT [PK__onl_cgfo__3213E83FC88D1C1A] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_cgform_enhance_sql] ADD CONSTRAINT [PK__onl_cgfo__3213E83F3E448CAB] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48669,7 +48762,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_cgform_field
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_cgform_field] ADD CONSTRAINT [PK__onl_cgfo__3213E83F94F380B1] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_cgform_field] ADD CONSTRAINT [PK__onl_cgfo__3213E83FE05F0414] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48706,7 +48799,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_cgform_head
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_cgform_head] ADD CONSTRAINT [PK__onl_cgfo__3213E83F1705FE7A] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_cgform_head] ADD CONSTRAINT [PK__onl_cgfo__3213E83F6D17E57F] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48725,7 +48818,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_cgform_index
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_cgform_index] ADD CONSTRAINT [PK__onl_cgfo__3213E83FDC0CC162] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_cgform_index] ADD CONSTRAINT [PK__onl_cgfo__3213E83FE43E7A85] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48744,7 +48837,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_cgreport_head
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_cgreport_head] ADD CONSTRAINT [PK__onl_cgre__3213E83FE9C96B0B] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_cgreport_head] ADD CONSTRAINT [PK__onl_cgre__3213E83FEA0990AC] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48775,7 +48868,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_cgreport_item
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_cgreport_item] ADD CONSTRAINT [PK__onl_cgre__3213E83F70C65EB8] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_cgreport_item] ADD CONSTRAINT [PK__onl_cgre__3213E83F24834090] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48794,7 +48887,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_cgreport_param
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_cgreport_param] ADD CONSTRAINT [PK__onl_cgre__3213E83F25593B2D] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_cgreport_param] ADD CONSTRAINT [PK__onl_cgre__3213E83FA8995174] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48803,7 +48896,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_drag_comp
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_drag_comp] ADD CONSTRAINT [PK__onl_drag__3213E83F531BC7EA] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_drag_comp] ADD CONSTRAINT [PK__onl_drag__3213E83F80FD75F1] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48812,7 +48905,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_drag_dataset_head
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_drag_dataset_head] ADD CONSTRAINT [PK__onl_drag__3213E83FACFE4ADD] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_drag_dataset_head] ADD CONSTRAINT [PK__onl_drag__3213E83F41C69FE4] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48831,7 +48924,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_drag_dataset_item
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_drag_dataset_item] ADD CONSTRAINT [PK__onl_drag__3213E83F433BCAB1] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_drag_dataset_item] ADD CONSTRAINT [PK__onl_drag__3213E83FC335E910] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48850,7 +48943,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_drag_dataset_param
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_drag_dataset_param] ADD CONSTRAINT [PK__onl_drag__3213E83F40211C27] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_drag_dataset_param] ADD CONSTRAINT [PK__onl_drag__3213E83F94E85FE3] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48859,7 +48952,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_drag_page
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_drag_page] ADD CONSTRAINT [PK__onl_drag__3213E83FDF46AAA9] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_drag_page] ADD CONSTRAINT [PK__onl_drag__3213E83F4A7E2A0C] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48868,7 +48961,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_drag_page_comp
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_drag_page_comp] ADD CONSTRAINT [PK__onl_drag__3213E83F83CA721F] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_drag_page_comp] ADD CONSTRAINT [PK__onl_drag__3213E83F21884F86] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48894,7 +48987,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_drag_share
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_drag_share] ADD CONSTRAINT [PK__onl_drag__3213E83F8B3106EE] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_drag_share] ADD CONSTRAINT [PK__onl_drag__3213E83F8C4094C7] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48931,7 +49024,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table onl_drag_table_relation
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[onl_drag_table_relation] ADD CONSTRAINT [PK__onl_drag__3213E83F6BB33894] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[onl_drag_table_relation] ADD CONSTRAINT [PK__onl_drag__3213E83FA7E2FBE9] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48940,7 +49033,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table open_api
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[open_api] ADD CONSTRAINT [PK__open_api__3213E83F88349C20] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[open_api] ADD CONSTRAINT [PK__open_api__3213E83F10BCA05A] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48949,7 +49042,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table open_api_auth
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[open_api_auth] ADD CONSTRAINT [PK__open_api__3213E83F41CA9928] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[open_api_auth] ADD CONSTRAINT [PK__open_api__3213E83FB3F58961] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48958,7 +49051,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table open_api_log
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[open_api_log] ADD CONSTRAINT [PK__open_api__3213E83F95659E2E] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[open_api_log] ADD CONSTRAINT [PK__open_api__3213E83FF028FCC2] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48967,7 +49060,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table open_api_permission
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[open_api_permission] ADD CONSTRAINT [PK__open_api__3213E83F4B0F5CFD] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[open_api_permission] ADD CONSTRAINT [PK__open_api__3213E83F5ECC328A] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -48976,7 +49069,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table oss_file
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[oss_file] ADD CONSTRAINT [PK__oss_file__3213E83F8BED225A] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[oss_file] ADD CONSTRAINT [PK__oss_file__3213E83F9898A904] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49075,7 +49168,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table rep_demo_dxtj
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[rep_demo_dxtj] ADD CONSTRAINT [PK__rep_demo__3213E83FFF38D434] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[rep_demo_dxtj] ADD CONSTRAINT [PK__rep_demo__3213E83F2531F618] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49084,7 +49177,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table rep_demo_employee
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[rep_demo_employee] ADD CONSTRAINT [PK__rep_demo__3213E83F5D1E0EFC] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[rep_demo_employee] ADD CONSTRAINT [PK__rep_demo__3213E83F0F4F099A] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49093,7 +49186,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table rep_demo_gongsi
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[rep_demo_gongsi] ADD CONSTRAINT [PK__rep_demo__3213E83FBDF70370] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[rep_demo_gongsi] ADD CONSTRAINT [PK__rep_demo__3213E83FB3B7E287] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49102,7 +49195,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table rep_demo_jianpiao
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[rep_demo_jianpiao] ADD CONSTRAINT [PK__rep_demo__3213E83F94A51ED5] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[rep_demo_jianpiao] ADD CONSTRAINT [PK__rep_demo__3213E83F8CA85143] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49111,7 +49204,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table rep_demo_order_main
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[rep_demo_order_main] ADD CONSTRAINT [PK__rep_demo__3213E83FC1AF14F6] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[rep_demo_order_main] ADD CONSTRAINT [PK__rep_demo__3213E83FF1EE3804] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49120,7 +49213,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table rep_demo_order_product
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[rep_demo_order_product] ADD CONSTRAINT [PK__rep_demo__3213E83F8BA59254] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[rep_demo_order_product] ADD CONSTRAINT [PK__rep_demo__3213E83F33E51CDE] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49181,7 +49274,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_announcement
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_announcement] ADD CONSTRAINT [PK__sys_anno__3213E83F0D8C3B91] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_announcement] ADD CONSTRAINT [PK__sys_anno__3213E83F07E5BF25] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49218,7 +49311,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_announcement_send
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_announcement_send] ADD CONSTRAINT [PK__sys_anno__3213E83FA47F1CBE] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_announcement_send] ADD CONSTRAINT [PK__sys_anno__3213E83F6D326573] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49227,7 +49320,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_category
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_category] ADD CONSTRAINT [PK__sys_cate__3213E83F33C3B659] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_category] ADD CONSTRAINT [PK__sys_cate__3213E83FB80600B6] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49246,7 +49339,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_check_rule
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_check_rule] ADD CONSTRAINT [PK__sys_chec__3213E83F21B54C9B] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_check_rule] ADD CONSTRAINT [PK__sys_chec__3213E83F0A86AF0E] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49266,7 +49359,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_comment
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_comment] ADD CONSTRAINT [PK__sys_comm__3213E83F45526F47] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_comment] ADD CONSTRAINT [PK__sys_comm__3213E83FAE641A15] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49286,7 +49379,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_data_log
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_data_log] ADD CONSTRAINT [PK__sys_data__3213E83FC2663C59] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_data_log] ADD CONSTRAINT [PK__sys_data__3213E83FB48E0DCC] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49305,7 +49398,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_data_source
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_data_source] ADD CONSTRAINT [PK__sys_data__3213E83F3BA5CF80] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_data_source] ADD CONSTRAINT [PK__sys_data__3213E83F70028109] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49348,7 +49441,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_depart
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_depart] ADD CONSTRAINT [PK__sys_depa__3213E83FDA47E76D] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_depart] ADD CONSTRAINT [PK__sys_depa__3213E83FA21F4654] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49357,7 +49450,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_depart_permission
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_depart_permission] ADD CONSTRAINT [PK__sys_depa__3213E83F9463049D] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_depart_permission] ADD CONSTRAINT [PK__sys_depa__3213E83FF02BA272] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49366,7 +49459,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_depart_role
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_depart_role] ADD CONSTRAINT [PK__sys_depa__3213E83F85076FEB] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_depart_role] ADD CONSTRAINT [PK__sys_depa__3213E83F0AF90373] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49398,7 +49491,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_depart_role_permission
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_depart_role_permission] ADD CONSTRAINT [PK__sys_depa__3213E83FE7E95AFE] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_depart_role_permission] ADD CONSTRAINT [PK__sys_depa__3213E83FC389D536] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49423,7 +49516,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_depart_role_user
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_depart_role_user] ADD CONSTRAINT [PK__sys_depa__3213E83FCA7B97BE] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_depart_role_user] ADD CONSTRAINT [PK__sys_depa__3213E83F8A10956E] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49448,7 +49541,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_dict
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_dict] ADD CONSTRAINT [PK__sys_dict__3213E83F2D0A72FE] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_dict] ADD CONSTRAINT [PK__sys_dict__3213E83F416B08BE] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49486,7 +49579,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_dict_item
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_dict_item] ADD CONSTRAINT [PK__sys_dict__3213E83F1B9CE54D] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_dict_item] ADD CONSTRAINT [PK__sys_dict__3213E83F988B64AF] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49511,7 +49604,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_files
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_files] ADD CONSTRAINT [PK__sys_file__3213E83F6CF0D0F4] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_files] ADD CONSTRAINT [PK__sys_file__3213E83FF688970F] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49530,7 +49623,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_fill_rule
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_fill_rule] ADD CONSTRAINT [PK__sys_fill__3213E83F9677507D] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_fill_rule] ADD CONSTRAINT [PK__sys_fill__3213E83F982894F4] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49556,7 +49649,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_form_file
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_form_file] ADD CONSTRAINT [PK__sys_form__3213E83FFCC893BD] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_form_file] ADD CONSTRAINT [PK__sys_form__3213E83F6116398E] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49565,7 +49658,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_gateway_route
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_gateway_route] ADD CONSTRAINT [PK__sys_gate__3213E83FCECFCA6E] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_gateway_route] ADD CONSTRAINT [PK__sys_gate__3213E83F3AEA2539] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49602,7 +49695,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_log
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_log] ADD CONSTRAINT [PK__sys_log__3213E83F87AEF960] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_log] ADD CONSTRAINT [PK__sys_log__3213E83F899DF7EE] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49651,7 +49744,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_permission
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_permission] ADD CONSTRAINT [PK__sys_perm__3213E83F4F33038B] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_permission] ADD CONSTRAINT [PK__sys_perm__3213E83FA87872D5] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49670,7 +49763,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_permission_data_rule
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_permission_data_rule] ADD CONSTRAINT [PK__sys_perm__3213E83F1EC8ADAD] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_permission_data_rule] ADD CONSTRAINT [PK__sys_perm__3213E83F9C51AB30] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49689,7 +49782,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_position
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_position] ADD CONSTRAINT [PK__sys_posi__3213E83F4C36D8AF] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_position] ADD CONSTRAINT [PK__sys_posi__3213E83F00463CBA] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49698,7 +49791,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_quartz_job
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_quartz_job] ADD CONSTRAINT [PK__sys_quar__3213E83F77193621] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_quartz_job] ADD CONSTRAINT [PK__sys_quar__3213E83FE87B06A2] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49723,7 +49816,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_role
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_role] ADD CONSTRAINT [PK__sys_role__3213E83FECC7EFD1] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_role] ADD CONSTRAINT [PK__sys_role__3213E83F204E86A4] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49754,7 +49847,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_role_index
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_role_index] ADD CONSTRAINT [PK__sys_role__3213E83F7488BC21] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_role_index] ADD CONSTRAINT [PK__sys_role__3213E83FAB72E5F9] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49786,7 +49879,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_role_permission
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_role_permission] ADD CONSTRAINT [PK__sys_role__3213E83F011ED5BD] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_role_permission] ADD CONSTRAINT [PK__sys_role__3213E83FCFD2061C] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49823,7 +49916,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_sms
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_sms] ADD CONSTRAINT [PK__sys_sms__3213E83F900482D6] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_sms] ADD CONSTRAINT [PK__sys_sms__3213E83F21923C7A] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49842,7 +49935,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_sms_template
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_sms_template] ADD CONSTRAINT [PK__sys_sms___3213E83F150DB986] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_sms_template] ADD CONSTRAINT [PK__sys_sms___3213E83FCD76A81E] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49861,7 +49954,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_table_white_list
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_table_white_list] ADD CONSTRAINT [PK__sys_tabl__3213E83F43D6591D] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_table_white_list] ADD CONSTRAINT [PK__sys_tabl__3213E83F274CCE05] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49870,7 +49963,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_tenant
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_tenant] ADD CONSTRAINT [PK__sys_tena__3213E83FDB9DA19F] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_tenant] ADD CONSTRAINT [PK__sys_tena__3213E83FF1B4A332] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49890,7 +49983,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_tenant_pack
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_tenant_pack] ADD CONSTRAINT [PK__sys_tena__3213E83FDA9DF743] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_tenant_pack] ADD CONSTRAINT [PK__sys_tena__3213E83F73D6EA67] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49909,7 +50002,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_tenant_pack_perms
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_tenant_pack_perms] ADD CONSTRAINT [PK__sys_tena__3213E83FFB39CCEB] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_tenant_pack_perms] ADD CONSTRAINT [PK__sys_tena__3213E83F47DB59EC] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49946,7 +50039,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_tenant_pack_user
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_tenant_pack_user] ADD CONSTRAINT [PK__sys_tena__3213E83FA7140C9B] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_tenant_pack_user] ADD CONSTRAINT [PK__sys_tena__3213E83F10086066] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -49982,7 +50075,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_third_account
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_third_account] ADD CONSTRAINT [PK__sys_thir__3213E83F8AAA793F] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_third_account] ADD CONSTRAINT [PK__sys_thir__3213E83F66D5B174] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -50007,7 +50100,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_third_app_config
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_third_app_config] ADD CONSTRAINT [PK__sys_thir__3213E83F695D5C5E] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_third_app_config] ADD CONSTRAINT [PK__sys_thir__3213E83F67503374] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -50069,7 +50162,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_user
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_user] ADD CONSTRAINT [PK__sys_user__3213E83FD895AF5C] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_user] ADD CONSTRAINT [PK__sys_user__3213E83F356BF399] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -50101,7 +50194,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_user_dep_post
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_user_dep_post] ADD CONSTRAINT [PK__sys_user__3213E83FE61706C1] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_user_dep_post] ADD CONSTRAINT [PK__sys_user__3213E83F914ED9EB] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -50133,7 +50226,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_user_depart
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_user_depart] ADD CONSTRAINT [PK__sys_user__3213E83FE6442AF7] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_user_depart] ADD CONSTRAINT [PK__sys_user__3213E83FBADFFB9F] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -50165,7 +50258,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_user_position
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_user_position] ADD CONSTRAINT [PK__sys_user__3213E83FE4F1412B] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_user_position] ADD CONSTRAINT [PK__sys_user__3213E83F5C9D222C] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -50197,7 +50290,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_user_role
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_user_role] ADD CONSTRAINT [PK__sys_user__3213E83F4271AE1F] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_user_role] ADD CONSTRAINT [PK__sys_user__3213E83F3472E02B] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -50242,7 +50335,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table sys_user_tenant
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[sys_user_tenant] ADD CONSTRAINT [PK__sys_user__3213E83F9087F1AB] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[sys_user_tenant] ADD CONSTRAINT [PK__sys_user__3213E83F264F87E5] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -50251,7 +50344,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table test_demo
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[test_demo] ADD CONSTRAINT [PK__test_dem__3213E83FACFD2100] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[test_demo] ADD CONSTRAINT [PK__test_dem__3213E83F8B80F8A8] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -50260,7 +50353,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table test_enhance_select
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[test_enhance_select] ADD CONSTRAINT [PK__test_enh__3213E83F45BD474F] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[test_enhance_select] ADD CONSTRAINT [PK__test_enh__3213E83FA16D80A6] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -50269,7 +50362,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table test_note
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[test_note] ADD CONSTRAINT [PK__test_not__3213E83F63C5AD8C] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[test_note] ADD CONSTRAINT [PK__test_not__3213E83FD208D9AF] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -50278,7 +50371,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table test_online_link
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[test_online_link] ADD CONSTRAINT [PK__test_onl__3213E83F5EC622CD] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[test_online_link] ADD CONSTRAINT [PK__test_onl__3213E83F19289BEC] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -50287,7 +50380,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table test_order_customer
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[test_order_customer] ADD CONSTRAINT [PK__test_ord__3213E83FDE802ADF] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[test_order_customer] ADD CONSTRAINT [PK__test_ord__3213E83F16091A93] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -50296,7 +50389,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table test_order_main
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[test_order_main] ADD CONSTRAINT [PK__test_ord__3213E83FD8EFBA93] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[test_order_main] ADD CONSTRAINT [PK__test_ord__3213E83FD27ED8AA] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -50305,7 +50398,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table test_order_product
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[test_order_product] ADD CONSTRAINT [PK__test_ord__3213E83F5E0DCE72] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[test_order_product] ADD CONSTRAINT [PK__test_ord__3213E83F439007A8] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -50314,7 +50407,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table test_person
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[test_person] ADD CONSTRAINT [PK__test_per__3213E83FFCBB82F8] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[test_person] ADD CONSTRAINT [PK__test_per__3213E83F861BE539] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
@ -50323,7 +50416,7 @@ GO
|
||||
-- ----------------------------
|
||||
-- Primary Key structure for table test_shoptype_tree
|
||||
-- ----------------------------
|
||||
ALTER TABLE [dbo].[test_shoptype_tree] ADD CONSTRAINT [PK__test_sho__3213E83FD04AA7D4] PRIMARY KEY CLUSTERED ([id])
|
||||
ALTER TABLE [dbo].[test_shoptype_tree] ADD CONSTRAINT [PK__test_sho__3213E83FC0BAE273] PRIMARY KEY CLUSTERED ([id])
|
||||
WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON)
|
||||
ON [PRIMARY]
|
||||
GO
|
||||
|
||||
@ -185,85 +185,25 @@
|
||||
<artifactId>spring-boot-starter-quartz</artifactId>
|
||||
</dependency>
|
||||
|
||||
<!--JWT-->
|
||||
<!-- Sa-Token 权限认证,在线文档:https://sa-token.cc -->
|
||||
<dependency>
|
||||
<groupId>com.auth0</groupId>
|
||||
<artifactId>java-jwt</artifactId>
|
||||
<version>${java-jwt.version}</version>
|
||||
<groupId>cn.dev33</groupId>
|
||||
<artifactId>sa-token-spring-boot3-starter</artifactId>
|
||||
<version>${sa-token.version}</version>
|
||||
</dependency>
|
||||
|
||||
<!--shiro-->
|
||||
<!-- Sa-Token 整合 Redis (使用 jackson 序列化方式) -->
|
||||
<dependency>
|
||||
<groupId>org.apache.shiro</groupId>
|
||||
<artifactId>shiro-spring-boot-starter</artifactId>
|
||||
<classifier>jakarta</classifier>
|
||||
<version>${shiro.version}</version>
|
||||
<exclusions>
|
||||
<exclusion>
|
||||
<groupId>org.apache.shiro</groupId>
|
||||
<artifactId>shiro-spring</artifactId>
|
||||
</exclusion>
|
||||
</exclusions>
|
||||
<groupId>cn.dev33</groupId>
|
||||
<artifactId>sa-token-redis-jackson</artifactId>
|
||||
<version>${sa-token.version}</version>
|
||||
</dependency>
|
||||
<!-- Sa-Token 整合 jwt (Simple模式),保持与原JWT token格式兼容 -->
|
||||
<dependency>
|
||||
<groupId>org.apache.shiro</groupId>
|
||||
<artifactId>shiro-spring</artifactId>
|
||||
<classifier>jakarta</classifier>
|
||||
<version>${shiro.version}</version>
|
||||
<!-- 排除仍使用了javax.servlet的依赖 -->
|
||||
<exclusions>
|
||||
<exclusion>
|
||||
<groupId>org.apache.shiro</groupId>
|
||||
<artifactId>shiro-core</artifactId>
|
||||
</exclusion>
|
||||
<exclusion>
|
||||
<groupId>org.apache.shiro</groupId>
|
||||
<artifactId>shiro-web</artifactId>
|
||||
</exclusion>
|
||||
</exclusions>
|
||||
<groupId>cn.dev33</groupId>
|
||||
<artifactId>sa-token-jwt</artifactId>
|
||||
<version>${sa-token.version}</version>
|
||||
</dependency>
|
||||
<!-- 引入适配jakarta的依赖包 -->
|
||||
<dependency>
|
||||
<groupId>org.apache.shiro</groupId>
|
||||
<artifactId>shiro-core</artifactId>
|
||||
<classifier>jakarta</classifier>
|
||||
<version>${shiro.version}</version>
|
||||
<exclusions>
|
||||
<exclusion>
|
||||
<groupId>commons-beanutils</groupId>
|
||||
<artifactId>commons-beanutils</artifactId>
|
||||
</exclusion>
|
||||
</exclusions>
|
||||
</dependency>
|
||||
<dependency>
|
||||
<groupId>org.apache.shiro</groupId>
|
||||
<artifactId>shiro-web</artifactId>
|
||||
<classifier>jakarta</classifier>
|
||||
<version>${shiro.version}</version>
|
||||
<exclusions>
|
||||
<exclusion>
|
||||
<groupId>org.apache.shiro</groupId>
|
||||
<artifactId>shiro-core</artifactId>
|
||||
</exclusion>
|
||||
</exclusions>
|
||||
</dependency>
|
||||
<!-- shiro-redis -->
|
||||
<dependency>
|
||||
<groupId>org.crazycake</groupId>
|
||||
<artifactId>shiro-redis</artifactId>
|
||||
<version>${shiro-redis.version}</version>
|
||||
<exclusions>
|
||||
<exclusion>
|
||||
<groupId>org.apache.shiro</groupId>
|
||||
<artifactId>shiro-core</artifactId>
|
||||
</exclusion>
|
||||
<exclusion>
|
||||
<artifactId>checkstyle</artifactId>
|
||||
<groupId>com.puppycrawl.tools</groupId>
|
||||
</exclusion>
|
||||
</exclusions>
|
||||
</dependency>
|
||||
|
||||
|
||||
<dependency>
|
||||
<groupId>com.github.xiaoymin</groupId>
|
||||
<artifactId>knife4j-openapi3-ui</artifactId>
|
||||
|
||||
@ -0,0 +1,21 @@
|
||||
package org.apache.shiro;
|
||||
|
||||
import org.apache.shiro.subject.Subject;
|
||||
|
||||
/**
|
||||
* 兼容处理Online功能使用处理,请勿修改
|
||||
* @author eightmonth@qq.com
|
||||
* @date 2024/4/29 14:05
|
||||
*/
|
||||
public class SecurityUtils {
|
||||
|
||||
|
||||
public static Subject getSubject() {
|
||||
return new Subject() {
|
||||
@Override
|
||||
public Object getPrincipal() {
|
||||
return Subject.super.getPrincipal();
|
||||
}
|
||||
};
|
||||
}
|
||||
}
|
||||
@ -0,0 +1,15 @@
|
||||
package org.apache.shiro.subject;
|
||||
|
||||
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
|
||||
/**
|
||||
* 兼容处理Online功能使用处理,请勿修改
|
||||
* @author eightmonth@qq.com
|
||||
* @date 2024/4/29 14:18
|
||||
*/
|
||||
public interface Subject {
|
||||
default Object getPrincipal() {
|
||||
return LoginUserUtils.getSessionUser();
|
||||
}
|
||||
}
|
||||
@ -2,7 +2,7 @@ package org.jeecg.common.aspect;
|
||||
|
||||
import com.alibaba.fastjson.JSONObject;
|
||||
import com.alibaba.fastjson.serializer.PropertyFilter;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.aspectj.lang.JoinPoint;
|
||||
import org.aspectj.lang.ProceedingJoinPoint;
|
||||
import org.aspectj.lang.annotation.Around;
|
||||
@ -100,7 +100,7 @@ public class AutoLogAspect {
|
||||
//设置IP地址
|
||||
dto.setIp(IpUtils.getIpAddr(request));
|
||||
//获取登录用户信息
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
if(sysUser!=null){
|
||||
dto.setUserid(sysUser.getUsername());
|
||||
dto.setUsername(sysUser.getRealname());
|
||||
@ -243,7 +243,7 @@ public class AutoLogAspect {
|
||||
sysLog.setIp(IPUtils.getIpAddr(request));
|
||||
|
||||
//获取登录用户信息
|
||||
LoginUser sysUser = (LoginUser)SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getLoginUser();
|
||||
if(sysUser!=null){
|
||||
sysLog.setUserid(sysUser.getUsername());
|
||||
sysLog.setUsername(sysUser.getRealname());
|
||||
|
||||
@ -87,30 +87,6 @@ public interface CommonConstant {
|
||||
/**访问权限认证未通过 510*/
|
||||
Integer SC_JEECG_NO_AUTHZ=510;
|
||||
|
||||
/** 登录用户Shiro权限缓存KEY前缀 */
|
||||
public static String PREFIX_USER_SHIRO_CACHE = "shiro:cache:org.jeecg.config.shiro.ShiroRealm.authorizationCache:";
|
||||
/** 登录用户Token令牌缓存KEY前缀 */
|
||||
String PREFIX_USER_TOKEN = "prefix_user_token:";
|
||||
/** 登录用户Token令牌作废提示信息,比如 “不允许同一账号多地同时登录,会往这个变量存提示信息” */
|
||||
String PREFIX_USER_TOKEN_ERROR_MSG = "prefix_user_token:error:msg_";
|
||||
|
||||
/**============================== 【是否允许同一账号多地同时登录】登录客户端类型常量 ==============================*/
|
||||
/** 客户端类型:PC端 */
|
||||
String CLIENT_TYPE_PC = "PC";
|
||||
/** 客户端类型:APP端 */
|
||||
String CLIENT_TYPE_APP = "APP";
|
||||
/** 客户端类型:手机号登录 */
|
||||
String CLIENT_TYPE_PHONE = "PHONE";
|
||||
String PREFIX_USER_TOKEN_PC = "prefix_user_token:single_login:pc:";
|
||||
/** 单点登录:用户在APP端的Token缓存KEY前缀 (username -> token) */
|
||||
String PREFIX_USER_TOKEN_APP = "prefix_user_token:single_login:app:";
|
||||
/** 单点登录:用户在手机号登录的Token缓存KEY前缀 (username -> token) */
|
||||
String PREFIX_USER_TOKEN_PHONE = "prefix_user_token:single_login:phone:";
|
||||
/**============================== 【是否允许同一账号多地同时登录】登录客户端类型常量 ==============================*/
|
||||
|
||||
// /** Token缓存时间:3600秒即一小时 */
|
||||
// int TOKEN_EXPIRE_TIME = 3600;
|
||||
|
||||
/** 登录二维码 */
|
||||
String LOGIN_QRCODE_PRE = "QRCODELOGIN:";
|
||||
String LOGIN_QRCODE = "LQ:";
|
||||
@ -741,4 +717,13 @@ public interface CommonConstant {
|
||||
* 发送短信方式:阿里云
|
||||
*/
|
||||
String SMS_SEND_TYPE_ALI_YUN = "aliyun";
|
||||
|
||||
/**============================== 【是否允许同一账号多地同时登录】登录客户端类型常量 ==============================*/
|
||||
/** 客户端类型:PC端 */
|
||||
String CLIENT_TYPE_PC = "PC";
|
||||
/** 客户端类型:APP端 */
|
||||
String CLIENT_TYPE_APP = "APP";
|
||||
/** 客户端类型:手机号登录 */
|
||||
String CLIENT_TYPE_PHONE = "PHONE";
|
||||
/**============================== 【是否允许同一账号多地同时登录】登录客户端类型常量 ==============================*/
|
||||
}
|
||||
|
||||
@ -5,9 +5,10 @@ import jakarta.annotation.Resource;
|
||||
import jakarta.servlet.http.HttpServletRequest;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.commons.lang3.exception.ExceptionUtils;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.apache.shiro.authz.AuthorizationException;
|
||||
import org.apache.shiro.authz.UnauthorizedException;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import cn.dev33.satoken.exception.NotLoginException;
|
||||
import cn.dev33.satoken.exception.NotPermissionException;
|
||||
import cn.dev33.satoken.exception.NotRoleException;
|
||||
import org.jeecg.common.api.dto.LogDTO;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
@ -112,12 +113,34 @@ public class JeecgBootExceptionHandler {
|
||||
return Result.error("数据库中已存在该记录");
|
||||
}
|
||||
|
||||
@ExceptionHandler({UnauthorizedException.class, AuthorizationException.class})
|
||||
public Result<?> handleAuthorizationException(AuthorizationException e){
|
||||
/**
|
||||
* 处理Sa-Token未登录异常
|
||||
*/
|
||||
@ExceptionHandler(NotLoginException.class)
|
||||
@ResponseStatus(HttpStatus.UNAUTHORIZED)
|
||||
public Result<?> handleNotLoginException(NotLoginException e){
|
||||
log.error("Sa-Token未登录异常: {}", e.getMessage());
|
||||
return new Result(401, CommonConstant.TOKEN_IS_INVALID_MSG);
|
||||
}
|
||||
|
||||
/**
|
||||
* 处理Sa-Token无权限异常
|
||||
*/
|
||||
@ExceptionHandler(NotPermissionException.class)
|
||||
public Result<?> handleNotPermissionException(NotPermissionException e){
|
||||
log.error(e.getMessage(), e);
|
||||
return Result.noauth("没有权限,请联系管理员分配权限!");
|
||||
}
|
||||
|
||||
/**
|
||||
* 处理Sa-Token无角色异常
|
||||
*/
|
||||
@ExceptionHandler(NotRoleException.class)
|
||||
public Result<?> handleNotRoleException(NotRoleException e){
|
||||
log.error(e.getMessage(), e);
|
||||
return Result.noauth("没有角色权限,请联系管理员分配角色!");
|
||||
}
|
||||
|
||||
@ExceptionHandler(Exception.class)
|
||||
public Result<?> handleException(Exception e){
|
||||
log.error(e.getMessage(), e);
|
||||
@ -263,7 +286,7 @@ public class JeecgBootExceptionHandler {
|
||||
|
||||
|
||||
//获取登录用户信息
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
if(sysUser!=null){
|
||||
log.setUserid(sysUser.getUsername());
|
||||
log.setUsername(sysUser.getRealname());
|
||||
|
||||
@ -6,10 +6,10 @@ import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
import com.baomidou.mybatisplus.extension.service.IService;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.commons.beanutils.PropertyUtils;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.system.query.QueryGenerator;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.util.oConvertUtils;
|
||||
import org.jeecg.config.JeecgBaseConfig;
|
||||
import org.jeecgframework.poi.excel.ExcelImportUtil;
|
||||
@ -52,7 +52,7 @@ public class JeecgController<T, S extends IService<T>> {
|
||||
protected ModelAndView exportXls(HttpServletRequest request, T object, Class<T> clazz, String title) {
|
||||
// Step.1 组装查询条件
|
||||
QueryWrapper<T> queryWrapper = QueryGenerator.initQueryWrapper(object, request.getParameterMap());
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
|
||||
// 过滤选中数据
|
||||
String selections = request.getParameter("selections");
|
||||
@ -94,7 +94,7 @@ public class JeecgController<T, S extends IService<T>> {
|
||||
protected ModelAndView exportXlsSheet(HttpServletRequest request, T object, Class<T> clazz, String title,String exportFields,Integer pageNum) {
|
||||
// Step.1 组装查询条件
|
||||
QueryWrapper<T> queryWrapper = QueryGenerator.initQueryWrapper(object, request.getParameterMap());
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
// Step.2 计算分页sheet数据
|
||||
double total = service.count();
|
||||
int count = (int)Math.ceil(total/pageNum);
|
||||
@ -144,7 +144,7 @@ public class JeecgController<T, S extends IService<T>> {
|
||||
protected ModelAndView exportXlsForBigData(HttpServletRequest request, T object, Class<T> clazz, String title,Integer pageSize) {
|
||||
// 组装查询条件
|
||||
QueryWrapper<T> queryWrapper = QueryGenerator.initQueryWrapper(object, request.getParameterMap());
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
// 计算分页数
|
||||
double total = service.count();
|
||||
int count = (int) Math.ceil(total / pageSize);
|
||||
|
||||
@ -1,31 +1,23 @@
|
||||
package org.jeecg.common.system.util;
|
||||
|
||||
import com.auth0.jwt.JWT;
|
||||
import com.auth0.jwt.JWTVerifier;
|
||||
import com.auth0.jwt.algorithms.Algorithm;
|
||||
import com.auth0.jwt.exceptions.JWTDecodeException;
|
||||
import com.auth0.jwt.interfaces.DecodedJWT;
|
||||
import cn.dev33.satoken.stp.StpUtil;
|
||||
import com.fasterxml.jackson.databind.ObjectMapper;
|
||||
import com.google.common.base.Joiner;
|
||||
|
||||
import java.io.IOException;
|
||||
import java.io.OutputStream;
|
||||
import java.util.Date;
|
||||
import java.util.Objects;
|
||||
import java.util.stream.Collectors;
|
||||
|
||||
import jakarta.servlet.ServletResponse;
|
||||
import jakarta.servlet.http.HttpServletRequest;
|
||||
import jakarta.servlet.http.HttpServletResponse;
|
||||
import jakarta.servlet.http.HttpSession;
|
||||
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.constant.DataBaseConstant;
|
||||
import org.jeecg.common.constant.SymbolConstant;
|
||||
import org.jeecg.common.constant.TenantConstant;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.constant.DataBaseConstant;
|
||||
import org.jeecg.common.exception.JeecgBootException;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.jeecg.common.system.vo.SysUserCacheInfo;
|
||||
@ -36,159 +28,74 @@ import org.jeecg.common.util.oConvertUtils;
|
||||
/**
|
||||
* @Author Scott
|
||||
* @Date 2018-07-12 14:23
|
||||
* @Desc JWT工具类
|
||||
* @Desc JWT工具类 - 已迁移到Sa-Token,此类作为兼容层保留
|
||||
**/
|
||||
@Slf4j
|
||||
public class JwtUtil {
|
||||
|
||||
/**PC端,Token有效期为7天(Token在reids中缓存时间为两倍)*/
|
||||
public static final long EXPIRE_TIME = (7 * 12) * 60 * 60 * 1000L;
|
||||
/**APP端,Token有效期为30天(Token在reids中缓存时间为两倍)*/
|
||||
public static final long APP_EXPIRE_TIME = (30 * 12) * 60 * 60 * 1000L;
|
||||
|
||||
static final String WELL_NUMBER = SymbolConstant.WELL_NUMBER + SymbolConstant.LEFT_CURLY_BRACKET;
|
||||
|
||||
/**
|
||||
*
|
||||
* @param response
|
||||
* @param code
|
||||
* @param errorMsg
|
||||
*/
|
||||
public static void responseError(HttpServletResponse response, Integer code, String errorMsg) {
|
||||
|
||||
/**
|
||||
* 返回错误 JSON 字符串(用于 Sa-Token Filter)
|
||||
* @param code 错误码
|
||||
* @param errorMsg 错误信息
|
||||
* @return JSON 字符串
|
||||
*/
|
||||
public static String responseErrorJson(Integer code, String errorMsg) {
|
||||
try {
|
||||
Result jsonResult = new Result(code, errorMsg);
|
||||
jsonResult.setSuccess(false);
|
||||
|
||||
// 设置响应头和内容类型
|
||||
response.setStatus(code);
|
||||
response.setHeader("Content-type", "text/html;charset=UTF-8");
|
||||
response.setContentType("application/json;charset=UTF-8");
|
||||
// 使用 ObjectMapper 序列化为 JSON 字符串
|
||||
ObjectMapper objectMapper = new ObjectMapper();
|
||||
String json = objectMapper.writeValueAsString(jsonResult);
|
||||
response.getWriter().write(json);
|
||||
response.getWriter().flush();
|
||||
return objectMapper.writeValueAsString(jsonResult);
|
||||
} catch (IOException e) {
|
||||
log.error(e.getMessage(), e);
|
||||
log.error("生成错误 JSON 失败: {}", e.getMessage());
|
||||
// 返回备用的硬编码 JSON
|
||||
return "{\"success\":false,\"message\":\"" + errorMsg + "\",\"code\":" + code + ",\"result\":null,\"timestamp\":" + System.currentTimeMillis() + "}";
|
||||
}
|
||||
}
|
||||
|
||||
|
||||
/**
|
||||
* 校验token是否正确
|
||||
*
|
||||
* @param token 密钥
|
||||
* @param secret 用户的密码
|
||||
* @return 是否正确
|
||||
* 注意:此方法已废弃,使用Sa-Token自动校验
|
||||
*
|
||||
* @param token
|
||||
* @return
|
||||
*/
|
||||
public static boolean verify(String token, String username, String secret) {
|
||||
@Deprecated
|
||||
public static boolean verify(String token){
|
||||
try {
|
||||
// 根据密码生成JWT效验器
|
||||
Algorithm algorithm = Algorithm.HMAC256(secret);
|
||||
JWTVerifier verifier = JWT.require(algorithm).withClaim("username", username).build();
|
||||
// 效验TOKEN
|
||||
DecodedJWT jwt = verifier.verify(token);
|
||||
return true;
|
||||
// 使用Sa-Token验证
|
||||
return StpUtil.getLoginIdByToken(token) != null;
|
||||
} catch (Exception e) {
|
||||
log.warn("Token验证失败:" + e.getMessage(),e);
|
||||
log.warn(e.getMessage(), e);
|
||||
return false;
|
||||
}
|
||||
}
|
||||
|
||||
/**
|
||||
* 获得token中的信息无需secret解密也能获得
|
||||
*
|
||||
* @return token中包含的用户名
|
||||
* 获得Token中的用户名(不校验token是否有效)
|
||||
* <p>注意:现在 loginId 就是 username,直接返回
|
||||
*
|
||||
* @param token JWT token
|
||||
* @return 用户名(username),如果 token 无效则返回 null
|
||||
*/
|
||||
public static String getUsername(String token) {
|
||||
public static String getUsername(String token){
|
||||
try {
|
||||
DecodedJWT jwt = JWT.decode(token);
|
||||
return jwt.getClaim("username").asString();
|
||||
} catch (JWTDecodeException e) {
|
||||
log.error(e.getMessage(), e);
|
||||
if(oConvertUtils.isEmpty(token)) {
|
||||
return null;
|
||||
}
|
||||
// Sa-Token 的 loginId 现在就是 username,直接返回
|
||||
Object loginId = StpUtil.getLoginIdByToken(token);
|
||||
return loginId != null ? loginId.toString() : null;
|
||||
} catch (Exception e) {
|
||||
log.warn("获取用户名失败: {}", e.getMessage());
|
||||
return null;
|
||||
}
|
||||
}
|
||||
|
||||
/**
|
||||
* 生成签名,5min后过期
|
||||
*
|
||||
* @param username 用户名
|
||||
* @param secret 用户的密码
|
||||
* @return 加密的token
|
||||
* @deprecated 请使用sign(String username, String secret, String clientType)方法代替
|
||||
*/
|
||||
@Deprecated
|
||||
public static String sign(String username, String secret) {
|
||||
Date date = new Date(System.currentTimeMillis() + EXPIRE_TIME);
|
||||
Algorithm algorithm = Algorithm.HMAC256(secret);
|
||||
// 附带username信息
|
||||
return JWT.create().withClaim("username", username).withExpiresAt(date).sign(algorithm);
|
||||
|
||||
}
|
||||
|
||||
|
||||
/**
|
||||
* 生成签名,5min后过期
|
||||
*
|
||||
* @param username 用户名
|
||||
* @param secret 用户的密码
|
||||
* @param expireTime 过期时间
|
||||
* @return 加密的token
|
||||
* @deprecated 请使用sign(String username, String secret, String clientType)方法代替
|
||||
*/
|
||||
@Deprecated
|
||||
public static String sign(String username, String secret, Long expireTime) {
|
||||
Date date = new Date(System.currentTimeMillis() + expireTime);
|
||||
Algorithm algorithm = Algorithm.HMAC256(secret);
|
||||
// 附带username信息
|
||||
return JWT.create().withClaim("username", username).withExpiresAt(date).sign(algorithm);
|
||||
|
||||
}
|
||||
|
||||
/**
|
||||
* 生成签名,根据客户端类型自动选择过期时间
|
||||
* for [JHHB-1030]【鉴权】移动端用户token到期后续期时间变成pc端时长
|
||||
*
|
||||
* @param username 用户名
|
||||
* @param secret 用户的密码
|
||||
* @param clientType 客户端类型(PC或APP)
|
||||
* @return 加密的token
|
||||
*/
|
||||
public static String sign(String username, String secret, String clientType) {
|
||||
// 根据客户端类型选择对应的过期时间
|
||||
long expireTime = CommonConstant.CLIENT_TYPE_APP.equalsIgnoreCase(clientType)
|
||||
? APP_EXPIRE_TIME
|
||||
: EXPIRE_TIME;
|
||||
Date date = new Date(System.currentTimeMillis() + expireTime);
|
||||
Algorithm algorithm = Algorithm.HMAC256(secret);
|
||||
// 附带username和clientType信息
|
||||
return JWT.create()
|
||||
.withClaim("username", username)
|
||||
.withClaim("clientType", clientType)
|
||||
.withExpiresAt(date)
|
||||
.sign(algorithm);
|
||||
}
|
||||
|
||||
/**
|
||||
* 从token中获取客户端类型
|
||||
* for [JHHB-1030]【鉴权】移动端用户token到期后续期时间变成pc端时长
|
||||
*
|
||||
* @param token JWT token
|
||||
* @return 客户端类型,如果不存在则返回PC(兼容旧token)
|
||||
*/
|
||||
public static String getClientType(String token) {
|
||||
try {
|
||||
DecodedJWT jwt = JWT.decode(token);
|
||||
String clientType = jwt.getClaim("clientType").asString();
|
||||
// 如果clientType为空,返回默认值PC(兼容旧token)
|
||||
return oConvertUtils.isNotEmpty(clientType) ? clientType : CommonConstant.CLIENT_TYPE_PC;
|
||||
} catch (JWTDecodeException e) {
|
||||
log.warn("解析token中的clientType失败,使用默认值PC:" + e.getMessage());
|
||||
return CommonConstant.CLIENT_TYPE_PC;
|
||||
}
|
||||
}
|
||||
|
||||
/**
|
||||
* 根据request中的token获取用户账号
|
||||
* 注意:此方法已适配Sa-Token
|
||||
*
|
||||
* @param request
|
||||
* @return
|
||||
@ -202,9 +109,9 @@ public class JwtUtil {
|
||||
}
|
||||
return username;
|
||||
}
|
||||
|
||||
|
||||
/**
|
||||
* 从session中获取变量
|
||||
* 从session中获取变量
|
||||
* @param key
|
||||
* @return
|
||||
*/
|
||||
@ -215,7 +122,7 @@ public class JwtUtil {
|
||||
String wellNumber = WELL_NUMBER;
|
||||
|
||||
if(key.indexOf(SymbolConstant.RIGHT_CURLY_BRACKET)!=-1){
|
||||
moshi = key.substring(key.indexOf("}")+1);
|
||||
moshi = key.substring(key.indexOf("}")+1);
|
||||
}
|
||||
String returnValue = null;
|
||||
if (key.contains(wellNumber)) {
|
||||
@ -229,16 +136,16 @@ public class JwtUtil {
|
||||
if(returnValue!=null){returnValue = returnValue + moshi;}
|
||||
return returnValue;
|
||||
}
|
||||
|
||||
|
||||
/**
|
||||
* 从当前用户中获取变量
|
||||
* 从当前用户中获取变量
|
||||
* @param key
|
||||
* @param user
|
||||
* @return
|
||||
*/
|
||||
public static String getUserSystemData(String key, SysUserCacheInfo user) {
|
||||
//1.优先获取 SysUserCacheInfo
|
||||
if(user==null) {
|
||||
if (user == null) {
|
||||
try {
|
||||
user = JeecgDataAutorUtils.loadUserInfo();
|
||||
} catch (Exception e) {
|
||||
@ -248,82 +155,82 @@ public class JwtUtil {
|
||||
//2.通过shiro获取登录用户信息
|
||||
LoginUser sysUser = null;
|
||||
try {
|
||||
sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
sysUser = (LoginUser) LoginUserUtils.getSessionUser();
|
||||
} catch (Exception e) {
|
||||
log.warn("SecurityUtils.getSubject() 获取用户信息异常:" + e.getMessage());
|
||||
}
|
||||
|
||||
//#{sys_user_code}%
|
||||
String moshi = "";
|
||||
String wellNumber = WELL_NUMBER;
|
||||
if(key.indexOf(SymbolConstant.RIGHT_CURLY_BRACKET)!=-1){
|
||||
moshi = key.substring(key.indexOf("}")+1);
|
||||
String wellNumber = WELL_NUMBER;
|
||||
if (key.indexOf(SymbolConstant.RIGHT_CURLY_BRACKET) != -1) {
|
||||
moshi = key.substring(key.indexOf("}") + 1);
|
||||
}
|
||||
String returnValue = null;
|
||||
//针对特殊标示处理#{sysOrgCode},判断替换
|
||||
if (key.contains(wellNumber)) {
|
||||
key = key.substring(2,key.indexOf("}"));
|
||||
key = key.substring(2, key.indexOf("}"));
|
||||
} else {
|
||||
key = key;
|
||||
}
|
||||
// 是否存在字符串标志
|
||||
boolean multiStr;
|
||||
if(oConvertUtils.isNotEmpty(key) && key.trim().matches("^\\[\\w+]$")){
|
||||
key = key.substring(1,key.length()-1);
|
||||
if (oConvertUtils.isNotEmpty(key) && key.trim().matches("^\\[\\w+]$")) {
|
||||
key = key.substring(1, key.length() - 1);
|
||||
multiStr = true;
|
||||
} else {
|
||||
multiStr = false;
|
||||
}
|
||||
multiStr = false;
|
||||
}
|
||||
//替换为当前系统时间(年月日)
|
||||
if (key.equals(DataBaseConstant.SYS_DATE)|| key.toLowerCase().equals(DataBaseConstant.SYS_DATE_TABLE)) {
|
||||
if (key.equals(DataBaseConstant.SYS_DATE) || key.toLowerCase().equals(DataBaseConstant.SYS_DATE_TABLE)) {
|
||||
returnValue = DateUtils.formatDate();
|
||||
}
|
||||
//替换为当前系统时间(年月日时分秒)
|
||||
else if (key.equals(DataBaseConstant.SYS_TIME)|| key.toLowerCase().equals(DataBaseConstant.SYS_TIME_TABLE)) {
|
||||
else if (key.equals(DataBaseConstant.SYS_TIME) || key.toLowerCase().equals(DataBaseConstant.SYS_TIME_TABLE)) {
|
||||
returnValue = DateUtils.now();
|
||||
}
|
||||
//流程状态默认值(默认未发起)
|
||||
else if (key.equals(DataBaseConstant.BPM_STATUS)|| key.toLowerCase().equals(DataBaseConstant.BPM_STATUS_TABLE)) {
|
||||
else if (key.equals(DataBaseConstant.BPM_STATUS) || key.toLowerCase().equals(DataBaseConstant.BPM_STATUS_TABLE)) {
|
||||
returnValue = "1";
|
||||
}
|
||||
|
||||
//后台任务获取用户信息异常,导致程序中断
|
||||
if(sysUser==null && user==null){
|
||||
if (sysUser == null && user == null) {
|
||||
return null;
|
||||
}
|
||||
|
||||
|
||||
//替换为系统登录用户帐号
|
||||
if (key.equals(DataBaseConstant.SYS_USER_CODE)|| key.toLowerCase().equals(DataBaseConstant.SYS_USER_CODE_TABLE)) {
|
||||
if(user==null) {
|
||||
if (key.equals(DataBaseConstant.SYS_USER_CODE) || key.toLowerCase().equals(DataBaseConstant.SYS_USER_CODE_TABLE)) {
|
||||
if (user == null) {
|
||||
returnValue = sysUser.getUsername();
|
||||
}else {
|
||||
} else {
|
||||
returnValue = user.getSysUserCode();
|
||||
}
|
||||
}
|
||||
|
||||
// 替换为系统登录用户ID
|
||||
else if (key.equals(DataBaseConstant.SYS_USER_ID) || key.equalsIgnoreCase(DataBaseConstant.SYS_USER_ID_TABLE)) {
|
||||
if(user==null) {
|
||||
if (user == null) {
|
||||
returnValue = sysUser.getId();
|
||||
}else {
|
||||
} else {
|
||||
returnValue = user.getSysUserId();
|
||||
}
|
||||
}
|
||||
|
||||
//替换为系统登录用户真实名字
|
||||
else if (key.equals(DataBaseConstant.SYS_USER_NAME)|| key.toLowerCase().equals(DataBaseConstant.SYS_USER_NAME_TABLE)) {
|
||||
if(user==null) {
|
||||
else if (key.equals(DataBaseConstant.SYS_USER_NAME) || key.toLowerCase().equals(DataBaseConstant.SYS_USER_NAME_TABLE)) {
|
||||
if (user == null) {
|
||||
returnValue = sysUser.getRealname();
|
||||
}else {
|
||||
} else {
|
||||
returnValue = user.getSysUserName();
|
||||
}
|
||||
}
|
||||
|
||||
|
||||
//替换为系统用户登录所使用的机构编码
|
||||
else if (key.equals(DataBaseConstant.SYS_ORG_CODE)|| key.toLowerCase().equals(DataBaseConstant.SYS_ORG_CODE_TABLE)) {
|
||||
if(user==null) {
|
||||
else if (key.equals(DataBaseConstant.SYS_ORG_CODE) || key.toLowerCase().equals(DataBaseConstant.SYS_ORG_CODE_TABLE)) {
|
||||
if (user == null) {
|
||||
returnValue = sysUser.getOrgCode();
|
||||
}else {
|
||||
} else {
|
||||
returnValue = user.getSysOrgCode();
|
||||
}
|
||||
}
|
||||
@ -338,19 +245,15 @@ public class JwtUtil {
|
||||
}
|
||||
|
||||
//替换为系统用户所拥有的所有机构编码
|
||||
else if (key.equals(DataBaseConstant.SYS_MULTI_ORG_CODE)|| key.toLowerCase().equals(DataBaseConstant.SYS_MULTI_ORG_CODE_TABLE)) {
|
||||
if(user==null){
|
||||
//TODO 暂时使用用户登录部门,存在逻辑缺陷,不是用户所拥有的部门
|
||||
else if (key.equals(DataBaseConstant.SYS_MULTI_ORG_CODE) || key.toLowerCase().equals(DataBaseConstant.SYS_MULTI_ORG_CODE_TABLE)) {
|
||||
if (user == null) {
|
||||
returnValue = sysUser.getOrgCode();
|
||||
// 代码逻辑说明: [QQYUN-10785]数据权限,查看自己拥有部门的权限中存在问题 #7288------------
|
||||
returnValue = multiStr ? "'" + returnValue + "'" : returnValue;
|
||||
}else{
|
||||
if(user.isOneDepart()) {
|
||||
} else {
|
||||
if (user.isOneDepart()) {
|
||||
returnValue = user.getSysMultiOrgCode().get(0);
|
||||
// 代码逻辑说明: [QQYUN-10785]数据权限,查看自己拥有部门的权限中存在问题 #7288------------
|
||||
returnValue = multiStr ? "'" + returnValue + "'" : returnValue;
|
||||
}else {
|
||||
// 代码逻辑说明: [QQYUN-10785]数据权限,查看自己拥有部门的权限中存在问题 #7288------------
|
||||
} else {
|
||||
returnValue = user.getSysMultiOrgCode().stream()
|
||||
.filter(Objects::nonNull)
|
||||
.map(orgCode -> {
|
||||
@ -374,20 +277,17 @@ public class JwtUtil {
|
||||
}
|
||||
}
|
||||
|
||||
// 代码逻辑说明: 多租户ID作为系统变量
|
||||
else if (key.equals(TenantConstant.TENANT_ID) || key.toLowerCase().equals(TenantConstant.TENANT_ID_TABLE)){
|
||||
// 多租户ID作为系统变量
|
||||
else if (key.equals(TenantConstant.TENANT_ID) || key.toLowerCase().equals(TenantConstant.TENANT_ID_TABLE)) {
|
||||
try {
|
||||
returnValue = SpringContextUtils.getHttpServletRequest().getHeader(CommonConstant.TENANT_ID);
|
||||
} catch (Exception e) {
|
||||
log.warn("获取系统租户异常:" + e.getMessage());
|
||||
}
|
||||
}
|
||||
if(returnValue!=null){returnValue = returnValue + moshi;}
|
||||
if (returnValue != null) {
|
||||
returnValue = returnValue + moshi;
|
||||
}
|
||||
return returnValue;
|
||||
}
|
||||
|
||||
// public static void main(String[] args) {
|
||||
// String token = "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJleHAiOjE1NjUzMzY1MTMsInVzZXJuYW1lIjoiYWRtaW4ifQ.xjhud_tWCNYBOg_aRlMgOdlZoWFFKB_givNElHNw3X0";
|
||||
// System.out.println(JwtUtil.getUsername(token));
|
||||
// }
|
||||
}
|
||||
|
||||
@ -0,0 +1,175 @@
|
||||
package org.jeecg.common.util;
|
||||
|
||||
import cn.dev33.satoken.stp.StpUtil;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
|
||||
/**
|
||||
* 登录用户工具类
|
||||
* 替代原有的Shiro SecurityUtils工具类
|
||||
* @author jeecg-boot
|
||||
*/
|
||||
@Slf4j
|
||||
public class LoginUserUtils {
|
||||
|
||||
/**
|
||||
* Session中存储登录用户信息的key
|
||||
*/
|
||||
private static final String SESSION_KEY_LOGIN_USER = "loginUser";
|
||||
|
||||
/**
|
||||
* 执行登录并设置用户信息到Session(推荐)
|
||||
*
|
||||
* <p>此方法会:
|
||||
* <ul>
|
||||
* <li>1. 调用 StpUtil.login(username) 生成token和session</li>
|
||||
* <li>2. 将 LoginUser 存入 Session 缓存(清除不必要的字段(密码等15个字段)</li>
|
||||
* <li>3. 返回生成的 token</li>
|
||||
* </ul>
|
||||
*
|
||||
* @param sysUser 完整的用户对象(从数据库查询得到)
|
||||
* @return 生成的 token
|
||||
*/
|
||||
public static String doLogin(LoginUser sysUser) {
|
||||
if (sysUser == null) {
|
||||
throw new IllegalArgumentException("用户对象不能为空");
|
||||
}
|
||||
|
||||
try {
|
||||
// 1. 获取 username
|
||||
String username = sysUser.getUsername();
|
||||
|
||||
if (username == null || username.trim().isEmpty()) {
|
||||
throw new IllegalArgumentException("用户名不能为空");
|
||||
}
|
||||
|
||||
// 2. Sa-Token 登录(使用 username 作为 loginId)
|
||||
StpUtil.login(username);
|
||||
|
||||
// 3. 用户信息到 LoginUser 并存入 Session
|
||||
setSessionUser(sysUser);
|
||||
|
||||
// 4. 返回生成的 token
|
||||
return StpUtil.getTokenValue();
|
||||
|
||||
} catch (Exception e) {
|
||||
throw new RuntimeException("登录失败: " + e.getMessage(), e);
|
||||
}
|
||||
}
|
||||
|
||||
/**
|
||||
* 获取当前登录用户信息
|
||||
*
|
||||
* <p>说明:
|
||||
* <ul>
|
||||
* <li>对于需要认证的接口:Sa-Token Filter 已经校验过登录状态,此方法必然能获取到用户</li>
|
||||
* <li>对于已排除拦截的接口:如果未登录或获取失败则返回 null,由业务代码自行判断处理</li>
|
||||
* </ul>
|
||||
*
|
||||
* @return 登录用户对象,如果未登录或session中没有则返回null
|
||||
*/
|
||||
public static LoginUser getSessionUser() {
|
||||
// 尝试从Sa-Token的Session中获取用户信息
|
||||
Object loginUser = StpUtil.getSession().get(SESSION_KEY_LOGIN_USER);
|
||||
if (loginUser instanceof LoginUser) {
|
||||
return (LoginUser) loginUser;
|
||||
}
|
||||
return null;
|
||||
}
|
||||
|
||||
/**
|
||||
* 根据指定的 token 获取登录用户信息
|
||||
*
|
||||
* <p>适用场景:已排除拦截的接口(如 WebSocket),需要显式传入 token 来获取用户信息
|
||||
*
|
||||
* <p>实现方式:临时切换到该 token 对应的会话,然后获取用户信息
|
||||
*
|
||||
* @param token JWT token
|
||||
* @return 登录用户对象,如果 token 无效或session中没有则返回null
|
||||
*/
|
||||
public static LoginUser getSessionUser(String token) {
|
||||
try {
|
||||
// 根据 token 获取登录ID
|
||||
Object loginId = StpUtil.getLoginIdByToken(token);
|
||||
if (loginId == null) {
|
||||
return null;
|
||||
}
|
||||
|
||||
// 临时切换到该 token 对应的登录会话
|
||||
StpUtil.switchTo(loginId);
|
||||
|
||||
// 直接调用无参方法获取用户信息
|
||||
return getSessionUser();
|
||||
|
||||
} catch (Exception e) {
|
||||
log.debug("根据token获取用户信息失败: {}", e.getMessage());
|
||||
return null;
|
||||
}
|
||||
}
|
||||
|
||||
|
||||
/**
|
||||
* 设置当前登录用户信息到Session
|
||||
*
|
||||
* <p>为减少 Redis 存储和保障安全,只保留必要的核心字段:
|
||||
* <ul>
|
||||
* <li>id, username, realname - 基础用户信息</li>
|
||||
* <li>orgCode, orgId, departIds - 部门和数据权限</li>
|
||||
* <li>roleCode - 角色权限</li>
|
||||
* <li>loginTenantId, relTenantIds - 多租户</li>
|
||||
* <li>avatar - 用户头像</li>
|
||||
* </ul>
|
||||
*
|
||||
* <p>⚠️ 注意:调用此方法前需要先调用 StpUtil.login()
|
||||
*
|
||||
* @param loginUser 登录用户对象
|
||||
*/
|
||||
public static void setSessionUser(LoginUser loginUser) {
|
||||
if (loginUser == null) {
|
||||
return;
|
||||
}
|
||||
|
||||
// ⚠️ 安全与性能:清除不必要的字段,减少 Redis 存储
|
||||
loginUser.setPassword(null); // 密码(安全)
|
||||
loginUser.setWorkNo(null); // 工号
|
||||
loginUser.setBirthday(null); // 生日
|
||||
loginUser.setSex(null); // 性别
|
||||
loginUser.setEmail(null); // 邮箱
|
||||
loginUser.setPhone(null); // 手机号
|
||||
loginUser.setStatus(null); // 状态
|
||||
loginUser.setDelFlag(null); // 删除标志
|
||||
loginUser.setActivitiSync(null); // 工作流同步
|
||||
loginUser.setCreateTime(null); // 创建时间
|
||||
loginUser.setUserIdentity(null); // 用户身份
|
||||
loginUser.setPost(null); // 职务
|
||||
loginUser.setTelephone(null); // 座机
|
||||
loginUser.setRelTenantIds(null); // 关联租户
|
||||
loginUser.setMainDepPostId(null); // 主岗位
|
||||
|
||||
StpUtil.getSession().set(SESSION_KEY_LOGIN_USER, loginUser);
|
||||
}
|
||||
|
||||
/**
|
||||
* 获取当前登录用户名(推荐使用此方法,语义更清晰)
|
||||
* @return 用户名(username)
|
||||
*/
|
||||
public static String getUsername() {
|
||||
return StpUtil.getLoginIdAsString();
|
||||
}
|
||||
|
||||
/**
|
||||
* 检查是否已登录
|
||||
* @return true-已登录,false-未登录
|
||||
*/
|
||||
public static boolean isLogin() {
|
||||
return StpUtil.isLogin();
|
||||
}
|
||||
|
||||
/**
|
||||
* 退出登录
|
||||
*/
|
||||
public static void logout() {
|
||||
StpUtil.logout();
|
||||
}
|
||||
}
|
||||
|
||||
@ -1,37 +0,0 @@
|
||||
package org.jeecg.common.util;
|
||||
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.apache.shiro.mgt.SecurityManager;
|
||||
import org.apache.shiro.subject.Subject;
|
||||
import org.apache.shiro.util.ThreadContext;
|
||||
|
||||
import java.util.concurrent.*;
|
||||
|
||||
/**
|
||||
* @date 2025-09-04
|
||||
* @author scott
|
||||
*
|
||||
* @Description: 支持shiro的API,获取当前登录人方法的线程池
|
||||
*/
|
||||
public class ShiroThreadPoolExecutor extends ThreadPoolExecutor {
|
||||
|
||||
public ShiroThreadPoolExecutor(int corePoolSize, int maximumPoolSize, long keepAliveTime, TimeUnit unit, BlockingQueue<Runnable> workQueue) {
|
||||
super(corePoolSize, maximumPoolSize, keepAliveTime, unit, workQueue);
|
||||
}
|
||||
|
||||
@Override
|
||||
public void execute(Runnable command) {
|
||||
Subject subject = SecurityUtils.getSubject();
|
||||
SecurityManager securityManager = SecurityUtils.getSecurityManager();
|
||||
super.execute(() -> {
|
||||
try {
|
||||
ThreadContext.bind(securityManager);
|
||||
ThreadContext.bind(subject);
|
||||
command.run();
|
||||
} finally {
|
||||
ThreadContext.unbindSubject();
|
||||
ThreadContext.unbindSecurityManager();
|
||||
}
|
||||
});
|
||||
}
|
||||
}
|
||||
@ -1,5 +1,6 @@
|
||||
package org.jeecg.common.util;
|
||||
|
||||
import cn.dev33.satoken.stp.StpUtil;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.commons.lang3.StringUtils;
|
||||
import org.jeecg.common.api.CommonAPI;
|
||||
@ -87,75 +88,42 @@ public class TokenUtils {
|
||||
}
|
||||
|
||||
/**
|
||||
* 验证Token
|
||||
* 验证Token(已重写为Sa-Token实现)
|
||||
*/
|
||||
public static boolean verifyToken(HttpServletRequest request, CommonAPI commonApi, RedisUtil redisUtil) {
|
||||
public static boolean verifyToken(HttpServletRequest request, CommonAPI commonApi) {
|
||||
log.debug(" -- url --" + request.getRequestURL());
|
||||
String token = getTokenByRequest(request);
|
||||
return TokenUtils.verifyToken(token, commonApi, redisUtil);
|
||||
return TokenUtils.verifyToken(token, commonApi);
|
||||
}
|
||||
|
||||
/**
|
||||
* 验证Token
|
||||
* 验证Token(已重写为Sa-Token实现)
|
||||
*/
|
||||
public static boolean verifyToken(String token, CommonAPI commonApi, RedisUtil redisUtil) {
|
||||
public static boolean verifyToken(String token, CommonAPI commonApi) {
|
||||
if (StringUtils.isBlank(token)) {
|
||||
throw new JeecgBoot401Exception("token不能为空!");
|
||||
}
|
||||
|
||||
// 解密获得username,用于和数据库进行对比
|
||||
String username = JwtUtil.getUsername(token);
|
||||
// 使用Sa-Token校验token
|
||||
Object username = StpUtil.getLoginIdByToken(token);
|
||||
if (username == null) {
|
||||
throw new JeecgBoot401Exception("token非法无效!");
|
||||
}
|
||||
|
||||
// 查询用户信息
|
||||
LoginUser user = TokenUtils.getLoginUser(username, commonApi, redisUtil);
|
||||
//LoginUser user = commonApi.getUserByName(username);
|
||||
LoginUser user = commonApi.getUserByName(username.toString());
|
||||
if (user == null) {
|
||||
throw new JeecgBoot401Exception("用户不存在!");
|
||||
}
|
||||
|
||||
// 判断用户状态
|
||||
if (user.getStatus() != 1) {
|
||||
throw new JeecgBoot401Exception("账号已被锁定,请联系管理员!");
|
||||
}
|
||||
// 校验token是否超时失效 & 或者账号密码是否错误
|
||||
if (!jwtTokenRefresh(token, username, user.getPassword(), redisUtil)) {
|
||||
// 用户登录Token过期提示信息
|
||||
String userLoginTokenErrorMsg = oConvertUtils.getString(redisUtil.get(CommonConstant.PREFIX_USER_TOKEN_ERROR_MSG + token));
|
||||
throw new JeecgBoot401Exception(oConvertUtils.isEmpty(userLoginTokenErrorMsg)? CommonConstant.TOKEN_IS_INVALID_MSG: userLoginTokenErrorMsg);
|
||||
}
|
||||
|
||||
return true;
|
||||
}
|
||||
|
||||
/**
|
||||
* 刷新token(保证用户在线操作不掉线)
|
||||
* @param token
|
||||
* @param userName
|
||||
* @param passWord
|
||||
* @param redisUtil
|
||||
* @return
|
||||
*/
|
||||
private static boolean jwtTokenRefresh(String token, String userName, String passWord, RedisUtil redisUtil) {
|
||||
String cacheToken = oConvertUtils.getString(redisUtil.get(CommonConstant.PREFIX_USER_TOKEN + token));
|
||||
if (oConvertUtils.isNotEmpty(cacheToken)) {
|
||||
// 校验token有效性
|
||||
if (!JwtUtil.verify(cacheToken, userName, passWord)) {
|
||||
// 从token中解析客户端类型,保持续期时使用相同的客户端类型
|
||||
String clientType = JwtUtil.getClientType(token);
|
||||
String newAuthorization = JwtUtil.sign(userName, passWord, clientType);
|
||||
// 根据客户端类型设置对应的缓存有效时间
|
||||
long expireTime = CommonConstant.CLIENT_TYPE_APP.equalsIgnoreCase(clientType)
|
||||
? JwtUtil.APP_EXPIRE_TIME * 2 / 1000
|
||||
: JwtUtil.EXPIRE_TIME * 2 / 1000;
|
||||
redisUtil.set(CommonConstant.PREFIX_USER_TOKEN + token, newAuthorization);
|
||||
redisUtil.expire(CommonConstant.PREFIX_USER_TOKEN + token, expireTime);
|
||||
}
|
||||
return true;
|
||||
}
|
||||
return false;
|
||||
}
|
||||
|
||||
/**
|
||||
* 获取登录用户
|
||||
*
|
||||
@ -181,4 +149,5 @@ public class TokenUtils {
|
||||
}
|
||||
return loginUser;
|
||||
}
|
||||
|
||||
}
|
||||
|
||||
@ -1,12 +1,13 @@
|
||||
package org.jeecg.common.util.encryption;
|
||||
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.lang.codec.Base64;
|
||||
import org.jeecg.common.util.oConvertUtils;
|
||||
|
||||
import javax.crypto.Cipher;
|
||||
import javax.crypto.spec.IvParameterSpec;
|
||||
import javax.crypto.spec.SecretKeySpec;
|
||||
import java.nio.charset.StandardCharsets;
|
||||
import java.util.Base64;
|
||||
|
||||
/**
|
||||
* AES 工具 (兼容历史 NoPadding + 新 PKCS5Padding)
|
||||
@ -23,7 +24,7 @@ public class AesEncryptUtil {
|
||||
SecretKeySpec ks = new SecretKeySpec(KEY.getBytes(StandardCharsets.UTF_8), "AES");
|
||||
IvParameterSpec ivSpec = new IvParameterSpec(IV.getBytes(StandardCharsets.UTF_8));
|
||||
cipher.init(Cipher.DECRYPT_MODE, ks, ivSpec);
|
||||
byte[] plain = cipher.doFinal(Base64.decode(cipherBase64));
|
||||
byte[] plain = cipher.doFinal(Base64.getDecoder().decode(cipherBase64));
|
||||
return new String(plain, StandardCharsets.UTF_8);
|
||||
}
|
||||
|
||||
@ -33,7 +34,7 @@ public class AesEncryptUtil {
|
||||
SecretKeySpec ks = new SecretKeySpec(KEY.getBytes(StandardCharsets.UTF_8), "AES");
|
||||
IvParameterSpec ivSpec = new IvParameterSpec(IV.getBytes(StandardCharsets.UTF_8));
|
||||
cipher.init(Cipher.DECRYPT_MODE, ks, ivSpec);
|
||||
byte[] data = cipher.doFinal(Base64.decode(cipherBase64));
|
||||
byte[] data = cipher.doFinal(Base64.getDecoder().decode(cipherBase64));
|
||||
return new String(data, StandardCharsets.UTF_8)
|
||||
.replace("\u0000",""); // 旧填充 0
|
||||
}
|
||||
@ -93,7 +94,7 @@ public class AesEncryptUtil {
|
||||
IvParameterSpec ivspec = new IvParameterSpec(IV.getBytes(StandardCharsets.UTF_8));
|
||||
cipher.init(Cipher.ENCRYPT_MODE, keyspec, ivspec);
|
||||
byte[] encrypted = cipher.doFinal(plaintext);
|
||||
return Base64.encodeToString(encrypted);
|
||||
return Base64.getEncoder().encodeToString(encrypted);
|
||||
}catch(Exception e){
|
||||
throw new IllegalStateException("legacy encrypt error", e);
|
||||
}
|
||||
|
||||
@ -24,23 +24,18 @@ public class WebsocketFilter implements Filter {
|
||||
|
||||
private static CommonAPI commonApi;
|
||||
|
||||
private static RedisUtil redisUtil;
|
||||
|
||||
@Override
|
||||
public void doFilter(ServletRequest servletRequest, ServletResponse servletResponse, FilterChain filterChain) throws IOException, ServletException {
|
||||
if (commonApi == null) {
|
||||
commonApi = SpringContextUtils.getBean(CommonAPI.class);
|
||||
}
|
||||
if (redisUtil == null) {
|
||||
redisUtil = SpringContextUtils.getBean(RedisUtil.class);
|
||||
}
|
||||
HttpServletRequest request = (HttpServletRequest)servletRequest;
|
||||
String token = request.getHeader(TOKEN_KEY);
|
||||
|
||||
log.debug("Websocket连接 Token安全校验,Path = {},token:{}", request.getRequestURI(), token);
|
||||
|
||||
try {
|
||||
TokenUtils.verifyToken(token, commonApi, redisUtil);
|
||||
TokenUtils.verifyToken(token, commonApi);
|
||||
} catch (Exception exception) {
|
||||
//log.error("Websocket连接 Token安全校验失败,IP:{}, Token:{}, Path = {},异常:{}", oConvertUtils.getIpAddrByRequest(request), token, request.getRequestURI(), exception.getMessage());
|
||||
log.debug("Websocket连接 Token安全校验失败,IP:{}, Token:{}, Path = {},异常:{}", oConvertUtils.getIpAddrByRequest(request), token, request.getRequestURI(), exception.getMessage());
|
||||
|
||||
@ -2,7 +2,7 @@ package org.jeecg.config.firewall.interceptor;
|
||||
|
||||
import com.alibaba.fastjson.JSON;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.api.CommonAPI;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
@ -68,7 +68,7 @@ public class LowCodeModeInterceptor implements HandlerInterceptor {
|
||||
if (jeecgBaseConfig.getFirewall()!=null && LowCodeModeInterceptor.LOW_CODE_MODE_PROD.equals(jeecgBaseConfig.getFirewall().getLowCodeMode())) {
|
||||
String requestURI = request.getRequestURI().substring(request.getContextPath().length());
|
||||
log.info("低代码模式,拦截请求路径:" + requestURI);
|
||||
LoginUser loginUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser loginUser = LoginUserUtils.getSessionUser();
|
||||
Set<String> hasRoles = null;
|
||||
if (loginUser == null) {
|
||||
loginUser = commonAPI.getUserByName(JwtUtil.getUserNameByToken(SpringContextUtils.getHttpServletRequest()));
|
||||
|
||||
@ -6,7 +6,7 @@ import org.apache.ibatis.executor.Executor;
|
||||
import org.apache.ibatis.mapping.MappedStatement;
|
||||
import org.apache.ibatis.mapping.SqlCommandType;
|
||||
import org.apache.ibatis.plugin.*;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.config.TenantContext;
|
||||
import org.jeecg.common.constant.TenantConstant;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
@ -189,7 +189,7 @@ public class MybatisInterceptor implements Interceptor {
|
||||
private LoginUser getLoginUser() {
|
||||
LoginUser sysUser = null;
|
||||
try {
|
||||
sysUser = SecurityUtils.getSubject().getPrincipal() != null ? (LoginUser) SecurityUtils.getSubject().getPrincipal() : null;
|
||||
sysUser = LoginUserUtils.getSessionUser() != null ? LoginUserUtils.getSessionUser() : null;
|
||||
} catch (Exception e) {
|
||||
//e.printStackTrace();
|
||||
sysUser = null;
|
||||
|
||||
@ -1,4 +1,4 @@
|
||||
package org.jeecg.config.shiro;
|
||||
package org.jeecg.config.satoken;
|
||||
|
||||
import java.lang.annotation.ElementType;
|
||||
import java.lang.annotation.Retention;
|
||||
@ -16,3 +16,4 @@ import java.lang.annotation.Target;
|
||||
@Retention(RetentionPolicy.RUNTIME)
|
||||
public @interface IgnoreAuth {
|
||||
}
|
||||
|
||||
@ -0,0 +1,420 @@
|
||||
package org.jeecg.config.satoken;
|
||||
|
||||
import cn.dev33.satoken.context.SaHolder;
|
||||
import cn.dev33.satoken.context.model.SaRequest;
|
||||
import cn.dev33.satoken.exception.NotLoginException;
|
||||
import cn.dev33.satoken.filter.SaServletFilter;
|
||||
import cn.dev33.satoken.interceptor.SaInterceptor;
|
||||
import cn.dev33.satoken.jwt.StpLogicJwtForSimple;
|
||||
import cn.dev33.satoken.router.SaHttpMethod;
|
||||
import cn.dev33.satoken.router.SaRouter;
|
||||
import cn.dev33.satoken.stp.StpLogic;
|
||||
import cn.dev33.satoken.stp.StpUtil;
|
||||
import jakarta.annotation.Resource;
|
||||
import jakarta.servlet.DispatcherType;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.jeecg.common.api.CommonAPI;
|
||||
import org.jeecg.common.config.TenantContext;
|
||||
import org.jeecg.common.constant.CacheConstant;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.jeecg.common.util.*;
|
||||
import org.jeecg.config.JeecgBaseConfig;
|
||||
import org.jeecg.config.mybatis.MybatisPlusSaasConfig;
|
||||
import org.jeecg.config.satoken.ignore.InMemoryIgnoreAuth;
|
||||
import org.springframework.beans.factory.annotation.Autowired;
|
||||
import org.springframework.beans.factory.config.BeanDefinition;
|
||||
import org.springframework.boot.web.servlet.FilterRegistrationBean;
|
||||
import org.springframework.context.annotation.Bean;
|
||||
import org.springframework.context.annotation.Configuration;
|
||||
import org.springframework.context.annotation.Primary;
|
||||
import org.springframework.context.annotation.Role;
|
||||
import org.springframework.core.env.Environment;
|
||||
import org.springframework.http.HttpHeaders;
|
||||
import org.springframework.http.HttpStatus;
|
||||
import org.springframework.web.servlet.config.annotation.InterceptorRegistry;
|
||||
import org.springframework.web.servlet.config.annotation.WebMvcConfigurer;
|
||||
|
||||
import java.util.ArrayList;
|
||||
import java.util.Arrays;
|
||||
import java.util.List;
|
||||
|
||||
/**
|
||||
* @author: jeecg-boot
|
||||
* @description: Sa-Token 配置类
|
||||
*/
|
||||
@Slf4j
|
||||
@Configuration
|
||||
@Role(BeanDefinition.ROLE_INFRASTRUCTURE)
|
||||
public class SaTokenConfig implements WebMvcConfigurer {
|
||||
|
||||
@Resource
|
||||
private JeecgBaseConfig jeecgBaseConfig;
|
||||
@Autowired
|
||||
private Environment env;
|
||||
@Autowired
|
||||
private CommonAPI commonAPI;
|
||||
@Autowired
|
||||
private RedisUtil redisUtil;
|
||||
|
||||
/**
|
||||
* Sa-Token 整合 jwt (Simple 模式)
|
||||
* 使用JWT-Simple模式生成标准JWT格式的token
|
||||
* 并支持从URL参数"token"读取token(兼容原系统)
|
||||
*/
|
||||
@Bean
|
||||
@Primary
|
||||
public StpLogic getStpLogicJwt() {
|
||||
return new StpLogicJwtForSimple() {
|
||||
/**
|
||||
* 获取当前请求的 Token 值
|
||||
* 优先级:Header > URL参数token > URL参数X-Access-Token
|
||||
*/
|
||||
@Override
|
||||
public String getTokenValue() {
|
||||
try {
|
||||
SaRequest request = SaHolder.getRequest();
|
||||
|
||||
// 1. 优先从Header中获取
|
||||
String tokenValue = request.getHeader(getConfigOrGlobal().getTokenName());
|
||||
if (oConvertUtils.isNotEmpty(tokenValue)) {
|
||||
return tokenValue;
|
||||
}
|
||||
|
||||
// 2. 从URL参数"token"获取(兼容原系统)
|
||||
tokenValue = request.getParam("token");
|
||||
if (oConvertUtils.isNotEmpty(tokenValue)) {
|
||||
return tokenValue;
|
||||
}
|
||||
|
||||
// 3. 从URL参数"X-Access-Token"获取
|
||||
tokenValue = request.getParam(getConfigOrGlobal().getTokenName());
|
||||
if (oConvertUtils.isNotEmpty(tokenValue)) {
|
||||
return tokenValue;
|
||||
}
|
||||
} catch (Exception e) {
|
||||
log.debug("获取token失败: {}", e.getMessage());
|
||||
}
|
||||
|
||||
// 4. 如果都没有,使用默认逻辑
|
||||
return super.getTokenValue();
|
||||
}
|
||||
};
|
||||
}
|
||||
|
||||
/**
|
||||
* 注册 Sa-Token 拦截器,打开注解式鉴权功能
|
||||
*/
|
||||
@Override
|
||||
public void addInterceptors(InterceptorRegistry registry) {
|
||||
// 注册 Sa-Token 拦截器,打开注解式鉴权功能
|
||||
registry.addInterceptor(new SaInterceptor()).addPathPatterns("/**");
|
||||
}
|
||||
|
||||
/**
|
||||
* 注册 Sa-Token 全局过滤器
|
||||
*/
|
||||
@Bean
|
||||
public SaServletFilter getSaServletFilter() {
|
||||
return new SaServletFilter()
|
||||
// 指定 [拦截路由] 与 [放行路由]
|
||||
.addInclude("/**")
|
||||
.setExcludeList(getExcludeUrls())
|
||||
// 认证函数: 每次请求执行
|
||||
.setAuth(obj -> {
|
||||
// 检查是否是免认证路径
|
||||
String servletPath = SaHolder.getRequest().getRequestPath();
|
||||
if (InMemoryIgnoreAuth.contains(servletPath)) {
|
||||
return;
|
||||
}
|
||||
|
||||
// 校验 token:如果请求中带有 token,先切换到对应的登录会话再校验
|
||||
try {
|
||||
String token = StpUtil.getTokenValue();
|
||||
if (oConvertUtils.isNotEmpty(token)) {
|
||||
// 根据 token 获取 loginId 并切换到对应的登录会话
|
||||
Object loginId = StpUtil.getLoginIdByToken(token);
|
||||
if (loginId != null) {
|
||||
StpUtil.switchTo(loginId);
|
||||
|
||||
// 需要手工自动续签,默认参数auto-renew:true 不好使
|
||||
long activeTimeout = StpUtil.stpLogic.getConfigOrGlobal().getActiveTimeout();
|
||||
if (activeTimeout > 0) {
|
||||
// 获取当前token的活跃剩余时间
|
||||
long tokenActiveTimeout = StpUtil.getTokenActiveTimeout();
|
||||
|
||||
// 如果剩余活跃时间少于总活跃时间的一半,进行续签
|
||||
if (tokenActiveTimeout > 0 && tokenActiveTimeout < (activeTimeout / 2)) {
|
||||
StpUtil.stpLogic.updateLastActiveToNow(token);
|
||||
log.info("【Sa-Token拦截器】Token续签成功,剩余活跃时间: {}秒", tokenActiveTimeout);
|
||||
}
|
||||
}
|
||||
|
||||
}
|
||||
}
|
||||
} catch (Exception e) {
|
||||
// 如果获取 loginId 失败,说明 token 无效或未登录,让 checkLogin 抛出异常
|
||||
log.debug("切换登录会话失败: {}", e.getMessage());
|
||||
}
|
||||
|
||||
// 最终校验登录状态
|
||||
StpUtil.checkLogin();
|
||||
|
||||
// 租户校验逻辑
|
||||
checkTenantAuthorization();
|
||||
})
|
||||
// 异常处理函数:每次认证函数发生异常时执行此函数
|
||||
.setError(e -> {
|
||||
log.warn("Sa-Token 认证失败:用户未登录或token无效");
|
||||
log.warn("请求路径: {}, Method: {},Token: {}", SaHolder.getRequest().getRequestPath(), SaHolder.getRequest().getMethod(), StpUtil.getTokenValue());
|
||||
|
||||
// 返回401状态码
|
||||
SaHolder.getResponse().setStatus(401).setHeader("Content-Type", "application/json;charset=UTF-8");
|
||||
return org.jeecg.common.system.util.JwtUtil.responseErrorJson(401, CommonConstant.TOKEN_IS_INVALID_MSG);
|
||||
})
|
||||
// 前置函数:在每次认证函数之前执行(BeforeAuth 不受 includeList 与 excludeList 的限制,所有请求都会进入)
|
||||
.setBeforeAuth(r -> {
|
||||
// 设置跨域配置
|
||||
Object cloudServer = env.getProperty(CommonConstant.CLOUD_SERVER_KEY);
|
||||
// 如果cloudServer为空 则说明是单体 需要加载跨域配置【微服务跨域切换】
|
||||
if (cloudServer == null) {
|
||||
SaHolder.getResponse()
|
||||
// 允许指定域访问跨域资源
|
||||
.setHeader(HttpHeaders.ACCESS_CONTROL_ALLOW_ORIGIN, SaHolder.getRequest().getHeader(HttpHeaders.ORIGIN))
|
||||
// 允许所有请求方式
|
||||
.setHeader(HttpHeaders.ACCESS_CONTROL_ALLOW_METHODS, "GET, POST, PUT, DELETE, OPTIONS")
|
||||
// 有效时间
|
||||
.setHeader(HttpHeaders.ACCESS_CONTROL_MAX_AGE, "3600")
|
||||
// 允许的header参数
|
||||
.setHeader(HttpHeaders.ACCESS_CONTROL_ALLOW_HEADERS, SaHolder.getRequest().getHeader(HttpHeaders.ACCESS_CONTROL_REQUEST_HEADERS))
|
||||
// 允许携带凭证
|
||||
.setHeader(HttpHeaders.ACCESS_CONTROL_ALLOW_CREDENTIALS, "true");
|
||||
}
|
||||
|
||||
// OPTIONS预检请求,直接返回
|
||||
SaRouter.match(SaHttpMethod.OPTIONS).free(r2 -> {
|
||||
SaHolder.getResponse().setStatus(HttpStatus.OK.value());
|
||||
});
|
||||
|
||||
// 设置当前线程上下文的租户ID
|
||||
String tenantId = SaHolder.getRequest().getHeader(CommonConstant.TENANT_ID);
|
||||
TenantContext.setTenant(tenantId);
|
||||
log.debug("===【TenantContext 线程设置】=== 请求路径: {}, 租户ID: {}", SaHolder.getRequest().getRequestPath(), tenantId);
|
||||
});
|
||||
}
|
||||
|
||||
/**
|
||||
* spring过滤装饰器 <br/>
|
||||
* 支持异步请求的过滤器装饰
|
||||
*/
|
||||
@Bean
|
||||
public FilterRegistrationBean<SaServletFilter> saTokenFilterRegistration() {
|
||||
FilterRegistrationBean<SaServletFilter> registration = new FilterRegistrationBean<>();
|
||||
registration.setFilter(getSaServletFilter());
|
||||
registration.setName("SaServletFilter");
|
||||
// 支持异步请求
|
||||
registration.setDispatcherTypes(DispatcherType.REQUEST, DispatcherType.ASYNC);
|
||||
// 拦截所有请求
|
||||
registration.addUrlPatterns("/*");
|
||||
registration.setOrder(1);
|
||||
registration.setAsyncSupported(true); // 支持异步请求
|
||||
return registration;
|
||||
}
|
||||
|
||||
/**
|
||||
* 获取排除URL列表
|
||||
*/
|
||||
private List<String> getExcludeUrls() {
|
||||
List<String> excludeUrls = new ArrayList<>();
|
||||
|
||||
// 支持yml方式,配置拦截排除
|
||||
if (jeecgBaseConfig != null && jeecgBaseConfig.getShiro() != null) {
|
||||
String shiroExcludeUrls = jeecgBaseConfig.getShiro().getExcludeUrls();
|
||||
if (oConvertUtils.isNotEmpty(shiroExcludeUrls)) {
|
||||
String[] permissionUrl = shiroExcludeUrls.split(",");
|
||||
excludeUrls.addAll(Arrays.asList(permissionUrl));
|
||||
}
|
||||
}
|
||||
|
||||
// 添加默认排除路径
|
||||
excludeUrls.addAll(Arrays.asList(
|
||||
"/sys/cas/client/validateLogin", // cas验证登录
|
||||
"/sys/randomImage/**", // 登录验证码接口排除
|
||||
"/sys/checkCaptcha", // 登录验证码接口排除
|
||||
"/sys/smsCheckCaptcha", // 短信次数发送太多验证码排除
|
||||
"/sys/login", // 登录接口排除
|
||||
"/sys/mLogin", // 登录接口排除
|
||||
"/sys/logout", // 登出接口排除
|
||||
"/sys/thirdLogin/**", // 第三方登录
|
||||
"/sys/getEncryptedString", // 获取加密串
|
||||
"/sys/sms", // 短信验证码
|
||||
"/sys/phoneLogin", // 手机登录
|
||||
"/sys/user/checkOnlyUser", // 校验用户是否存在
|
||||
"/sys/user/register", // 用户注册
|
||||
"/sys/user/phoneVerification", // 用户忘记密码验证手机号
|
||||
"/sys/user/passwordChange", // 用户更改密码
|
||||
"/auth/2step-code", // 登录验证码
|
||||
"/sys/common/static/**", // 图片预览 & 下载文件不限制token
|
||||
"/sys/common/pdf/**", // pdf预览
|
||||
"/generic/**", // pdf预览需要文件
|
||||
"/sys/getLoginQrcode/**", // 登录二维码
|
||||
"/sys/getQrcodeToken/**", // 监听扫码
|
||||
"/sys/checkAuth", // 授权接口排除
|
||||
"/openapi/call/**", // 开放平台接口排除
|
||||
|
||||
// 排除静态资源后缀
|
||||
"/",
|
||||
"/doc.html",
|
||||
"**/*.js",
|
||||
"**/*.css",
|
||||
"**/*.html",
|
||||
"**/*.svg",
|
||||
"**/*.pdf",
|
||||
"**/*.jpg",
|
||||
"**/*.png",
|
||||
"**/*.gif",
|
||||
"**/*.ico",
|
||||
"**/*.ttf",
|
||||
"**/*.woff",
|
||||
"**/*.woff2",
|
||||
"**/*.glb",
|
||||
"**/*.wasm",
|
||||
"**/*.js.map",
|
||||
"**/*.css.map",
|
||||
|
||||
"/druid/**",
|
||||
"/swagger-ui.html",
|
||||
"/swagger*/**",
|
||||
"/webjars/**",
|
||||
"/v3/**",
|
||||
|
||||
// 排除消息通告查看详情页面(用于第三方APP)
|
||||
"/sys/annountCement/show/**",
|
||||
|
||||
// 积木报表和积木BI排除
|
||||
"/jmreport/**",
|
||||
"/drag/lib/**",
|
||||
"/drag/list/**",
|
||||
"/drag/favicon.ico",
|
||||
"/drag/view",
|
||||
"/drag/page/queryById",
|
||||
"/drag/page/addVisitsNumber",
|
||||
"/drag/page/queryTemplateList",
|
||||
"/drag/share/view/**",
|
||||
"/drag/onlDragDatasetHead/getAllChartData",
|
||||
"/drag/onlDragDatasetHead/getTotalData",
|
||||
"/drag/onlDragDatasetHead/getMapDataByCode",
|
||||
"/drag/onlDragDatasetHead/getTotalDataByCompId",
|
||||
"/drag/mock/json/**",
|
||||
"/drag/onlDragDatasetHead/getDictByCodes",
|
||||
"/drag/onlDragDatasetHead/queryAllById",
|
||||
"/jimubi/view",
|
||||
"/jimubi/share/view/**",
|
||||
|
||||
// 大屏模板例子
|
||||
"/test/bigScreen/**",
|
||||
"/bigscreen/template1/**",
|
||||
"/bigscreen/template2/**",
|
||||
|
||||
// websocket排除
|
||||
"/websocket/**", // 系统通知和公告
|
||||
"/newsWebsocket/**", // CMS模块
|
||||
"/vxeSocket/**", // JVxeTable无痕刷新示例
|
||||
"/dragChannelSocket/**", // 仪表盘(按钮通信)
|
||||
|
||||
// App vue3版本查询版本接口
|
||||
"/sys/version/app3version",
|
||||
|
||||
// 测试模块排除
|
||||
"/test/seata/**",
|
||||
|
||||
// 错误路径排除
|
||||
"/error",
|
||||
|
||||
// 企业微信证书排除
|
||||
"/WW_verify*"
|
||||
));
|
||||
|
||||
return excludeUrls;
|
||||
}
|
||||
|
||||
/**
|
||||
* 校验用户的tenant_id和前端传过来的是否一致
|
||||
*
|
||||
* <p>实现逻辑:
|
||||
* <ul>
|
||||
* <li>1. 获取当前登录用户信息</li>
|
||||
* <li>2. 检查用户是否配置了租户信息</li>
|
||||
* <li>3. 获取前端请求头中的租户ID</li>
|
||||
* <li>4. 校验用户所属租户中是否包含当前请求的租户ID</li>
|
||||
* <li>5. 如果校验失败,从数据库重新查询用户信息并再次校验</li>
|
||||
* <li>6. 最终校验失败则抛出异常</li>
|
||||
* </ul>
|
||||
*
|
||||
* @throws NotLoginException 租户授权变更异常
|
||||
*/
|
||||
private void checkTenantAuthorization() {
|
||||
log.debug("------ 租户校验开始 ------");
|
||||
// 如果未开启租户控制,直接返回
|
||||
if (!MybatisPlusSaasConfig.OPEN_SYSTEM_TENANT_CONTROL) {
|
||||
return;
|
||||
}
|
||||
|
||||
try {
|
||||
// 获取当前登录用户信息
|
||||
LoginUser loginUser = TokenUtils.getLoginUser(LoginUserUtils.getUsername(), commonAPI, redisUtil);
|
||||
if (loginUser == null) {
|
||||
return;
|
||||
}
|
||||
|
||||
String username = loginUser.getUsername();
|
||||
String userTenantIds = loginUser.getRelTenantIds();
|
||||
|
||||
// 如果用户未配置租户信息,直接返回
|
||||
if (oConvertUtils.isEmpty(userTenantIds)) {
|
||||
return;
|
||||
}
|
||||
|
||||
// 获取前端请求头中的租户ID
|
||||
String loginTenantId = TokenUtils.getTenantIdByRequest(SpringContextUtils.getHttpServletRequest());
|
||||
log.info("登录租户:{}", loginTenantId);
|
||||
log.info("用户拥有那些租户:{}", userTenantIds);
|
||||
|
||||
// 登录用户无租户,前端header中租户ID值为 0
|
||||
String str = "0";
|
||||
if (oConvertUtils.isEmpty(loginTenantId) || str.equals(loginTenantId)) {
|
||||
return;
|
||||
}
|
||||
|
||||
String[] userTenantIdsArray = userTenantIds.split(",");
|
||||
if (!oConvertUtils.isIn(loginTenantId, userTenantIdsArray)) {
|
||||
boolean isAuthorization = false;
|
||||
|
||||
//========================================================================
|
||||
// 查询用户信息(如果租户不匹配从数据库中重新查询一次用户信息)
|
||||
String loginUserKey = CacheConstant.SYS_USERS_CACHE + "::" + username;
|
||||
redisUtil.del(loginUserKey);
|
||||
|
||||
LoginUser loginUserFromDb = commonAPI.getUserByName(username);
|
||||
LoginUserUtils.setSessionUser(loginUserFromDb);
|
||||
if (loginUserFromDb != null && oConvertUtils.isNotEmpty(loginUserFromDb.getRelTenantIds())) {
|
||||
String[] newArray = loginUserFromDb.getRelTenantIds().split(",");
|
||||
if (oConvertUtils.isIn(loginTenantId, newArray)) {
|
||||
isAuthorization = true;
|
||||
}
|
||||
}
|
||||
//========================================================================
|
||||
|
||||
if (!isAuthorization) {
|
||||
log.info("租户异常——登录租户:{}", loginTenantId);
|
||||
log.info("租户异常——用户拥有租户组:{}", userTenantIds);
|
||||
throw new NotLoginException("登录租户授权变更,请重新登陆!", StpUtil.TYPE, NotLoginException.KICK_OUT);
|
||||
}
|
||||
}
|
||||
|
||||
}catch (Exception e) {
|
||||
log.error("租户校验异常:{}", e.getMessage(), e);
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
@ -0,0 +1,174 @@
|
||||
package org.jeecg.config.satoken;
|
||||
|
||||
import cn.dev33.satoken.dao.SaTokenDao;
|
||||
import cn.dev33.satoken.SaManager;
|
||||
import cn.dev33.satoken.stp.StpInterface;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.jeecg.common.api.CommonAPI;
|
||||
import org.springframework.context.annotation.Lazy;
|
||||
import org.springframework.stereotype.Component;
|
||||
|
||||
import jakarta.annotation.Resource;
|
||||
import java.util.ArrayList;
|
||||
import java.util.List;
|
||||
import java.util.Set;
|
||||
|
||||
/**
|
||||
* @description: Sa-Token 权限认证接口实现(带缓存)
|
||||
*
|
||||
* <p>⚠️ 重要说明:</p>
|
||||
* <ul>
|
||||
* <li><strong>Sa-Token 的 StpInterface 默认不提供缓存能力</strong>,需要自己实现缓存逻辑</li>
|
||||
* <li>本实现采用 <strong>[账号id -> 权限/角色列表]</strong> 缓存模型</li>
|
||||
* <li>缓存键格式:
|
||||
* <ul>
|
||||
* <li>用户权限缓存:satoken:user-permission:{username}</li>
|
||||
* <li>用户角色缓存:satoken:user-role:{username}</li>
|
||||
* </ul>
|
||||
* </li>
|
||||
* <li>缓存过期时间:30天</li>
|
||||
* <li>⚠️ 当修改用户的角色或权限时,需要手动清除缓存</li>
|
||||
* </ul>
|
||||
*
|
||||
* <p>清除缓存示例:</p>
|
||||
* <pre>
|
||||
* // 清除单个用户的权限和角色缓存
|
||||
* StpInterfaceImpl.clearUserCache("admin");
|
||||
*
|
||||
* // 清除多个用户的缓存
|
||||
* StpInterfaceImpl.clearUserCache(Arrays.asList("admin", "user1", "user2"));
|
||||
* </pre>
|
||||
*/
|
||||
@Component
|
||||
@Slf4j
|
||||
public class StpInterfaceImpl implements StpInterface {
|
||||
|
||||
@Lazy
|
||||
@Resource
|
||||
private CommonAPI commonApi;
|
||||
|
||||
/**
|
||||
* 缓存过期时间(秒):30天
|
||||
*/
|
||||
private static final long CACHE_TIMEOUT = 60 * 60 * 24 * 30;
|
||||
|
||||
/**
|
||||
* 权限缓存键前缀
|
||||
*/
|
||||
private static final String PERMISSION_CACHE_PREFIX = "satoken:user-permission:";
|
||||
|
||||
/**
|
||||
* 角色缓存键前缀
|
||||
*/
|
||||
private static final String ROLE_CACHE_PREFIX = "satoken:user-role:";
|
||||
|
||||
/**
|
||||
* 返回一个账号所拥有的权限码集合(带缓存)
|
||||
*
|
||||
* @param loginId 账号id(这里是 username)
|
||||
* @param loginType 账号类型
|
||||
* @return 权限码集合
|
||||
*/
|
||||
@Override
|
||||
@SuppressWarnings("unchecked")
|
||||
public List<String> getPermissionList(Object loginId, String loginType) {
|
||||
String username = loginId.toString();
|
||||
String cacheKey = PERMISSION_CACHE_PREFIX + username;
|
||||
|
||||
SaTokenDao dao = SaManager.getSaTokenDao();
|
||||
|
||||
// 1. 先从缓存获取
|
||||
List<String> permissionList = (List<String>) dao.getObject(cacheKey);
|
||||
|
||||
if (permissionList == null) {
|
||||
// 2. 缓存不存在,从数据库查询
|
||||
log.warn("权限缓存未命中,查询数据库 [ username={} ]", username);
|
||||
|
||||
String userId = commonApi.getUserIdByName(username);
|
||||
if (userId == null) {
|
||||
log.warn("用户不存在: {}", username);
|
||||
return new ArrayList<>();
|
||||
}
|
||||
|
||||
Set<String> permissionSet = commonApi.queryUserAuths(userId);
|
||||
permissionList = new ArrayList<>(permissionSet);
|
||||
|
||||
// 3. 将结果缓存起来
|
||||
dao.setObject(cacheKey, permissionList, CACHE_TIMEOUT);
|
||||
log.info("权限已缓存 [ username={}, permissions={} ]", username, permissionList.size());
|
||||
} else {
|
||||
log.debug("权限缓存命中 [ username={}, permissions={} ]", username, permissionList.size());
|
||||
}
|
||||
|
||||
return permissionList;
|
||||
}
|
||||
|
||||
/**
|
||||
* 返回一个账号所拥有的角色标识集合(带缓存)
|
||||
*
|
||||
* @param loginId 账号id(这里是 username)
|
||||
* @param loginType 账号类型
|
||||
* @return 角色标识集合
|
||||
*/
|
||||
@Override
|
||||
@SuppressWarnings("unchecked")
|
||||
public List<String> getRoleList(Object loginId, String loginType) {
|
||||
String username = loginId.toString();
|
||||
String cacheKey = ROLE_CACHE_PREFIX + username;
|
||||
|
||||
SaTokenDao dao = SaManager.getSaTokenDao();
|
||||
|
||||
// 1. 先从缓存获取
|
||||
List<String> roleList = (List<String>) dao.getObject(cacheKey);
|
||||
|
||||
if (roleList == null) {
|
||||
// 2. 缓存不存在,从数据库查询
|
||||
log.warn("角色缓存未命中,查询数据库 [ username={} ]", username);
|
||||
|
||||
String userId = commonApi.getUserIdByName(username);
|
||||
if (userId == null) {
|
||||
log.warn("用户不存在: {}", username);
|
||||
return new ArrayList<>();
|
||||
}
|
||||
|
||||
Set<String> roleSet = commonApi.queryUserRolesById(userId);
|
||||
roleList = new ArrayList<>(roleSet);
|
||||
|
||||
// 3. 将结果缓存起来
|
||||
dao.setObject(cacheKey, roleList, CACHE_TIMEOUT);
|
||||
log.info("角色已缓存 [ username={}, roles={} ]", username, roleList.size());
|
||||
} else {
|
||||
log.debug("角色缓存命中 [ username={}, roles={} ]", username, roleList.size());
|
||||
}
|
||||
|
||||
return roleList;
|
||||
}
|
||||
|
||||
/**
|
||||
* 清除单个用户的权限和角色缓存
|
||||
* <p>使用场景:修改用户的角色分配后</p>
|
||||
*
|
||||
* @param username 用户名
|
||||
*/
|
||||
public static void clearUserCache(String username) {
|
||||
SaTokenDao dao = SaManager.getSaTokenDao();
|
||||
dao.deleteObject(PERMISSION_CACHE_PREFIX + username);
|
||||
dao.deleteObject(ROLE_CACHE_PREFIX + username);
|
||||
log.info("已清除用户缓存 [ username={} ]", username);
|
||||
}
|
||||
|
||||
/**
|
||||
* 批量清除多个用户的权限和角色缓存
|
||||
* <p>使用场景:修改角色权限后,清除拥有该角色的所有用户的缓存</p>
|
||||
*
|
||||
* @param usernameList 用户名列表
|
||||
*/
|
||||
public static void clearUserCache(List<String> usernameList) {
|
||||
SaTokenDao dao = SaManager.getSaTokenDao();
|
||||
for (String username : usernameList) {
|
||||
dao.deleteObject(PERMISSION_CACHE_PREFIX + username);
|
||||
dao.deleteObject(ROLE_CACHE_PREFIX + username);
|
||||
}
|
||||
log.info("已批量清除用户缓存 [ count={} ]", usernameList.size());
|
||||
}
|
||||
}
|
||||
@ -1,14 +1,13 @@
|
||||
package org.jeecg.config.shiro.ignore;
|
||||
package org.jeecg.config.satoken.ignore;
|
||||
|
||||
import lombok.AllArgsConstructor;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.jeecg.config.shiro.IgnoreAuth;
|
||||
import org.jeecg.config.satoken.IgnoreAuth;
|
||||
import org.springframework.beans.factory.InitializingBean;
|
||||
import org.springframework.context.annotation.Lazy;
|
||||
import org.springframework.stereotype.Component;
|
||||
import org.springframework.util.CollectionUtils;
|
||||
import org.springframework.web.bind.annotation.*;
|
||||
import org.springframework.web.method.HandlerMethod;
|
||||
import org.springframework.web.servlet.mvc.method.annotation.RequestMappingHandlerMapping;
|
||||
|
||||
import java.lang.reflect.Method;
|
||||
@ -33,17 +32,17 @@ public class IgnoreAuthPostProcessor implements InitializingBean {
|
||||
public void afterPropertiesSet() throws Exception {
|
||||
|
||||
long startTime = System.currentTimeMillis();
|
||||
|
||||
|
||||
List<String> ignoreAuthUrls = new ArrayList<>();
|
||||
|
||||
|
||||
// 优化:直接从HandlerMethod过滤,避免重复扫描
|
||||
requestMappingHandlerMapping.getHandlerMethods().values().stream()
|
||||
.filter(handlerMethod -> handlerMethod.getMethod().isAnnotationPresent(IgnoreAuth.class))
|
||||
.forEach(handlerMethod -> {
|
||||
Class<?> clazz = handlerMethod.getBeanType();
|
||||
Method method = handlerMethod.getMethod();
|
||||
ignoreAuthUrls.addAll(processIgnoreAuthMethod(clazz, method));
|
||||
});
|
||||
.filter(handlerMethod -> handlerMethod.getMethod().isAnnotationPresent(IgnoreAuth.class))
|
||||
.forEach(handlerMethod -> {
|
||||
Class<?> clazz = handlerMethod.getBeanType();
|
||||
Method method = handlerMethod.getMethod();
|
||||
ignoreAuthUrls.addAll(processIgnoreAuthMethod(clazz, method));
|
||||
});
|
||||
|
||||
log.info("Init Token ignoreAuthUrls Config [ 集合 ] :{}", ignoreAuthUrls);
|
||||
if (!CollectionUtils.isEmpty(ignoreAuthUrls)) {
|
||||
@ -60,7 +59,7 @@ public class IgnoreAuthPostProcessor implements InitializingBean {
|
||||
private List<String> processIgnoreAuthMethod(Class<?> clazz, Method method) {
|
||||
RequestMapping base = clazz.getAnnotation(RequestMapping.class);
|
||||
String[] baseUrl = Objects.nonNull(base) ? base.value() : new String[]{};
|
||||
|
||||
|
||||
String[] uri = null;
|
||||
if (method.isAnnotationPresent(RequestMapping.class)) {
|
||||
uri = method.getAnnotation(RequestMapping.class).value();
|
||||
@ -75,7 +74,7 @@ public class IgnoreAuthPostProcessor implements InitializingBean {
|
||||
} else if (method.isAnnotationPresent(PatchMapping.class)) {
|
||||
uri = method.getAnnotation(PatchMapping.class).value();
|
||||
}
|
||||
|
||||
|
||||
return uri != null ? rebuildUrl(baseUrl, uri) : Collections.emptyList();
|
||||
}
|
||||
|
||||
@ -1,4 +1,4 @@
|
||||
package org.jeecg.config.shiro.ignore;
|
||||
package org.jeecg.config.satoken.ignore;
|
||||
|
||||
import org.springframework.util.AntPathMatcher;
|
||||
import org.springframework.util.PathMatcher;
|
||||
@ -6,8 +6,8 @@ import java.util.ArrayList;
|
||||
import java.util.List;
|
||||
|
||||
/**
|
||||
* 使用内存存储通过@IgnoreAuth注解的url,配合JwtFilter进行免登录校验
|
||||
* PS:无法使用ThreadLocal进行存储,因为ThreadLocal装载时,JwtFilter已经初始化完毕,导致该类获取ThreadLocal为空
|
||||
* 使用内存存储通过@IgnoreAuth注解的url,配合Sa-Token进行免登录校验
|
||||
* PS:无法使用ThreadLocal进行存储,因为ThreadLocal装载时,Filter已经初始化完毕,导致该类获取ThreadLocal为空
|
||||
* @author eightmonth
|
||||
* @date 2024/4/18 15:02
|
||||
*/
|
||||
@ -15,6 +15,7 @@ public class InMemoryIgnoreAuth {
|
||||
private static final List<String> IGNORE_AUTH_LIST = new ArrayList<>();
|
||||
|
||||
private static PathMatcher MATCHER = new AntPathMatcher();
|
||||
|
||||
public InMemoryIgnoreAuth() {}
|
||||
|
||||
public static void set(List<String> list) {
|
||||
@ -31,11 +32,11 @@ public class InMemoryIgnoreAuth {
|
||||
|
||||
public static boolean contains(String url) {
|
||||
for (String ignoreAuth : IGNORE_AUTH_LIST) {
|
||||
if(MATCHER.match(ignoreAuth,url)){
|
||||
if(MATCHER.match(ignoreAuth, url)){
|
||||
return true;
|
||||
}
|
||||
}
|
||||
|
||||
return false;
|
||||
}
|
||||
}
|
||||
|
||||
@ -1,28 +0,0 @@
|
||||
package org.jeecg.config.shiro;
|
||||
|
||||
import org.apache.shiro.authc.AuthenticationToken;
|
||||
|
||||
/**
|
||||
* @Author Scott
|
||||
* @create 2018-07-12 15:19
|
||||
* @desc
|
||||
**/
|
||||
public class JwtToken implements AuthenticationToken {
|
||||
|
||||
private static final long serialVersionUID = 1L;
|
||||
private String token;
|
||||
|
||||
public JwtToken(String token) {
|
||||
this.token = token;
|
||||
}
|
||||
|
||||
@Override
|
||||
public Object getPrincipal() {
|
||||
return token;
|
||||
}
|
||||
|
||||
@Override
|
||||
public Object getCredentials() {
|
||||
return token;
|
||||
}
|
||||
}
|
||||
@ -1,386 +0,0 @@
|
||||
package org.jeecg.config.shiro;
|
||||
|
||||
import jakarta.annotation.Resource;
|
||||
import jakarta.servlet.DispatcherType;
|
||||
import jakarta.servlet.Filter;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.commons.pool2.impl.GenericObjectPoolConfig;
|
||||
import org.apache.shiro.mgt.DefaultSessionStorageEvaluator;
|
||||
import org.apache.shiro.mgt.DefaultSubjectDAO;
|
||||
import org.apache.shiro.mgt.SecurityManager;
|
||||
import org.apache.shiro.spring.LifecycleBeanPostProcessor;
|
||||
import org.apache.shiro.spring.security.interceptor.AuthorizationAttributeSourceAdvisor;
|
||||
import org.apache.shiro.spring.web.ShiroFilterFactoryBean;
|
||||
import org.apache.shiro.spring.web.ShiroUrlPathHelper;
|
||||
import org.apache.shiro.web.mgt.DefaultWebSecurityManager;
|
||||
import org.crazycake.shiro.*;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.util.oConvertUtils;
|
||||
import org.jeecg.config.JeecgBaseConfig;
|
||||
import org.jeecg.config.shiro.filters.CustomShiroFilterFactoryBean;
|
||||
import org.jeecg.config.shiro.filters.JwtFilter;
|
||||
import org.springframework.aop.framework.autoproxy.DefaultAdvisorAutoProxyCreator;
|
||||
import org.springframework.beans.factory.annotation.Autowired;
|
||||
import org.springframework.beans.factory.config.BeanDefinition;
|
||||
import org.springframework.boot.web.servlet.FilterRegistrationBean;
|
||||
import org.springframework.context.annotation.*;
|
||||
import org.springframework.core.annotation.AnnotationUtils;
|
||||
import org.springframework.core.env.Environment;
|
||||
import org.springframework.core.type.filter.AnnotationTypeFilter;
|
||||
import org.springframework.data.redis.connection.lettuce.LettuceConnectionFactory;
|
||||
import org.springframework.boot.autoconfigure.data.redis.RedisProperties;
|
||||
import org.springframework.util.CollectionUtils;
|
||||
import org.springframework.util.StringUtils;
|
||||
import org.springframework.web.bind.annotation.*;
|
||||
import org.springframework.web.filter.DelegatingFilterProxy;
|
||||
import org.springframework.web.servlet.mvc.method.annotation.RequestMappingHandlerMapping;
|
||||
import redis.clients.jedis.HostAndPort;
|
||||
import redis.clients.jedis.JedisCluster;
|
||||
|
||||
import java.lang.reflect.Method;
|
||||
import java.util.*;
|
||||
|
||||
/**
|
||||
* @author: Scott
|
||||
* @date: 2018/2/7
|
||||
* @description: shiro 配置类
|
||||
*/
|
||||
|
||||
@Slf4j
|
||||
@Configuration
|
||||
public class ShiroConfig {
|
||||
|
||||
@Resource
|
||||
private LettuceConnectionFactory lettuceConnectionFactory;
|
||||
@Autowired
|
||||
private Environment env;
|
||||
@Resource
|
||||
private JeecgBaseConfig jeecgBaseConfig;
|
||||
@Autowired(required = false)
|
||||
private RedisProperties redisProperties;
|
||||
|
||||
/**
|
||||
* Filter Chain定义说明
|
||||
*
|
||||
* 1、一个URL可以配置多个Filter,使用逗号分隔
|
||||
* 2、当设置多个过滤器时,全部验证通过,才视为通过
|
||||
* 3、部分过滤器可指定参数,如perms,roles
|
||||
*/
|
||||
@Bean("shiroFilterFactoryBean")
|
||||
public ShiroFilterFactoryBean shiroFilter(SecurityManager securityManager) {
|
||||
CustomShiroFilterFactoryBean shiroFilterFactoryBean = new CustomShiroFilterFactoryBean();
|
||||
shiroFilterFactoryBean.setSecurityManager(securityManager);
|
||||
// 拦截器
|
||||
Map<String, String> filterChainDefinitionMap = new LinkedHashMap<String, String>();
|
||||
|
||||
//支持yml方式,配置拦截排除
|
||||
if(jeecgBaseConfig!=null && jeecgBaseConfig.getShiro()!=null){
|
||||
String shiroExcludeUrls = jeecgBaseConfig.getShiro().getExcludeUrls();
|
||||
if(oConvertUtils.isNotEmpty(shiroExcludeUrls)){
|
||||
String[] permissionUrl = shiroExcludeUrls.split(",");
|
||||
for(String url : permissionUrl){
|
||||
filterChainDefinitionMap.put(url,"anon");
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
// 配置不会被拦截的链接 顺序判断
|
||||
filterChainDefinitionMap.put("/sys/cas/client/validateLogin", "anon"); //cas验证登录
|
||||
filterChainDefinitionMap.put("/sys/randomImage/**", "anon"); //登录验证码接口排除
|
||||
filterChainDefinitionMap.put("/sys/checkCaptcha", "anon"); //登录验证码接口排除
|
||||
filterChainDefinitionMap.put("/sys/smsCheckCaptcha", "anon"); //短信次数发送太多验证码排除
|
||||
filterChainDefinitionMap.put("/sys/login", "anon"); //登录接口排除
|
||||
filterChainDefinitionMap.put("/sys/mLogin", "anon"); //登录接口排除
|
||||
filterChainDefinitionMap.put("/sys/logout", "anon"); //登出接口排除
|
||||
filterChainDefinitionMap.put("/sys/thirdLogin/**", "anon"); //第三方登录
|
||||
filterChainDefinitionMap.put("/sys/getEncryptedString", "anon"); //获取加密串
|
||||
filterChainDefinitionMap.put("/sys/sms", "anon");//短信验证码
|
||||
filterChainDefinitionMap.put("/sys/phoneLogin", "anon");//手机登录
|
||||
filterChainDefinitionMap.put("/sys/user/checkOnlyUser", "anon");//校验用户是否存在
|
||||
filterChainDefinitionMap.put("/sys/user/register", "anon");//用户注册
|
||||
filterChainDefinitionMap.put("/sys/user/phoneVerification", "anon");//用户忘记密码验证手机号
|
||||
filterChainDefinitionMap.put("/sys/user/passwordChange", "anon");//用户更改密码
|
||||
filterChainDefinitionMap.put("/auth/2step-code", "anon");//登录验证码
|
||||
filterChainDefinitionMap.put("/sys/common/static/**", "anon");//图片预览 &下载文件不限制token
|
||||
filterChainDefinitionMap.put("/sys/common/pdf/**", "anon");//pdf预览
|
||||
|
||||
//filterChainDefinitionMap.put("/sys/common/view/**", "anon");//图片预览不限制token
|
||||
//filterChainDefinitionMap.put("/sys/common/download/**", "anon");//文件下载不限制token
|
||||
filterChainDefinitionMap.put("/generic/**", "anon");//pdf预览需要文件
|
||||
|
||||
filterChainDefinitionMap.put("/sys/getLoginQrcode/**", "anon"); //登录二维码
|
||||
filterChainDefinitionMap.put("/sys/getQrcodeToken/**", "anon"); //监听扫码
|
||||
filterChainDefinitionMap.put("/sys/checkAuth", "anon"); //授权接口排除
|
||||
filterChainDefinitionMap.put("/openapi/call/**", "anon"); // 开放平台接口排除
|
||||
|
||||
// 代码逻辑说明: 排除静态资源后缀
|
||||
filterChainDefinitionMap.put("/", "anon");
|
||||
filterChainDefinitionMap.put("/doc.html", "anon");
|
||||
filterChainDefinitionMap.put("/**/*.js", "anon");
|
||||
filterChainDefinitionMap.put("/**/*.css", "anon");
|
||||
filterChainDefinitionMap.put("/**/*.html", "anon");
|
||||
filterChainDefinitionMap.put("/**/*.svg", "anon");
|
||||
filterChainDefinitionMap.put("/**/*.pdf", "anon");
|
||||
filterChainDefinitionMap.put("/**/*.jpg", "anon");
|
||||
filterChainDefinitionMap.put("/**/*.png", "anon");
|
||||
filterChainDefinitionMap.put("/**/*.gif", "anon");
|
||||
filterChainDefinitionMap.put("/**/*.ico", "anon");
|
||||
filterChainDefinitionMap.put("/**/*.ttf", "anon");
|
||||
filterChainDefinitionMap.put("/**/*.woff", "anon");
|
||||
filterChainDefinitionMap.put("/**/*.woff2", "anon");
|
||||
|
||||
filterChainDefinitionMap.put("/**/*.glb", "anon");
|
||||
filterChainDefinitionMap.put("/**/*.wasm", "anon");
|
||||
|
||||
filterChainDefinitionMap.put("/druid/**", "anon");
|
||||
filterChainDefinitionMap.put("/swagger-ui.html", "anon");
|
||||
filterChainDefinitionMap.put("/swagger**/**", "anon");
|
||||
filterChainDefinitionMap.put("/webjars/**", "anon");
|
||||
filterChainDefinitionMap.put("/v3/**", "anon");
|
||||
|
||||
filterChainDefinitionMap.put("/sys/annountCement/show/**", "anon");
|
||||
|
||||
//积木报表排除
|
||||
filterChainDefinitionMap.put("/jmreport/**", "anon");
|
||||
filterChainDefinitionMap.put("/**/*.js.map", "anon");
|
||||
filterChainDefinitionMap.put("/**/*.css.map", "anon");
|
||||
|
||||
//积木BI大屏和仪表盘排除
|
||||
filterChainDefinitionMap.put("/drag/view", "anon");
|
||||
filterChainDefinitionMap.put("/drag/page/queryById", "anon");
|
||||
filterChainDefinitionMap.put("/drag/page/addVisitsNumber", "anon");
|
||||
filterChainDefinitionMap.put("/drag/page/queryTemplateList", "anon");
|
||||
filterChainDefinitionMap.put("/drag/share/view/**", "anon");
|
||||
filterChainDefinitionMap.put("/drag/onlDragDatasetHead/getAllChartData", "anon");
|
||||
filterChainDefinitionMap.put("/drag/onlDragDatasetHead/getTotalData", "anon");
|
||||
filterChainDefinitionMap.put("/drag/onlDragDatasetHead/getMapDataByCode", "anon");
|
||||
filterChainDefinitionMap.put("/drag/onlDragDatasetHead/getTotalDataByCompId", "anon");
|
||||
filterChainDefinitionMap.put("/drag/mock/json/**", "anon");
|
||||
filterChainDefinitionMap.put("/drag/onlDragDatasetHead/getDictByCodes", "anon");
|
||||
filterChainDefinitionMap.put("/drag/onlDragDatasetHead/queryAllById", "anon");
|
||||
filterChainDefinitionMap.put("/jimubi/view", "anon");
|
||||
filterChainDefinitionMap.put("/jimubi/share/view/**", "anon");
|
||||
|
||||
//大屏模板例子
|
||||
filterChainDefinitionMap.put("/test/bigScreen/**", "anon");
|
||||
filterChainDefinitionMap.put("/bigscreen/template1/**", "anon");
|
||||
filterChainDefinitionMap.put("/bigscreen/template2/**", "anon");
|
||||
//filterChainDefinitionMap.put("/test/jeecgDemo/rabbitMqClientTest/**", "anon"); //MQ测试
|
||||
//filterChainDefinitionMap.put("/test/jeecgDemo/html", "anon"); //模板页面
|
||||
//filterChainDefinitionMap.put("/test/jeecgDemo/redis/**", "anon"); //redis测试
|
||||
|
||||
//websocket排除
|
||||
filterChainDefinitionMap.put("/websocket/**", "anon");//系统通知和公告
|
||||
filterChainDefinitionMap.put("/newsWebsocket/**", "anon");//CMS模块
|
||||
filterChainDefinitionMap.put("/vxeSocket/**", "anon");//JVxeTable无痕刷新示例
|
||||
//App vue3版本查询版本接口
|
||||
filterChainDefinitionMap.put("/sys/version/app3version", "anon");
|
||||
//仪表盘(按钮通信)
|
||||
filterChainDefinitionMap.put("/dragChannelSocket/**","anon");
|
||||
|
||||
//性能监控——安全隐患泄露TOEKN(durid连接池也有)
|
||||
//filterChainDefinitionMap.put("/actuator/**", "anon");
|
||||
//测试模块排除
|
||||
filterChainDefinitionMap.put("/test/seata/**", "anon");
|
||||
|
||||
//错误路径排除
|
||||
filterChainDefinitionMap.put("/error", "anon");
|
||||
// 企业微信证书排除
|
||||
filterChainDefinitionMap.put("/WW_verify*", "anon");
|
||||
|
||||
// 添加自己的过滤器并且取名为jwt
|
||||
Map<String, Filter> filterMap = new HashMap<String, Filter>(1);
|
||||
//如果cloudServer为空 则说明是单体 需要加载跨域配置【微服务跨域切换】
|
||||
Object cloudServer = env.getProperty(CommonConstant.CLOUD_SERVER_KEY);
|
||||
filterMap.put("jwt", new JwtFilter(cloudServer==null));
|
||||
shiroFilterFactoryBean.setFilters(filterMap);
|
||||
// <!-- 过滤链定义,从上向下顺序执行,一般将/**放在最为下边
|
||||
filterChainDefinitionMap.put("/**", "jwt");
|
||||
|
||||
// 未授权界面返回JSON
|
||||
shiroFilterFactoryBean.setUnauthorizedUrl("/sys/common/403");
|
||||
shiroFilterFactoryBean.setLoginUrl("/sys/common/403");
|
||||
shiroFilterFactoryBean.setFilterChainDefinitionMap(filterChainDefinitionMap);
|
||||
return shiroFilterFactoryBean;
|
||||
}
|
||||
|
||||
|
||||
/**
|
||||
* spring过滤装饰器 <br/>
|
||||
* 因为shiro的filter不支持异步请求,导致所有的异步请求都会报错. <br/>
|
||||
* 所以需要用spring的FilterRegistrationBean再代理一下shiro的filter.为他扩展异步支持. <br/>
|
||||
* 后续所有异步的接口都需要再这里增加registration.addUrlPatterns("/xxx/xxx");
|
||||
* @return
|
||||
* @author chenrui
|
||||
* @date 2024/12/3 19:49
|
||||
*/
|
||||
@Bean
|
||||
public FilterRegistrationBean shiroFilterRegistration() {
|
||||
FilterRegistrationBean registration = new FilterRegistrationBean();
|
||||
registration.setFilter(new DelegatingFilterProxy("shiroFilterFactoryBean"));
|
||||
registration.setEnabled(true);
|
||||
// 代码逻辑说明: [issues/7491]运行耗时长,效率慢
|
||||
registration.addUrlPatterns("/test/ai/chat/send");
|
||||
registration.addUrlPatterns("/airag/flow/run");
|
||||
registration.addUrlPatterns("/airag/flow/debug");
|
||||
registration.addUrlPatterns("/airag/chat/send");
|
||||
registration.addUrlPatterns("/airag/app/debug");
|
||||
registration.addUrlPatterns("/airag/app/prompt/generate");
|
||||
registration.addUrlPatterns("/airag/chat/receive/**");
|
||||
//支持异步
|
||||
registration.setAsyncSupported(true);
|
||||
registration.setDispatcherTypes(DispatcherType.REQUEST, DispatcherType.ASYNC);
|
||||
return registration;
|
||||
}
|
||||
|
||||
@Bean("securityManager")
|
||||
public DefaultWebSecurityManager securityManager(ShiroRealm myRealm) {
|
||||
DefaultWebSecurityManager securityManager = new DefaultWebSecurityManager();
|
||||
securityManager.setRealm(myRealm);
|
||||
|
||||
/*
|
||||
* 关闭shiro自带的session,详情见文档
|
||||
* http://shiro.apache.org/session-management.html#SessionManagement-
|
||||
* StatelessApplications%28Sessionless%29
|
||||
*/
|
||||
DefaultSubjectDAO subjectDAO = new DefaultSubjectDAO();
|
||||
DefaultSessionStorageEvaluator defaultSessionStorageEvaluator = new DefaultSessionStorageEvaluator();
|
||||
defaultSessionStorageEvaluator.setSessionStorageEnabled(false);
|
||||
subjectDAO.setSessionStorageEvaluator(defaultSessionStorageEvaluator);
|
||||
securityManager.setSubjectDAO(subjectDAO);
|
||||
//自定义缓存实现,使用redis
|
||||
securityManager.setCacheManager(redisCacheManager());
|
||||
return securityManager;
|
||||
}
|
||||
|
||||
/**
|
||||
* 下面的代码是添加注解支持
|
||||
* @return
|
||||
*/
|
||||
@Bean
|
||||
@DependsOn("lifecycleBeanPostProcessor")
|
||||
public DefaultAdvisorAutoProxyCreator defaultAdvisorAutoProxyCreator() {
|
||||
DefaultAdvisorAutoProxyCreator defaultAdvisorAutoProxyCreator = new DefaultAdvisorAutoProxyCreator();
|
||||
defaultAdvisorAutoProxyCreator.setProxyTargetClass(true);
|
||||
/**
|
||||
* 解决重复代理问题 github#994
|
||||
* 添加前缀判断 不匹配 任何Advisor
|
||||
*/
|
||||
defaultAdvisorAutoProxyCreator.setUsePrefix(true);
|
||||
defaultAdvisorAutoProxyCreator.setAdvisorBeanNamePrefix("_no_advisor");
|
||||
return defaultAdvisorAutoProxyCreator;
|
||||
}
|
||||
|
||||
@Bean
|
||||
public static LifecycleBeanPostProcessor lifecycleBeanPostProcessor() {
|
||||
return new LifecycleBeanPostProcessor();
|
||||
}
|
||||
|
||||
@Bean
|
||||
public AuthorizationAttributeSourceAdvisor authorizationAttributeSourceAdvisor(DefaultWebSecurityManager securityManager) {
|
||||
AuthorizationAttributeSourceAdvisor advisor = new AuthorizationAttributeSourceAdvisor();
|
||||
advisor.setSecurityManager(securityManager);
|
||||
return advisor;
|
||||
}
|
||||
|
||||
/**
|
||||
* cacheManager 缓存 redis实现
|
||||
* 使用的是shiro-redis开源插件
|
||||
*
|
||||
* @return
|
||||
*/
|
||||
public RedisCacheManager redisCacheManager() {
|
||||
log.info("===============(1)创建缓存管理器RedisCacheManager");
|
||||
RedisCacheManager redisCacheManager = new RedisCacheManager();
|
||||
redisCacheManager.setRedisManager(redisManager());
|
||||
//redis中针对不同用户缓存(此处的id需要对应user实体中的id字段,用于唯一标识)
|
||||
redisCacheManager.setPrincipalIdFieldName("id");
|
||||
//用户权限信息缓存时间
|
||||
redisCacheManager.setExpire(200000);
|
||||
return redisCacheManager;
|
||||
}
|
||||
|
||||
/**
|
||||
* RedisConfig在项目starter项目中
|
||||
* jeecg-boot-starter-github\jeecg-boot-common\src\main\java\org\jeecg\common\modules\redis\config\RedisConfig.java
|
||||
*
|
||||
* 配置shiro redisManager
|
||||
* 使用的是shiro-redis开源插件
|
||||
*
|
||||
* @return
|
||||
*/
|
||||
@Bean
|
||||
public IRedisManager redisManager() {
|
||||
log.info("===============(2)创建RedisManager,连接Redis..");
|
||||
IRedisManager manager;
|
||||
// sentinel cluster redis(【issues/5569】shiro集成 redis 不支持 sentinel 方式部署的redis集群 #5569)
|
||||
if (Objects.nonNull(redisProperties)
|
||||
&& Objects.nonNull(redisProperties.getSentinel())
|
||||
&& !CollectionUtils.isEmpty(redisProperties.getSentinel().getNodes())) {
|
||||
RedisSentinelManager sentinelManager = new RedisSentinelManager();
|
||||
sentinelManager.setMasterName(redisProperties.getSentinel().getMaster());
|
||||
sentinelManager.setHost(String.join(",", redisProperties.getSentinel().getNodes()));
|
||||
sentinelManager.setPassword(redisProperties.getPassword());
|
||||
sentinelManager.setDatabase(redisProperties.getDatabase());
|
||||
|
||||
return sentinelManager;
|
||||
}
|
||||
|
||||
// redis 单机支持,在集群为空,或者集群无机器时候使用 add by jzyadmin@163.com
|
||||
if (lettuceConnectionFactory.getClusterConfiguration() == null || lettuceConnectionFactory.getClusterConfiguration().getClusterNodes().isEmpty()) {
|
||||
RedisManager redisManager = new RedisManager();
|
||||
redisManager.setHost(lettuceConnectionFactory.getHostName() + ":" + lettuceConnectionFactory.getPort());
|
||||
//(lettuceConnectionFactory.getPort());
|
||||
redisManager.setDatabase(lettuceConnectionFactory.getDatabase());
|
||||
redisManager.setTimeout(0);
|
||||
if (!StringUtils.isEmpty(lettuceConnectionFactory.getPassword())) {
|
||||
redisManager.setPassword(lettuceConnectionFactory.getPassword());
|
||||
}
|
||||
manager = redisManager;
|
||||
}else{
|
||||
// redis集群支持,优先使用集群配置
|
||||
RedisClusterManager redisManager = new RedisClusterManager();
|
||||
Set<HostAndPort> portSet = new HashSet<>();
|
||||
lettuceConnectionFactory.getClusterConfiguration().getClusterNodes().forEach(node -> portSet.add(new HostAndPort(node.getHost() , node.getPort())));
|
||||
//update-begin--Author:scott Date:20210531 for:修改集群模式下未设置redis密码的bug issues/I3QNIC
|
||||
if (oConvertUtils.isNotEmpty(lettuceConnectionFactory.getPassword())) {
|
||||
JedisCluster jedisCluster = new JedisCluster(portSet, 2000, 2000, 5,
|
||||
lettuceConnectionFactory.getPassword(), new GenericObjectPoolConfig());
|
||||
redisManager.setPassword(lettuceConnectionFactory.getPassword());
|
||||
redisManager.setJedisCluster(jedisCluster);
|
||||
} else {
|
||||
JedisCluster jedisCluster = new JedisCluster(portSet);
|
||||
redisManager.setJedisCluster(jedisCluster);
|
||||
}
|
||||
manager = redisManager;
|
||||
}
|
||||
return manager;
|
||||
}
|
||||
|
||||
/**
|
||||
* 解决 ShiroRequestMappingConfig 获取 requestMappingHandlerMapping Bean 冲突
|
||||
* spring-boot-autoconfigure:3.4.5 和 spring-boot-actuator-autoconfigure:3.4.5
|
||||
*/
|
||||
@Primary
|
||||
@Bean
|
||||
public RequestMappingHandlerMapping overridedRequestMappingHandlerMapping() {
|
||||
RequestMappingHandlerMapping mapping = new RequestMappingHandlerMapping();
|
||||
mapping.setUrlPathHelper(new ShiroUrlPathHelper());
|
||||
return mapping;
|
||||
}
|
||||
|
||||
private List<String> rebuildUrl(String[] bases, String[] uris) {
|
||||
List<String> urls = new ArrayList<>();
|
||||
for (String base : bases) {
|
||||
for (String uri : uris) {
|
||||
urls.add(prefix(base)+prefix(uri));
|
||||
}
|
||||
}
|
||||
return urls;
|
||||
}
|
||||
|
||||
private String prefix(String seg) {
|
||||
return seg.startsWith("/") ? seg : "/"+seg;
|
||||
}
|
||||
|
||||
}
|
||||
@ -1,239 +0,0 @@
|
||||
package org.jeecg.config.shiro;
|
||||
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.authc.AuthenticationException;
|
||||
import org.apache.shiro.authc.AuthenticationInfo;
|
||||
import org.apache.shiro.authc.AuthenticationToken;
|
||||
import org.apache.shiro.authc.SimpleAuthenticationInfo;
|
||||
import org.apache.shiro.authz.AuthorizationInfo;
|
||||
import org.apache.shiro.authz.SimpleAuthorizationInfo;
|
||||
import org.apache.shiro.realm.AuthorizingRealm;
|
||||
import org.apache.shiro.subject.PrincipalCollection;
|
||||
import org.jeecg.common.api.CommonAPI;
|
||||
import org.jeecg.common.config.TenantContext;
|
||||
import org.jeecg.common.constant.CacheConstant;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.system.util.JwtUtil;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.jeecg.common.util.RedisUtil;
|
||||
import org.jeecg.common.util.SpringContextUtils;
|
||||
import org.jeecg.common.util.TokenUtils;
|
||||
import org.jeecg.common.util.oConvertUtils;
|
||||
import org.jeecg.config.mybatis.MybatisPlusSaasConfig;
|
||||
import org.springframework.beans.factory.config.BeanDefinition;
|
||||
import org.springframework.context.annotation.Lazy;
|
||||
import org.springframework.context.annotation.Role;
|
||||
import org.springframework.stereotype.Component;
|
||||
|
||||
import jakarta.annotation.Resource;
|
||||
import jakarta.servlet.http.HttpServletRequest;
|
||||
import java.util.Set;
|
||||
|
||||
/**
|
||||
* @Description: 用户登录鉴权和获取用户授权
|
||||
* @Author: Scott
|
||||
* @Date: 2019-4-23 8:13
|
||||
* @Version: 1.1
|
||||
*/
|
||||
@Component
|
||||
@Slf4j
|
||||
@Role(BeanDefinition.ROLE_INFRASTRUCTURE)
|
||||
public class ShiroRealm extends AuthorizingRealm {
|
||||
@Lazy
|
||||
@Resource
|
||||
private CommonAPI commonApi;
|
||||
|
||||
@Lazy
|
||||
@Resource
|
||||
private RedisUtil redisUtil;
|
||||
|
||||
/**
|
||||
* 必须重写此方法,不然Shiro会报错
|
||||
*/
|
||||
@Override
|
||||
public boolean supports(AuthenticationToken token) {
|
||||
return token instanceof JwtToken;
|
||||
}
|
||||
|
||||
/**
|
||||
* 权限信息认证(包括角色以及权限)是用户访问controller的时候才进行验证(redis存储的此处权限信息)
|
||||
* 触发检测用户权限时才会调用此方法,例如checkRole,checkPermission
|
||||
*
|
||||
* @param principals 身份信息
|
||||
* @return AuthorizationInfo 权限信息
|
||||
*/
|
||||
@Override
|
||||
protected AuthorizationInfo doGetAuthorizationInfo(PrincipalCollection principals) {
|
||||
log.debug("===============Shiro权限认证开始============ [ roles、permissions]==========");
|
||||
String username = null;
|
||||
String userId = null;
|
||||
if (principals != null) {
|
||||
LoginUser sysUser = (LoginUser) principals.getPrimaryPrincipal();
|
||||
username = sysUser.getUsername();
|
||||
userId = sysUser.getId();
|
||||
}
|
||||
SimpleAuthorizationInfo info = new SimpleAuthorizationInfo();
|
||||
|
||||
// 设置用户拥有的角色集合,比如“admin,test”
|
||||
Set<String> roleSet = commonApi.queryUserRolesById(userId);
|
||||
//System.out.println(roleSet.toString());
|
||||
info.setRoles(roleSet);
|
||||
|
||||
// 设置用户拥有的权限集合,比如“sys:role:add,sys:user:add”
|
||||
Set<String> permissionSet = commonApi.queryUserAuths(userId);
|
||||
info.addStringPermissions(permissionSet);
|
||||
//System.out.println(permissionSet);
|
||||
log.debug("===============Shiro权限认证成功==============");
|
||||
return info;
|
||||
}
|
||||
|
||||
/**
|
||||
* 用户信息认证是在用户进行登录的时候进行验证(不存redis)
|
||||
* 也就是说验证用户输入的账号和密码是否正确,错误抛出异常
|
||||
*
|
||||
* @param auth 用户登录的账号密码信息
|
||||
* @return 返回封装了用户信息的 AuthenticationInfo 实例
|
||||
* @throws AuthenticationException
|
||||
*/
|
||||
@Override
|
||||
protected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken auth) throws AuthenticationException {
|
||||
log.debug("===============Shiro身份认证开始============doGetAuthenticationInfo==========");
|
||||
String token = (String) auth.getCredentials();
|
||||
if (token == null) {
|
||||
HttpServletRequest req = SpringContextUtils.getHttpServletRequest();
|
||||
log.info("————————身份认证失败——————————IP地址: "+ oConvertUtils.getIpAddrByRequest(req) +",URL:"+req.getRequestURI());
|
||||
throw new AuthenticationException("token为空!");
|
||||
}
|
||||
// 校验token有效性
|
||||
LoginUser loginUser = null;
|
||||
try {
|
||||
loginUser = this.checkUserTokenIsEffect(token);
|
||||
} catch (AuthenticationException e) {
|
||||
log.error("—————校验 check token 失败——————————"+ e.getMessage(), e);
|
||||
// 重新抛出异常,让JwtFilter统一处理,避免返回两次错误响应
|
||||
throw e;
|
||||
}
|
||||
return new SimpleAuthenticationInfo(loginUser, token, getName());
|
||||
}
|
||||
|
||||
/**
|
||||
* 校验token的有效性
|
||||
*
|
||||
* @param token
|
||||
*/
|
||||
public LoginUser checkUserTokenIsEffect(String token) throws AuthenticationException {
|
||||
// 解密获得username,用于和数据库进行对比
|
||||
String username = JwtUtil.getUsername(token);
|
||||
if (username == null) {
|
||||
throw new AuthenticationException("Token非法无效!");
|
||||
}
|
||||
|
||||
// 查询用户信息
|
||||
log.debug("———校验token是否有效————checkUserTokenIsEffect——————— "+ token);
|
||||
LoginUser loginUser = TokenUtils.getLoginUser(username, commonApi, redisUtil);
|
||||
//LoginUser loginUser = commonApi.getUserByName(username);
|
||||
if (loginUser == null) {
|
||||
throw new AuthenticationException("用户不存在!");
|
||||
}
|
||||
// 判断用户状态
|
||||
if (loginUser.getStatus() != 1) {
|
||||
throw new AuthenticationException("账号已被锁定,请联系管理员!");
|
||||
}
|
||||
// 校验token是否超时失效 & 或者账号密码是否错误
|
||||
if (!jwtTokenRefresh(token, username, loginUser.getPassword())) {
|
||||
// 用户登录Token过期提示信息
|
||||
String userLoginTokenErrorMsg = oConvertUtils.getString(redisUtil.get(CommonConstant.PREFIX_USER_TOKEN_ERROR_MSG + token));
|
||||
throw new AuthenticationException(oConvertUtils.isEmpty(userLoginTokenErrorMsg)? CommonConstant.TOKEN_IS_INVALID_MSG: userLoginTokenErrorMsg);
|
||||
}
|
||||
// 代码逻辑说明: 校验用户的tenant_id和前端传过来的是否一致
|
||||
String userTenantIds = loginUser.getRelTenantIds();
|
||||
if(MybatisPlusSaasConfig.OPEN_SYSTEM_TENANT_CONTROL && oConvertUtils.isNotEmpty(userTenantIds)){
|
||||
String contextTenantId = TenantContext.getTenant();
|
||||
log.debug("登录租户:" + contextTenantId);
|
||||
log.debug("用户拥有那些租户:" + userTenantIds);
|
||||
//登录用户无租户,前端header中租户ID值为 0
|
||||
String str ="0";
|
||||
if(oConvertUtils.isNotEmpty(contextTenantId) && !str.equals(contextTenantId)){
|
||||
// 代码逻辑说明: /issues/I4O14W 用户租户信息变更判断漏洞
|
||||
String[] arr = userTenantIds.split(",");
|
||||
if(!oConvertUtils.isIn(contextTenantId, arr)){
|
||||
boolean isAuthorization = false;
|
||||
//========================================================================
|
||||
// 查询用户信息(如果租户不匹配从数据库中重新查询一次用户信息)
|
||||
String loginUserKey = CacheConstant.SYS_USERS_CACHE + "::" + username;
|
||||
redisUtil.del(loginUserKey);
|
||||
LoginUser loginUserFromDb = commonApi.getUserByName(username);
|
||||
if (oConvertUtils.isNotEmpty(loginUserFromDb.getRelTenantIds())) {
|
||||
String[] newArray = loginUserFromDb.getRelTenantIds().split(",");
|
||||
if (oConvertUtils.isIn(contextTenantId, newArray)) {
|
||||
isAuthorization = true;
|
||||
}
|
||||
}
|
||||
//========================================================================
|
||||
|
||||
//*********************************************
|
||||
if(!isAuthorization){
|
||||
log.info("租户异常——登录租户:" + contextTenantId);
|
||||
log.info("租户异常——用户拥有租户组:" + userTenantIds);
|
||||
throw new AuthenticationException("登录租户授权变更,请重新登陆!");
|
||||
}
|
||||
//*********************************************
|
||||
}
|
||||
}
|
||||
}
|
||||
return loginUser;
|
||||
}
|
||||
|
||||
/**
|
||||
* JWTToken刷新生命周期 (实现: 用户在线操作不掉线功能)
|
||||
* 1、登录成功后将用户的JWT生成的Token作为k、v存储到cache缓存里面(这时候k、v值一样),缓存有效期设置为Jwt有效时间的2倍
|
||||
* 2、当该用户再次请求时,通过JWTFilter层层校验之后会进入到doGetAuthenticationInfo进行身份验证
|
||||
* 3、当该用户这次请求jwt生成的token值已经超时,但该token对应cache中的k还是存在,则表示该用户一直在操作只是JWT的token失效了,程序会给token对应的k映射的v值重新生成JWTToken并覆盖v值,该缓存生命周期重新计算
|
||||
* 4、当该用户这次请求jwt在生成的token值已经超时,并在cache中不存在对应的k,则表示该用户账户空闲超时,返回用户信息已失效,请重新登录。
|
||||
* 注意: 前端请求Header中设置Authorization保持不变,校验有效性以缓存中的token为准。
|
||||
* 用户过期时间 = Jwt有效时间 * 2。
|
||||
*
|
||||
* @param userName
|
||||
* @param passWord
|
||||
* @return
|
||||
*/
|
||||
public boolean jwtTokenRefresh(String token, String userName, String passWord) {
|
||||
String cacheToken = String.valueOf(redisUtil.get(CommonConstant.PREFIX_USER_TOKEN + token));
|
||||
if (oConvertUtils.isNotEmpty(cacheToken)) {
|
||||
// 校验token有效性
|
||||
if (!JwtUtil.verify(cacheToken, userName, passWord)) {
|
||||
// 从token中解析客户端类型,保持续期时使用相同的客户端类型
|
||||
String clientType = JwtUtil.getClientType(token);
|
||||
String newAuthorization = JwtUtil.sign(userName, passWord, clientType);
|
||||
// 根据客户端类型设置对应的缓存有效时间
|
||||
long expireTime = CommonConstant.CLIENT_TYPE_APP.equalsIgnoreCase(clientType)
|
||||
? JwtUtil.APP_EXPIRE_TIME * 2 / 1000
|
||||
: JwtUtil.EXPIRE_TIME * 2 / 1000;
|
||||
redisUtil.set(CommonConstant.PREFIX_USER_TOKEN + token, newAuthorization);
|
||||
redisUtil.expire(CommonConstant.PREFIX_USER_TOKEN + token, expireTime);
|
||||
log.debug("——————————用户在线操作,更新token保证不掉线—————————jwtTokenRefresh——————— "+ token);
|
||||
}
|
||||
// else {
|
||||
// // 设置超时时间
|
||||
// redisUtil.set(CommonConstant.PREFIX_USER_TOKEN + token, cacheToken);
|
||||
// redisUtil.expire(CommonConstant.PREFIX_USER_TOKEN + token, JwtUtil.EXPIRE_TIME / 1000);
|
||||
// }
|
||||
return true;
|
||||
}
|
||||
|
||||
//redis中不存在此TOEKN,说明token非法返回false
|
||||
return false;
|
||||
}
|
||||
|
||||
/**
|
||||
* 清除当前用户的权限认证缓存
|
||||
*
|
||||
* @param principals 权限信息
|
||||
*/
|
||||
@Override
|
||||
public void clearCache(PrincipalCollection principals) {
|
||||
super.clearCache(principals);
|
||||
// 代码逻辑说明: 【TV360X-1320】分配权限必须退出重新登录才生效,造成很多用户困扰---
|
||||
super.clearCachedAuthorizationInfo(principals);
|
||||
}
|
||||
}
|
||||
@ -1,77 +0,0 @@
|
||||
package org.jeecg.config.shiro.filters;
|
||||
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.spring.web.ShiroFilterFactoryBean;
|
||||
import org.apache.shiro.web.filter.InvalidRequestFilter;
|
||||
import org.apache.shiro.web.filter.mgt.DefaultFilter;
|
||||
import org.apache.shiro.web.filter.mgt.FilterChainManager;
|
||||
import org.apache.shiro.web.filter.mgt.FilterChainResolver;
|
||||
import org.apache.shiro.web.filter.mgt.PathMatchingFilterChainResolver;
|
||||
import org.apache.shiro.web.mgt.WebSecurityManager;
|
||||
import org.apache.shiro.web.servlet.AbstractShiroFilter;
|
||||
import org.apache.shiro.mgt.SecurityManager;
|
||||
import org.springframework.beans.factory.BeanInitializationException;
|
||||
|
||||
import jakarta.servlet.Filter;
|
||||
import java.util.Map;
|
||||
|
||||
/**
|
||||
* 自定义ShiroFilterFactoryBean解决资源中文路径问题
|
||||
* @author: jeecg-boot
|
||||
*/
|
||||
@Slf4j
|
||||
public class CustomShiroFilterFactoryBean extends ShiroFilterFactoryBean {
|
||||
@Override
|
||||
public Class getObjectType() {
|
||||
return MySpringShiroFilter.class;
|
||||
}
|
||||
|
||||
@Override
|
||||
protected AbstractShiroFilter createInstance() throws Exception {
|
||||
|
||||
SecurityManager securityManager = getSecurityManager();
|
||||
if (securityManager == null) {
|
||||
String msg = "SecurityManager property must be set.";
|
||||
throw new BeanInitializationException(msg);
|
||||
}
|
||||
|
||||
if (!(securityManager instanceof WebSecurityManager)) {
|
||||
String msg = "The security manager does not implement the WebSecurityManager interface.";
|
||||
throw new BeanInitializationException(msg);
|
||||
}
|
||||
|
||||
FilterChainManager manager = createFilterChainManager();
|
||||
//Expose the constructed FilterChainManager by first wrapping it in a
|
||||
// FilterChainResolver implementation. The AbstractShiroFilter implementations
|
||||
// do not know about FilterChainManagers - only resolvers:
|
||||
PathMatchingFilterChainResolver chainResolver = new PathMatchingFilterChainResolver();
|
||||
chainResolver.setFilterChainManager(manager);
|
||||
|
||||
Map<String, Filter> filterMap = manager.getFilters();
|
||||
Filter invalidRequestFilter = filterMap.get(DefaultFilter.invalidRequest.name());
|
||||
if (invalidRequestFilter instanceof InvalidRequestFilter) {
|
||||
//此处是关键,设置false跳过URL携带中文400,servletPath中文校验bug
|
||||
((InvalidRequestFilter) invalidRequestFilter).setBlockNonAscii(false);
|
||||
}
|
||||
//Now create a concrete ShiroFilter instance and apply the acquired SecurityManager and built
|
||||
//FilterChainResolver. It doesn't matter that the instance is an anonymous inner class
|
||||
//here - we're just using it because it is a concrete AbstractShiroFilter instance that accepts
|
||||
//injection of the SecurityManager and FilterChainResolver:
|
||||
return new MySpringShiroFilter((WebSecurityManager) securityManager, chainResolver);
|
||||
}
|
||||
|
||||
private static final class MySpringShiroFilter extends AbstractShiroFilter {
|
||||
protected MySpringShiroFilter(WebSecurityManager webSecurityManager, FilterChainResolver resolver) {
|
||||
if (webSecurityManager == null) {
|
||||
throw new IllegalArgumentException("WebSecurityManager property cannot be null.");
|
||||
} else {
|
||||
this.setSecurityManager(webSecurityManager);
|
||||
if (resolver != null) {
|
||||
this.setFilterChainResolver(resolver);
|
||||
}
|
||||
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
}
|
||||
@ -1,132 +0,0 @@
|
||||
package org.jeecg.config.shiro.filters;
|
||||
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.commons.lang.StringUtils;
|
||||
import org.apache.shiro.web.filter.authc.BasicHttpAuthenticationFilter;
|
||||
import org.jeecg.common.config.TenantContext;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.system.util.JwtUtil;
|
||||
import org.jeecg.common.util.oConvertUtils;
|
||||
import org.jeecg.config.shiro.JwtToken;
|
||||
import org.jeecg.config.shiro.ignore.InMemoryIgnoreAuth;
|
||||
import org.springframework.http.HttpHeaders;
|
||||
import org.springframework.http.HttpStatus;
|
||||
import org.springframework.web.bind.annotation.RequestMethod;
|
||||
|
||||
import jakarta.servlet.ServletRequest;
|
||||
import jakarta.servlet.ServletResponse;
|
||||
import jakarta.servlet.http.HttpServletRequest;
|
||||
import jakarta.servlet.http.HttpServletResponse;
|
||||
|
||||
/**
|
||||
* @Description: 鉴权登录拦截器
|
||||
* @Author: Scott
|
||||
* @Date: 2018/10/7
|
||||
**/
|
||||
@Slf4j
|
||||
public class JwtFilter extends BasicHttpAuthenticationFilter {
|
||||
|
||||
/**
|
||||
* 默认开启跨域设置(使用单体)
|
||||
* 微服务情况下,此属性设置为false
|
||||
*/
|
||||
private boolean allowOrigin = true;
|
||||
|
||||
public JwtFilter(){}
|
||||
public JwtFilter(boolean allowOrigin){
|
||||
this.allowOrigin = allowOrigin;
|
||||
}
|
||||
|
||||
/**
|
||||
* 执行登录认证
|
||||
*
|
||||
* @param request
|
||||
* @param response
|
||||
* @param mappedValue
|
||||
* @return
|
||||
*/
|
||||
@Override
|
||||
protected boolean isAccessAllowed(ServletRequest request, ServletResponse response, Object mappedValue) {
|
||||
try {
|
||||
// 判断当前路径是不是注解了@IngoreAuth路径,如果是,则放开验证
|
||||
if (InMemoryIgnoreAuth.contains(((HttpServletRequest) request).getServletPath())) {
|
||||
return true;
|
||||
}
|
||||
|
||||
executeLogin(request, response);
|
||||
return true;
|
||||
} catch (Exception e) {
|
||||
// 使用异常中的具体错误信息,保留"不允许同一账号多地同时登录"等具体提示
|
||||
String errorMsg = e.getMessage();
|
||||
if (oConvertUtils.isEmpty(errorMsg)) {
|
||||
errorMsg = CommonConstant.TOKEN_IS_INVALID_MSG;
|
||||
}
|
||||
JwtUtil.responseError((HttpServletResponse)response, 401, errorMsg);
|
||||
return false;
|
||||
}
|
||||
}
|
||||
|
||||
/**
|
||||
*
|
||||
*/
|
||||
@Override
|
||||
protected boolean executeLogin(ServletRequest request, ServletResponse response) throws Exception {
|
||||
HttpServletRequest httpServletRequest = (HttpServletRequest) request;
|
||||
String token = httpServletRequest.getHeader(CommonConstant.X_ACCESS_TOKEN);
|
||||
// 代码逻辑说明: JT-355 OA聊天添加token验证,获取token参数
|
||||
if (oConvertUtils.isEmpty(token)) {
|
||||
token = httpServletRequest.getParameter("token");
|
||||
}
|
||||
|
||||
JwtToken jwtToken = new JwtToken(token);
|
||||
// 提交给realm进行登入,如果错误他会抛出异常并被捕获
|
||||
getSubject(request, response).login(jwtToken);
|
||||
// 如果没有抛出异常则代表登入成功,返回true
|
||||
return true;
|
||||
}
|
||||
|
||||
/**
|
||||
* 对跨域提供支持
|
||||
*/
|
||||
@Override
|
||||
protected boolean preHandle(ServletRequest request, ServletResponse response) throws Exception {
|
||||
HttpServletRequest httpServletRequest = (HttpServletRequest) request;
|
||||
HttpServletResponse httpServletResponse = (HttpServletResponse) response;
|
||||
if(allowOrigin){
|
||||
httpServletResponse.setHeader(HttpHeaders.ACCESS_CONTROL_ALLOW_ORIGIN, httpServletRequest.getHeader(HttpHeaders.ORIGIN));
|
||||
// 允许客户端请求方法
|
||||
httpServletResponse.setHeader(HttpHeaders.ACCESS_CONTROL_ALLOW_METHODS, "GET,POST,OPTIONS,PUT,DELETE");
|
||||
// 允许客户端提交的Header
|
||||
String requestHeaders = httpServletRequest.getHeader(HttpHeaders.ACCESS_CONTROL_REQUEST_HEADERS);
|
||||
if (StringUtils.isNotEmpty(requestHeaders)) {
|
||||
httpServletResponse.setHeader(HttpHeaders.ACCESS_CONTROL_ALLOW_HEADERS, requestHeaders);
|
||||
}
|
||||
// 允许客户端携带凭证信息(是否允许发送Cookie)
|
||||
httpServletResponse.setHeader(HttpHeaders.ACCESS_CONTROL_ALLOW_CREDENTIALS, "true");
|
||||
}
|
||||
// 跨域时会首先发送一个option请求,这里我们给option请求直接返回正常状态
|
||||
if (RequestMethod.OPTIONS.name().equalsIgnoreCase(httpServletRequest.getMethod())) {
|
||||
httpServletResponse.setStatus(HttpStatus.OK.value());
|
||||
return false;
|
||||
}
|
||||
// 代码逻辑说明: 多租户用到
|
||||
String tenantId = httpServletRequest.getHeader(CommonConstant.TENANT_ID);
|
||||
TenantContext.setTenant(tenantId);
|
||||
|
||||
return super.preHandle(request, response);
|
||||
}
|
||||
|
||||
/**
|
||||
* JwtFilter中ThreadLocal需要及时清除 #3634
|
||||
*
|
||||
* @param request
|
||||
* @param response
|
||||
* @param exception
|
||||
* @throws Exception
|
||||
*/
|
||||
@Override
|
||||
public void afterCompletion(ServletRequest request, ServletResponse response, Exception exception) throws Exception {
|
||||
//log.info("------清空线程中多租户的ID={}------",TenantContext.getTenant());
|
||||
TenantContext.clear();
|
||||
}
|
||||
}
|
||||
@ -1,67 +0,0 @@
|
||||
package org.jeecg.config.shiro.filters;
|
||||
|
||||
import jakarta.servlet.ServletRequest;
|
||||
import jakarta.servlet.ServletResponse;
|
||||
import jakarta.servlet.http.HttpServletRequest;
|
||||
import jakarta.servlet.http.HttpServletResponse;
|
||||
import org.apache.shiro.subject.Subject;
|
||||
import org.apache.shiro.web.filter.AccessControlFilter;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
|
||||
/**
|
||||
* @Author Scott
|
||||
* @create 2019-02-01 15:56
|
||||
* @desc 鉴权请求URL访问权限拦截器
|
||||
*/
|
||||
@Slf4j
|
||||
public class ResourceCheckFilter extends AccessControlFilter {
|
||||
|
||||
private String errorUrl;
|
||||
|
||||
public String getErrorUrl() {
|
||||
return errorUrl;
|
||||
}
|
||||
|
||||
public void setErrorUrl(String errorUrl) {
|
||||
this.errorUrl = errorUrl;
|
||||
}
|
||||
|
||||
/**
|
||||
* 表示是否允许访问 ,如果允许访问返回true,否则false;
|
||||
*
|
||||
* @param servletRequest
|
||||
* @param servletResponse
|
||||
* @param o 表示写在拦截器中括号里面的字符串 mappedValue 就是 [urls] 配置中拦截器参数部分
|
||||
* @return
|
||||
* @throws Exception
|
||||
*/
|
||||
@Override
|
||||
protected boolean isAccessAllowed(ServletRequest servletRequest, ServletResponse servletResponse, Object o) throws Exception {
|
||||
Subject subject = getSubject(servletRequest, servletResponse);
|
||||
String url = getPathWithinApplication(servletRequest);
|
||||
log.info("当前用户正在访问的 url => " + url);
|
||||
return subject.isPermitted(url);
|
||||
}
|
||||
|
||||
/**
|
||||
* onAccessDenied:表示当访问拒绝时是否已经处理了; 如果返回 true 表示需要继续处理; 如果返回 false
|
||||
* 表示该拦截器实例已经处理了,将直接返回即可。
|
||||
*
|
||||
* @param servletRequest
|
||||
* @param servletResponse
|
||||
* @return
|
||||
* @throws Exception
|
||||
*/
|
||||
@Override
|
||||
protected boolean onAccessDenied(ServletRequest servletRequest, ServletResponse servletResponse) throws Exception {
|
||||
log.info("当 isAccessAllowed 返回 false 的时候,才会执行 method onAccessDenied ");
|
||||
|
||||
HttpServletRequest request = (HttpServletRequest) servletRequest;
|
||||
HttpServletResponse response = (HttpServletResponse) servletResponse;
|
||||
response.sendRedirect(request.getContextPath() + this.errorUrl);
|
||||
|
||||
// 返回 false 表示已经处理,例如页面跳转啥的,表示不在走以下的拦截器了(如果还有配置的话)
|
||||
return false;
|
||||
}
|
||||
|
||||
}
|
||||
@ -19,10 +19,6 @@ public class Firewall {
|
||||
* 低代码模式(dev:开发模式,prod:发布模式——关闭所有在线开发配置能力)
|
||||
*/
|
||||
private String lowCodeMode;
|
||||
/**
|
||||
* 是否允许同一账号多地同时登录 (为 true 时允许一起登录, 为 false 时新登录挤掉旧登录)
|
||||
*/
|
||||
private Boolean isConcurrent = true;
|
||||
/**
|
||||
* 是否开启默认密码登录提醒(true 登录后提示必须修改默认密码)
|
||||
*/
|
||||
@ -78,12 +74,4 @@ public class Firewall {
|
||||
public void setDisableSelectAll(Boolean disableSelectAll) {
|
||||
this.disableSelectAll = disableSelectAll;
|
||||
}
|
||||
|
||||
public Boolean getIsConcurrent() {
|
||||
return isConcurrent;
|
||||
}
|
||||
|
||||
public void setIsConcurrent(Boolean isConcurrent) {
|
||||
this.isConcurrent = isConcurrent;
|
||||
}
|
||||
}
|
||||
|
||||
@ -2,7 +2,7 @@ package org.jeecg.modules.base.service.impl;
|
||||
|
||||
import com.baomidou.mybatisplus.core.toolkit.IdWorker;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.api.dto.LogDTO;
|
||||
import org.jeecg.common.constant.enums.ClientTerminalTypeEnum;
|
||||
import org.jeecg.common.util.BrowserUtils;
|
||||
@ -74,7 +74,7 @@ public class BaseCommonServiceImpl implements BaseCommonService {
|
||||
//获取登录用户信息
|
||||
if(user==null){
|
||||
try {
|
||||
user = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
user = LoginUserUtils.getSessionUser();
|
||||
} catch (Exception e) {
|
||||
//e.printStackTrace();
|
||||
}
|
||||
|
||||
@ -1,17 +1,17 @@
|
||||
package org.jeecg.modules.airag.app.controller;
|
||||
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
import com.baomidou.mybatisplus.core.conditions.query.QueryWrapper;
|
||||
import com.baomidou.mybatisplus.core.metadata.IPage;
|
||||
import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.system.base.controller.JeecgController;
|
||||
import org.jeecg.common.system.query.QueryGenerator;
|
||||
import org.jeecg.common.util.AssertUtils;
|
||||
import org.jeecg.common.util.TokenUtils;
|
||||
import org.jeecg.config.mybatis.MybatisPlusSaasConfig;
|
||||
import org.jeecg.config.shiro.IgnoreAuth;
|
||||
import org.jeecg.config.satoken.IgnoreAuth;
|
||||
import org.jeecg.modules.airag.app.consts.AiAppConsts;
|
||||
import org.jeecg.modules.airag.app.entity.AiragApp;
|
||||
import org.jeecg.modules.airag.app.service.IAiragAppService;
|
||||
@ -67,7 +67,7 @@ public class AiragAppController extends JeecgController<AiragApp, IAiragAppServi
|
||||
* @return
|
||||
*/
|
||||
@RequestMapping(value = "/edit", method = {RequestMethod.PUT, RequestMethod.POST})
|
||||
@RequiresPermissions("airag:app:edit")
|
||||
@SaCheckPermission("airag:app:edit")
|
||||
public Result<String> edit(@RequestBody AiragApp airagApp) {
|
||||
AssertUtils.assertNotEmpty("参数异常", airagApp);
|
||||
AssertUtils.assertNotEmpty("请输入应用名称", airagApp.getName());
|
||||
@ -106,7 +106,7 @@ public class AiragAppController extends JeecgController<AiragApp, IAiragAppServi
|
||||
* @return
|
||||
*/
|
||||
@DeleteMapping(value = "/delete")
|
||||
@RequiresPermissions("airag:app:delete")
|
||||
@SaCheckPermission("airag:app:delete")
|
||||
public Result<String> delete(HttpServletRequest request,@RequestParam(name = "id", required = true) String id) {
|
||||
//update-begin---author:chenrui ---date:20250606 for:[issues/8337]关于ai工作列表的数据权限问题 #8337------------
|
||||
//如果是saas隔离的情况下,判断当前租户id是否是当前租户下的
|
||||
|
||||
@ -6,7 +6,7 @@ import lombok.extern.slf4j.Slf4j;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.util.CommonUtils;
|
||||
import org.jeecg.config.shiro.IgnoreAuth;
|
||||
import org.jeecg.config.satoken.IgnoreAuth;
|
||||
import org.jeecg.modules.airag.app.service.IAiragChatService;
|
||||
import org.jeecg.modules.airag.app.vo.ChatConversation;
|
||||
import org.jeecg.modules.airag.app.vo.ChatSendParams;
|
||||
|
||||
@ -1306,7 +1306,7 @@ public class AiragChatServiceImpl implements IAiragChatService {
|
||||
} else {
|
||||
token = TokenUtils.getTokenByRequest();
|
||||
}
|
||||
if (TokenUtils.verifyToken(token, sysBaseApi, redisUtil)) {
|
||||
if (TokenUtils.verifyToken(token, sysBaseApi)) {
|
||||
return JwtUtil.getUsername(token);
|
||||
}
|
||||
} catch (Exception e) {
|
||||
|
||||
@ -1,10 +1,10 @@
|
||||
package org.jeecg.modules.airag.llm.controller;
|
||||
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
import com.baomidou.mybatisplus.core.conditions.query.QueryWrapper;
|
||||
import com.baomidou.mybatisplus.core.metadata.IPage;
|
||||
import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.system.query.QueryGenerator;
|
||||
import org.jeecg.common.util.AssertUtils;
|
||||
@ -77,7 +77,7 @@ public class AiragKnowledgeController {
|
||||
* @date 2025/2/18 17:09
|
||||
*/
|
||||
@PostMapping(value = "/add")
|
||||
@RequiresPermissions("airag:knowledge:add")
|
||||
@SaCheckPermission("airag:knowledge:add")
|
||||
public Result<String> add(@RequestBody AiragKnowledge airagKnowledge) {
|
||||
airagKnowledge.setStatus(LLMConsts.STATUS_ENABLE);
|
||||
airagKnowledgeService.save(airagKnowledge);
|
||||
@ -94,7 +94,7 @@ public class AiragKnowledgeController {
|
||||
*/
|
||||
@Transactional(rollbackFor = Exception.class)
|
||||
@RequestMapping(value = "/edit", method = {RequestMethod.PUT, RequestMethod.POST})
|
||||
@RequiresPermissions("airag:knowledge:edit")
|
||||
@SaCheckPermission("airag:knowledge:edit")
|
||||
public Result<String> edit(@RequestBody AiragKnowledge airagKnowledge) {
|
||||
AiragKnowledge airagKnowledgeEntity = airagKnowledgeService.getById(airagKnowledge.getId());
|
||||
if (airagKnowledgeEntity == null) {
|
||||
@ -118,7 +118,7 @@ public class AiragKnowledgeController {
|
||||
* @date 2025/3/12 17:05
|
||||
*/
|
||||
@PutMapping(value = "/rebuild")
|
||||
@RequiresPermissions("airag:knowledge:rebuild")
|
||||
@SaCheckPermission("airag:knowledge:rebuild")
|
||||
public Result<?> rebuild(@RequestParam("knowIds") String knowIds) {
|
||||
String[] knowIdArr = knowIds.split(",");
|
||||
for (String knowId : knowIdArr) {
|
||||
@ -137,7 +137,7 @@ public class AiragKnowledgeController {
|
||||
*/
|
||||
@Transactional(rollbackFor = Exception.class)
|
||||
@DeleteMapping(value = "/delete")
|
||||
@RequiresPermissions("airag:knowledge:delete")
|
||||
@SaCheckPermission("airag:knowledge:delete")
|
||||
public Result<String> delete(HttpServletRequest request, @RequestParam(name = "id", required = true) String id) {
|
||||
//update-begin---author:chenrui ---date:20250606 for:[issues/8337]关于ai工作列表的数据权限问题 #8337------------
|
||||
//如果是saas隔离的情况下,判断当前租户id是否是当前租户下的
|
||||
@ -204,7 +204,7 @@ public class AiragKnowledgeController {
|
||||
* @date 2025/2/18 15:47
|
||||
*/
|
||||
@PostMapping(value = "/doc/edit")
|
||||
@RequiresPermissions("airag:knowledge:doc:edit")
|
||||
@SaCheckPermission("airag:knowledge:doc:edit")
|
||||
public Result<?> addDocument(@RequestBody AiragKnowledgeDoc airagKnowledgeDoc) {
|
||||
return airagKnowledgeDocService.editDocument(airagKnowledgeDoc);
|
||||
}
|
||||
@ -217,7 +217,7 @@ public class AiragKnowledgeController {
|
||||
* @date 2025/3/20 11:29
|
||||
*/
|
||||
@PostMapping(value = "/doc/import/zip")
|
||||
@RequiresPermissions("airag:knowledge:doc:zip")
|
||||
@SaCheckPermission("airag:knowledge:doc:zip")
|
||||
public Result<?> importDocumentFromZip(@RequestParam(name = "knowId", required = true) String knowId,
|
||||
@RequestParam(name = "file", required = true) MultipartFile file) {
|
||||
return airagKnowledgeDocService.importDocumentFromZip(knowId,file);
|
||||
@ -244,7 +244,7 @@ public class AiragKnowledgeController {
|
||||
* @date 2025/2/18 15:47
|
||||
*/
|
||||
@PutMapping(value = "/doc/rebuild")
|
||||
@RequiresPermissions("airag:knowledge:doc:rebuild")
|
||||
@SaCheckPermission("airag:knowledge:doc:rebuild")
|
||||
public Result<?> rebuildDocument(@RequestParam("docIds") String docIds) {
|
||||
return airagKnowledgeDocService.rebuildDocument(docIds);
|
||||
}
|
||||
@ -259,7 +259,7 @@ public class AiragKnowledgeController {
|
||||
*/
|
||||
@Transactional(rollbackFor = Exception.class)
|
||||
@DeleteMapping(value = "/doc/deleteBatch")
|
||||
@RequiresPermissions("airag:knowledge:doc:deleteBatch")
|
||||
@SaCheckPermission("airag:knowledge:doc:deleteBatch")
|
||||
public Result<String> deleteDocumentBatch(HttpServletRequest request, @RequestParam(name = "ids", required = true) String ids) {
|
||||
List<String> idsList = Arrays.asList(ids.split(","));
|
||||
//update-begin---author:chenrui ---date:20250606 for:[issues/8337]关于ai工作列表的数据权限问题 #8337------------
|
||||
@ -287,7 +287,7 @@ public class AiragKnowledgeController {
|
||||
*/
|
||||
@Transactional(rollbackFor = Exception.class)
|
||||
@DeleteMapping(value = "/doc/deleteAll")
|
||||
@RequiresPermissions("airag:knowledge:doc:deleteAll")
|
||||
@SaCheckPermission("airag:knowledge:doc:deleteAll")
|
||||
public Result<?> deleteDocumentAll(HttpServletRequest request, @RequestParam(name = "knowId") String knowId) {
|
||||
//update-begin---author:chenrui ---date:20250606 for:[issues/8337]关于ai工作列表的数据权限问题 #8337------------
|
||||
//如果是saas隔离的情况下,判断当前租户id是否是当前租户下的
|
||||
|
||||
@ -169,7 +169,7 @@ public class AiragMcpController extends JeecgController<AiragMcp, IAiragMcpServi
|
||||
* @param request
|
||||
* @param airagMcp
|
||||
*/
|
||||
// @RequiresPermissions("llm:airag_mcp:exportXls")
|
||||
// @SaCheckPermission("llm:airag_mcp:exportXls")
|
||||
@RequestMapping(value = "/exportXls")
|
||||
public ModelAndView exportXls(HttpServletRequest request, AiragMcp airagMcp) {
|
||||
return super.exportXls(request, airagMcp, AiragMcp.class, "MCP");
|
||||
@ -182,7 +182,7 @@ public class AiragMcpController extends JeecgController<AiragMcp, IAiragMcpServi
|
||||
* @param response
|
||||
* @return
|
||||
*/
|
||||
// @RequiresPermissions("llm:airag_mcp:importExcel")
|
||||
// @SaCheckPermission("llm:airag_mcp:importExcel")
|
||||
@RequestMapping(value = "/importExcel", method = RequestMethod.POST)
|
||||
public Result<?> importExcel(HttpServletRequest request, HttpServletResponse response) {
|
||||
return super.importExcel(request, response, AiragMcp.class);
|
||||
|
||||
@ -1,5 +1,6 @@
|
||||
package org.jeecg.modules.airag.llm.controller;
|
||||
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
import com.baomidou.mybatisplus.core.conditions.query.QueryWrapper;
|
||||
import com.baomidou.mybatisplus.core.metadata.IPage;
|
||||
import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
@ -7,7 +8,6 @@ import dev.langchain4j.data.message.UserMessage;
|
||||
import dev.langchain4j.model.embedding.EmbeddingModel;
|
||||
import io.swagger.v3.oas.annotations.tags.Tag;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import org.jeecg.ai.factory.AiModelFactory;
|
||||
import org.jeecg.ai.factory.AiModelOptions;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
@ -72,7 +72,7 @@ public class AiragModelController extends JeecgController<AiragModel, IAiragMode
|
||||
* @return
|
||||
*/
|
||||
@PostMapping(value = "/add")
|
||||
@RequiresPermissions("airag:model:add")
|
||||
@SaCheckPermission("airag:model:add")
|
||||
public Result<String> add(@RequestBody AiragModel airagModel) {
|
||||
// 验证 模型名称/模型类型/基础模型
|
||||
AssertUtils.assertNotEmpty("模型名称不能为空", airagModel.getName());
|
||||
@ -95,7 +95,7 @@ public class AiragModelController extends JeecgController<AiragModel, IAiragMode
|
||||
* @return
|
||||
*/
|
||||
@RequestMapping(value = "/edit", method = {RequestMethod.PUT, RequestMethod.POST})
|
||||
@RequiresPermissions("airag:model:edit")
|
||||
@SaCheckPermission("airag:model:edit")
|
||||
public Result<String> edit(@RequestBody AiragModel airagModel) {
|
||||
airagModelService.updateById(airagModel);
|
||||
return Result.OK("编辑成功!");
|
||||
@ -108,7 +108,7 @@ public class AiragModelController extends JeecgController<AiragModel, IAiragMode
|
||||
* @return
|
||||
*/
|
||||
@DeleteMapping(value = "/delete")
|
||||
@RequiresPermissions("airag:model:delete")
|
||||
@SaCheckPermission("airag:model:delete")
|
||||
public Result<String> delete(HttpServletRequest request, @RequestParam(name = "id", required = true) String id) {
|
||||
//update-begin---author:chenrui ---date:20250606 for:[issues/8337]关于ai工作列表的数据权限问题 #8337------------
|
||||
//如果是saas隔离的情况下,判断当前租户id是否是当前租户下的
|
||||
|
||||
@ -10,8 +10,6 @@ import io.swagger.v3.oas.annotations.Operation;
|
||||
import io.swagger.v3.oas.annotations.Parameter;
|
||||
import io.swagger.v3.oas.annotations.tags.Tag;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.apache.shiro.mgt.DefaultSecurityManager;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.aspect.annotation.AutoLog;
|
||||
import org.jeecg.common.aspect.annotation.PermissionData;
|
||||
@ -21,7 +19,7 @@ import org.jeecg.common.system.query.QueryGenerator;
|
||||
import org.jeecg.common.util.DateUtils;
|
||||
import org.jeecg.common.util.RedisUtil;
|
||||
import org.jeecg.common.util.UUIDGenerator;
|
||||
import org.jeecg.config.shiro.IgnoreAuth;
|
||||
import org.jeecg.config.satoken.IgnoreAuth;
|
||||
import org.jeecg.modules.demo.test.entity.JeecgDemo;
|
||||
import org.jeecg.modules.demo.test.service.IJeecgDemoService;
|
||||
import org.springframework.beans.factory.annotation.Autowired;
|
||||
@ -477,11 +475,6 @@ public class JeecgDemoController extends JeecgController<JeecgDemo, IJeecgDemoSe
|
||||
*/
|
||||
@GetMapping(value ="/test")
|
||||
public Mono<String> test() {
|
||||
//解决shiro报错No SecurityManager accessible to the calling code, either bound to the org.apache.shiro
|
||||
// https://blog.csdn.net/Japhet_jiu/article/details/131177210
|
||||
DefaultSecurityManager securityManager = new DefaultSecurityManager();
|
||||
SecurityUtils.setSecurityManager(securityManager);
|
||||
|
||||
return Mono.just("测试");
|
||||
}
|
||||
|
||||
|
||||
@ -8,17 +8,14 @@ import java.util.Map;
|
||||
import jakarta.servlet.http.HttpServletRequest;
|
||||
import jakarta.servlet.http.HttpServletResponse;
|
||||
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.system.base.controller.JeecgController;
|
||||
import org.jeecg.common.system.query.QueryGenerator;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.jeecg.common.util.oConvertUtils;
|
||||
import org.jeecg.modules.demo.test.entity.JeecgDemo;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.modules.demo.test.entity.JeecgOrderCustomer;
|
||||
import org.jeecg.modules.demo.test.entity.JeecgOrderMain;
|
||||
import org.jeecg.modules.demo.test.entity.JeecgOrderTicket;
|
||||
import org.jeecg.modules.demo.test.service.IJeecgDemoService;
|
||||
import org.jeecg.modules.demo.test.service.IJeecgOrderCustomerService;
|
||||
import org.jeecg.modules.demo.test.service.IJeecgOrderMainService;
|
||||
import org.jeecg.modules.demo.test.service.IJeecgOrderTicketService;
|
||||
@ -33,7 +30,6 @@ import org.springframework.beans.factory.annotation.Autowired;
|
||||
import org.springframework.web.bind.annotation.DeleteMapping;
|
||||
import org.springframework.web.bind.annotation.GetMapping;
|
||||
import org.springframework.web.bind.annotation.PostMapping;
|
||||
import org.springframework.web.bind.annotation.PutMapping;
|
||||
import org.springframework.web.bind.annotation.RequestBody;
|
||||
import org.springframework.web.bind.annotation.RequestMapping;
|
||||
import org.springframework.web.bind.annotation.RequestMethod;
|
||||
@ -184,7 +180,7 @@ public class JeecgOrderMainController extends JeecgController<JeecgOrderMain, IJ
|
||||
//Step.2 AutoPoi 导出Excel
|
||||
ModelAndView mv = new ModelAndView(new JeecgEntityExcelView());
|
||||
//获取当前用户
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
|
||||
List<JeecgOrderMainPage> pageList = new ArrayList<JeecgOrderMainPage>();
|
||||
|
||||
|
||||
@ -3,10 +3,10 @@ package org.jeecg.modules.demo.test.service.impl;
|
||||
import com.baomidou.mybatisplus.core.metadata.IPage;
|
||||
import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
import com.baomidou.mybatisplus.extension.service.impl.ServiceImpl;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.constant.CacheConstant;
|
||||
import org.jeecg.common.system.query.QueryGenerator;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.modules.demo.test.entity.JeecgDemo;
|
||||
import org.jeecg.modules.demo.test.mapper.JeecgDemoMapper;
|
||||
import org.jeecg.modules.demo.test.service.IJeecgDemoService;
|
||||
@ -97,7 +97,7 @@ public class JeecgDemoServiceImpl extends ServiceImpl<JeecgDemoMapper, JeecgDemo
|
||||
|
||||
@Override
|
||||
public String getExportFields() {
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
//权限配置列导出示例
|
||||
//1.配置前缀与菜单中配置的列前缀一致
|
||||
List<String> noAuthList = new ArrayList<>();
|
||||
|
||||
@ -1,30 +0,0 @@
|
||||
package org.jeecg.config.init;
|
||||
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.util.RedisUtil;
|
||||
import org.springframework.beans.factory.annotation.Autowired;
|
||||
import org.springframework.boot.ApplicationArguments;
|
||||
import org.springframework.boot.ApplicationRunner;
|
||||
import org.springframework.stereotype.Component;
|
||||
|
||||
/**
|
||||
* Shiro缓存清理
|
||||
* 在应用启动时清除所有的Shiro授权缓存
|
||||
* 主要用于解决重启项目,用户未重新登录,按钮权限不生效的问题
|
||||
*/
|
||||
@Slf4j
|
||||
@Component
|
||||
public class ShiroCacheClearRunner implements ApplicationRunner {
|
||||
|
||||
@Autowired
|
||||
private RedisUtil redisUtil;
|
||||
|
||||
@Override
|
||||
public void run(ApplicationArguments args) {
|
||||
// 清空所有授权redis缓存
|
||||
log.info("——— Service restart, clearing all user shiro authorization cache ——— ");
|
||||
redisUtil.removeAll(CommonConstant.PREFIX_USER_SHIRO_CACHE);
|
||||
|
||||
}
|
||||
}
|
||||
@ -56,7 +56,7 @@ public class JimuReportTokenService implements JmReportTokenServiceI {
|
||||
|
||||
@Override
|
||||
public Boolean verifyToken(String token) {
|
||||
return TokenUtils.verifyToken(token, sysBaseApi, redisUtil);
|
||||
return TokenUtils.verifyToken(token, sysBaseApi);
|
||||
}
|
||||
|
||||
@Override
|
||||
|
||||
@ -1,6 +1,6 @@
|
||||
package org.jeecg.modules.aop;
|
||||
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.aspectj.lang.ProceedingJoinPoint;
|
||||
import org.aspectj.lang.annotation.AfterThrowing;
|
||||
import org.aspectj.lang.annotation.Around;
|
||||
@ -79,7 +79,7 @@ public class TenantPackUserLogAspect {
|
||||
dto.setOperateType(opType);
|
||||
dto.setTenantId(tenantId);
|
||||
//获取登录用户信息
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
if(sysUser!=null){
|
||||
dto.setUserid(sysUser.getUsername());
|
||||
dto.setUsername(sysUser.getRealname());
|
||||
|
||||
@ -7,8 +7,8 @@ import jakarta.servlet.http.HttpServletResponse;
|
||||
|
||||
import org.apache.commons.lang.StringUtils;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.system.util.JwtUtil;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.util.RedisUtil;
|
||||
import org.jeecg.modules.cas.util.CasServiceUtil;
|
||||
import org.jeecg.modules.cas.util.XmlUtils;
|
||||
@ -16,6 +16,7 @@ import org.jeecg.modules.system.entity.SysDepart;
|
||||
import org.jeecg.modules.system.entity.SysUser;
|
||||
import org.jeecg.modules.system.service.ISysDepartService;
|
||||
import org.jeecg.modules.system.service.ISysUserService;
|
||||
import org.springframework.beans.BeanUtils;
|
||||
import org.springframework.beans.factory.annotation.Autowired;
|
||||
import org.springframework.beans.factory.annotation.Value;
|
||||
import org.springframework.http.HttpEntity;
|
||||
@ -78,10 +79,10 @@ public class CasClientController {
|
||||
if(!result.isSuccess()) {
|
||||
return result;
|
||||
}
|
||||
String token = JwtUtil.sign(sysUser.getUsername(), sysUser.getPassword(), CommonConstant.CLIENT_TYPE_PC);
|
||||
// 设置超时时间
|
||||
redisUtil.set(CommonConstant.PREFIX_USER_TOKEN + token, token);
|
||||
redisUtil.expire(CommonConstant.PREFIX_USER_TOKEN + token, JwtUtil.EXPIRE_TIME*2 / 1000);
|
||||
// 使用Sa-Token生成token(使用username作为loginId)
|
||||
LoginUser loginUser = new LoginUser();
|
||||
BeanUtils.copyProperties(sysUser, loginUser);
|
||||
String token = LoginUserUtils.doLogin(loginUser);
|
||||
|
||||
//获取用户部门信息
|
||||
JSONObject obj = new JSONObject();
|
||||
|
||||
@ -6,10 +6,12 @@ import org.apache.commons.lang3.ObjectUtils;
|
||||
import org.jeecg.common.api.dto.message.MessageDTO;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.constant.enums.MessageTypeEnum;
|
||||
import org.jeecg.common.system.util.JwtUtil;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.util.RedisUtil;
|
||||
import org.jeecg.common.util.SpringContextUtils;
|
||||
import org.jeecg.common.util.oConvertUtils;
|
||||
import org.springframework.beans.BeanUtils;
|
||||
import org.jeecg.config.StaticConfig;
|
||||
import org.jeecg.modules.message.entity.SysMessage;
|
||||
import org.jeecg.modules.message.handle.ISendMsgHandle;
|
||||
@ -236,12 +238,10 @@ public class EmailSendMsgHandle implements ISendMsgHandle {
|
||||
* @return
|
||||
*/
|
||||
private String getToken(SysUser user) {
|
||||
// 生成token
|
||||
String token = JwtUtil.sign(user.getUsername(), user.getPassword(), CommonConstant.CLIENT_TYPE_PC);
|
||||
redisUtil.set(CommonConstant.PREFIX_USER_TOKEN + token, token);
|
||||
// 设置超时时间 1个小时
|
||||
redisUtil.expire(CommonConstant.PREFIX_USER_TOKEN + token, JwtUtil.EXPIRE_TIME * 1 / 1000);
|
||||
return token;
|
||||
// 使用封装方法:一步完成登录和设置用户信息
|
||||
LoginUser loginUser = new LoginUser();
|
||||
BeanUtils.copyProperties(user, loginUser);
|
||||
return LoginUserUtils.doLogin(loginUser);
|
||||
}
|
||||
|
||||
/**
|
||||
|
||||
@ -1,86 +0,0 @@
|
||||
//package org.jeecg.modules.ngalain.controller;
|
||||
//
|
||||
//import java.util.ArrayList;
|
||||
//import java.util.List;
|
||||
//import java.util.Map;
|
||||
//
|
||||
//import jakarta.servlet.http.HttpServletRequest;
|
||||
//
|
||||
//import org.apache.shiro.SecurityUtils;
|
||||
//import org.jeecg.common.api.vo.Result;
|
||||
//import org.jeecg.common.system.vo.DictModel;
|
||||
//import org.jeecg.common.system.vo.LoginUser;
|
||||
//import org.jeecg.modules.ngalain.service.NgAlainService;
|
||||
//import org.jeecg.modules.system.service.ISysDictService;
|
||||
//import org.springframework.beans.factory.annotation.Autowired;
|
||||
//import org.springframework.web.bind.annotation.PathVariable;
|
||||
//import org.springframework.web.bind.annotation.RequestMapping;
|
||||
//import org.springframework.web.bind.annotation.RequestMethod;
|
||||
//import org.springframework.web.bind.annotation.ResponseBody;
|
||||
//import org.springframework.web.bind.annotation.RestController;
|
||||
//
|
||||
//import com.alibaba.fastjson.JSONObject;
|
||||
//
|
||||
//import lombok.extern.slf4j.Slf4j;
|
||||
//
|
||||
//@Slf4j
|
||||
//@RestController
|
||||
//@RequestMapping("/sys/ng-alain")
|
||||
//public class NgAlainController {
|
||||
// @Autowired
|
||||
// private NgAlainService ngAlainService;
|
||||
// @Autowired
|
||||
// private ISysDictService sysDictService;
|
||||
//
|
||||
// @RequestMapping(value = "/getAppData")
|
||||
// @ResponseBody
|
||||
// public JSONObject getAppData(HttpServletRequest request) throws Exception {
|
||||
// String token=request.getHeader("X-Access-Token");
|
||||
// JSONObject j = new JSONObject();
|
||||
// LoginUser user = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
// JSONObject userObjcet = new JSONObject();
|
||||
// userObjcet.put("name", user.getUsername());
|
||||
// userObjcet.put("avatar", user.getAvatar());
|
||||
// userObjcet.put("email", user.getEmail());
|
||||
// userObjcet.put("token", token);
|
||||
// j.put("user", userObjcet);
|
||||
// j.put("menu",ngAlainService.getMenu(user.getUsername()));
|
||||
// JSONObject app = new JSONObject();
|
||||
// app.put("name", "jeecg-boot-angular");
|
||||
// app.put("description", "jeecg+ng-alain整合版本");
|
||||
// j.put("app", app);
|
||||
// return j;
|
||||
// }
|
||||
//
|
||||
// @RequestMapping(value = "/getDictItems/{dictCode}", method = RequestMethod.GET)
|
||||
// public Object getDictItems(@PathVariable String dictCode) {
|
||||
// log.info(" dictCode : "+ dictCode);
|
||||
// Result<List<DictModel>> result = new Result<List<DictModel>>();
|
||||
// List<DictModel> ls = null;
|
||||
// try {
|
||||
// ls = sysDictService.queryDictItemsByCode(dictCode);
|
||||
// result.setSuccess(true);
|
||||
// result.setResult(ls);
|
||||
// } catch (Exception e) {
|
||||
// log.error(e.getMessage(),e);
|
||||
// result.error500("操作失败");
|
||||
// return result;
|
||||
// }
|
||||
// List<JSONObject> dictlist=new ArrayList<>();
|
||||
// for (DictModel l : ls) {
|
||||
// JSONObject dict=new JSONObject();
|
||||
// try {
|
||||
// dict.put("value",Integer.parseInt(l.getValue()));
|
||||
// } catch (NumberFormatException e) {
|
||||
// dict.put("value",l.getValue());
|
||||
// }
|
||||
// dict.put("label",l.getText());
|
||||
// dictlist.add(dict);
|
||||
// }
|
||||
// return dictlist;
|
||||
// }
|
||||
// @RequestMapping(value = "/getDictItemsByTable/{table}/{key}/{value}", method = RequestMethod.GET)
|
||||
// public Object getDictItemsByTable(@PathVariable String table,@PathVariable String key,@PathVariable String value) {
|
||||
// return this.ngAlainService.getDictByTable(table,key,value);
|
||||
// }
|
||||
//}
|
||||
@ -7,11 +7,13 @@ import com.baomidou.mybatisplus.core.conditions.query.QueryWrapper;
|
||||
import com.baomidou.mybatisplus.core.metadata.IPage;
|
||||
import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
import com.google.common.collect.Lists;
|
||||
import jakarta.servlet.http.HttpServletRequest;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.system.base.controller.JeecgController;
|
||||
import org.jeecg.common.system.query.QueryGenerator;
|
||||
import org.jeecg.common.system.util.JwtUtil;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.util.RedisUtil;
|
||||
import org.jeecg.common.util.RestUtil;
|
||||
import org.jeecg.modules.openapi.entity.OpenApi;
|
||||
@ -24,6 +26,7 @@ import org.jeecg.modules.openapi.service.OpenApiService;
|
||||
import org.jeecg.modules.openapi.swagger.*;
|
||||
import org.jeecg.modules.system.entity.SysUser;
|
||||
import org.jeecg.modules.system.service.ISysUserService;
|
||||
import org.springframework.beans.BeanUtils;
|
||||
import org.springframework.beans.factory.annotation.Autowired;
|
||||
import org.springframework.http.HttpEntity;
|
||||
import org.springframework.http.HttpHeaders;
|
||||
@ -33,7 +36,6 @@ import org.springframework.web.bind.annotation.*;
|
||||
import org.springframework.web.client.RestTemplate;
|
||||
import org.springframework.web.util.UriComponentsBuilder;
|
||||
|
||||
import jakarta.servlet.http.HttpServletRequest;
|
||||
import java.net.URI;
|
||||
import java.util.*;
|
||||
import java.util.stream.Collectors;
|
||||
@ -163,7 +165,7 @@ public class OpenApiController extends JeecgController<OpenApi, OpenApiService>
|
||||
String appkey = request.getHeader("appkey");
|
||||
OpenApiAuth openApiAuth = openApiAuthService.getByAppkey(appkey);
|
||||
SysUser systemUser = sysUserService.getUserByName(openApiAuth.getCreateBy());
|
||||
String token = this.getToken(systemUser.getUsername(), systemUser.getPassword());
|
||||
String token = this.getToken(systemUser);
|
||||
httpHeaders.put("X-Access-Token", Lists.newArrayList(token));
|
||||
httpHeaders.put("Content-Type",Lists.newArrayList("application/json"));
|
||||
HttpEntity<String> httpEntity = new HttpEntity<>(json, httpHeaders);
|
||||
@ -202,15 +204,13 @@ public class OpenApiController extends JeecgController<OpenApi, OpenApiService>
|
||||
/**
|
||||
* 生成接口访问令牌 Token
|
||||
*
|
||||
* @param USERNAME
|
||||
* @param PASSWORD
|
||||
* @return
|
||||
*/
|
||||
private String getToken(String USERNAME, String PASSWORD) {
|
||||
String token = JwtUtil.sign(USERNAME, PASSWORD, CommonConstant.CLIENT_TYPE_PC);
|
||||
redisUtil.set(CommonConstant.PREFIX_USER_TOKEN + token, token);
|
||||
redisUtil.expire(CommonConstant.PREFIX_USER_TOKEN + token, 60);
|
||||
return token;
|
||||
private String getToken(SysUser user) {
|
||||
// 使用封装方法:一步完成登录和设置用户信息
|
||||
LoginUser loginUser = new LoginUser();
|
||||
BeanUtils.copyProperties(user, loginUser);
|
||||
return LoginUserUtils.doLogin(loginUser);
|
||||
}
|
||||
|
||||
|
||||
|
||||
@ -1,7 +1,7 @@
|
||||
package org.jeecg.modules.openapi.controller;
|
||||
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.config.shiro.IgnoreAuth;
|
||||
import org.jeecg.config.satoken.IgnoreAuth;
|
||||
import org.springframework.web.bind.annotation.GetMapping;
|
||||
import org.springframework.web.bind.annotation.RequestMapping;
|
||||
import org.springframework.web.bind.annotation.RestController;
|
||||
|
||||
@ -2,8 +2,8 @@ package org.jeecg.modules.oss.controller;
|
||||
|
||||
import jakarta.servlet.http.HttpServletRequest;
|
||||
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import org.apache.shiro.authz.annotation.RequiresRoles;
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
import cn.dev33.satoken.annotation.SaCheckRole;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.system.query.QueryGenerator;
|
||||
import org.jeecg.modules.oss.entity.OssFile;
|
||||
@ -47,8 +47,8 @@ public class OssFileController {
|
||||
|
||||
@ResponseBody
|
||||
@PostMapping("/upload")
|
||||
//@RequiresRoles("admin")
|
||||
@RequiresPermissions("system:ossFile:upload")
|
||||
//@SaCheckRole("admin")
|
||||
@SaCheckPermission("system:ossFile:upload")
|
||||
public Result upload(@RequestParam("file") MultipartFile multipartFile) {
|
||||
Result result = new Result();
|
||||
try {
|
||||
|
||||
@ -6,9 +6,8 @@ import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
import io.swagger.v3.oas.annotations.tags.Tag;
|
||||
import io.swagger.v3.oas.annotations.Operation;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import org.apache.shiro.authz.annotation.RequiresRoles;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.constant.SymbolConstant;
|
||||
@ -80,8 +79,8 @@ public class QuartzJobController {
|
||||
* @param quartzJob
|
||||
* @return
|
||||
*/
|
||||
//@RequiresRoles("admin")
|
||||
@RequiresPermissions("system:quartzJob:add")
|
||||
//@SaCheckRole("admin")
|
||||
@SaCheckPermission("system:quartzJob:add")
|
||||
@RequestMapping(value = "/add", method = RequestMethod.POST)
|
||||
public Result<?> add(@RequestBody QuartzJob quartzJob) {
|
||||
quartzJobService.saveAndScheduleJob(quartzJob);
|
||||
@ -94,8 +93,8 @@ public class QuartzJobController {
|
||||
* @param quartzJob
|
||||
* @return
|
||||
*/
|
||||
//@RequiresRoles("admin")
|
||||
@RequiresPermissions("system:quartzJob:edit")
|
||||
//@SaCheckRole("admin")
|
||||
@SaCheckPermission("system:quartzJob:edit")
|
||||
@RequestMapping(value = "/edit", method ={RequestMethod.PUT, RequestMethod.POST})
|
||||
public Result<?> eidt(@RequestBody QuartzJob quartzJob) {
|
||||
try {
|
||||
@ -113,8 +112,8 @@ public class QuartzJobController {
|
||||
* @param id
|
||||
* @return
|
||||
*/
|
||||
//@RequiresRoles("admin")
|
||||
@RequiresPermissions("system:quartzJob:delete")
|
||||
//@SaCheckRole("admin")
|
||||
@SaCheckPermission("system:quartzJob:delete")
|
||||
@RequestMapping(value = "/delete", method = RequestMethod.DELETE)
|
||||
public Result<?> delete(@RequestParam(name = "id", required = true) String id) {
|
||||
QuartzJob quartzJob = quartzJobService.getById(id);
|
||||
@ -132,8 +131,8 @@ public class QuartzJobController {
|
||||
* @param ids
|
||||
* @return
|
||||
*/
|
||||
//@RequiresRoles("admin")
|
||||
@RequiresPermissions("system:quartzJob:deleteBatch")
|
||||
//@SaCheckRole("admin")
|
||||
@SaCheckPermission("system:quartzJob:deleteBatch")
|
||||
@RequestMapping(value = "/deleteBatch", method = RequestMethod.DELETE)
|
||||
public Result<?> deleteBatch(@RequestParam(name = "ids", required = true) String ids) {
|
||||
if (ids == null || "".equals(ids.trim())) {
|
||||
@ -152,8 +151,8 @@ public class QuartzJobController {
|
||||
* @param id
|
||||
* @return
|
||||
*/
|
||||
//@RequiresRoles("admin")
|
||||
@RequiresPermissions("system:quartzJob:pause")
|
||||
//@SaCheckRole("admin")
|
||||
@SaCheckPermission("system:quartzJob:pause")
|
||||
@GetMapping(value = "/pause")
|
||||
@Operation(summary = "停止定时任务")
|
||||
public Result<Object> pauseJob(@RequestParam(name = "id") String id) {
|
||||
@ -171,8 +170,8 @@ public class QuartzJobController {
|
||||
* @param id
|
||||
* @return
|
||||
*/
|
||||
//@RequiresRoles("admin")
|
||||
@RequiresPermissions("system:quartzJob:resume")
|
||||
//@SaCheckRole("admin")
|
||||
@SaCheckPermission("system:quartzJob:resume")
|
||||
@GetMapping(value = "/resume")
|
||||
@Operation(summary = "启动定时任务")
|
||||
public Result<Object> resumeJob(@RequestParam(name = "id") String id) {
|
||||
@ -220,7 +219,8 @@ public class QuartzJobController {
|
||||
mv.addObject(NormalExcelConstants.FILE_NAME, "定时任务列表");
|
||||
mv.addObject(NormalExcelConstants.CLASS, QuartzJob.class);
|
||||
//获取当前登录用户
|
||||
LoginUser user = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
//update-begin---author:wangshuai ---date:20211227 for:[JTC-116]导出人写死了------------
|
||||
LoginUser user = LoginUserUtils.getSessionUser();
|
||||
mv.addObject(NormalExcelConstants.PARAMS, new ExportParams("定时任务列表数据", "导出人:"+user.getRealname(), "导出信息"));
|
||||
mv.addObject(NormalExcelConstants.DATA_LIST, pageList);
|
||||
return mv;
|
||||
@ -276,8 +276,8 @@ public class QuartzJobController {
|
||||
* @param id
|
||||
* @return
|
||||
*/
|
||||
//@RequiresRoles("admin")
|
||||
@RequiresPermissions("system:quartzJob:execute")
|
||||
//@SaCheckRole("admin")
|
||||
@SaCheckPermission("system:quartzJob:execute")
|
||||
@GetMapping("/execute")
|
||||
public Result<?> execute(@RequestParam(name = "id", required = true) String id) {
|
||||
QuartzJob quartzJob = quartzJobService.getById(id);
|
||||
|
||||
@ -1,5 +1,6 @@
|
||||
package org.jeecg.modules.system.controller;
|
||||
|
||||
import cn.dev33.satoken.stp.StpUtil;
|
||||
import cn.hutool.core.util.RandomUtil;
|
||||
import com.alibaba.fastjson.JSONObject;
|
||||
import com.aliyuncs.exceptions.ClientException;
|
||||
@ -11,8 +12,9 @@ import jakarta.annotation.Resource;
|
||||
import jakarta.servlet.http.HttpServletRequest;
|
||||
import jakarta.servlet.http.HttpServletResponse;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.apache.shiro.authz.annotation.RequiresRoles;
|
||||
import org.apache.tomcat.util.threads.ThreadPoolExecutor;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import cn.dev33.satoken.annotation.SaCheckRole;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.constant.CacheConstant;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
@ -24,7 +26,7 @@ import org.jeecg.common.util.*;
|
||||
import org.jeecg.common.util.encryption.AesEncryptUtil;
|
||||
import org.jeecg.common.util.encryption.EncryptedString;
|
||||
import org.jeecg.config.JeecgBaseConfig;
|
||||
import org.jeecg.config.shiro.IgnoreAuth;
|
||||
import org.jeecg.config.satoken.IgnoreAuth;
|
||||
import org.jeecg.modules.base.service.BaseCommonService;
|
||||
import org.jeecg.modules.system.entity.SysDepart;
|
||||
import org.jeecg.modules.system.entity.SysRoleIndex;
|
||||
@ -75,8 +77,7 @@ public class LoginController {
|
||||
/**
|
||||
* 线程池用于异步发送纪要
|
||||
*/
|
||||
public static ExecutorService cachedThreadPool = new ShiroThreadPoolExecutor(0, 1024, 60L, TimeUnit.SECONDS, new SynchronousQueue<>());
|
||||
|
||||
public static ExecutorService cachedThreadPool = new ThreadPoolExecutor(0, 1024, 60L, TimeUnit.SECONDS, new SynchronousQueue<>());
|
||||
|
||||
|
||||
@Operation(summary="登录接口")
|
||||
@ -141,7 +142,8 @@ public class LoginController {
|
||||
public Result<JSONObject> getUserInfo(HttpServletRequest request){
|
||||
long start = System.currentTimeMillis();
|
||||
Result<JSONObject> result = new Result<JSONObject>();
|
||||
String username = JwtUtil.getUserNameByToken(request);
|
||||
// 使用Sa-Token获取登录用户名(loginId现在是username)
|
||||
String username = StpUtil.getLoginIdAsString();
|
||||
if(oConvertUtils.isNotEmpty(username)) {
|
||||
// 根据用户名查询用户信息
|
||||
SysUser sysUser = sysUserService.getUserByName(username);
|
||||
@ -189,7 +191,8 @@ public class LoginController {
|
||||
LoginUser sysUser = sysBaseApi.getUserByName(username);
|
||||
if(sysUser!=null) {
|
||||
asyncClearLogoutCache(token, sysUser); // 异步清理
|
||||
SecurityUtils.getSubject().logout();
|
||||
// 使用Sa-Token退出登录
|
||||
StpUtil.logout();
|
||||
return Result.ok("退出登录成功!");
|
||||
}else {
|
||||
return Result.error("Token无效!");
|
||||
@ -197,25 +200,17 @@ public class LoginController {
|
||||
}
|
||||
|
||||
/**
|
||||
* 清理用户缓存
|
||||
*
|
||||
* 清理用户缓存(使用Sa-Token)
|
||||
*
|
||||
* @param token
|
||||
* @param sysUser
|
||||
*/
|
||||
private void asyncClearLogoutCache(String token, LoginUser sysUser) {
|
||||
cachedThreadPool.execute(()->{
|
||||
//清空用户登录Token缓存
|
||||
redisUtil.del(CommonConstant.PREFIX_USER_TOKEN + token);
|
||||
//清空用户登录Shiro权限缓存
|
||||
redisUtil.del(CommonConstant.PREFIX_USER_SHIRO_CACHE + sysUser.getId());
|
||||
//清空用户的缓存信息(包括部门信息),例如sys:cache:user::<username>
|
||||
redisUtil.del(String.format("%s::%s", CacheConstant.SYS_USERS_CACHE, sysUser.getUsername()));
|
||||
//清空是否允许同一账号多地同时登录缓存(PC端和APP端)
|
||||
redisUtil.del(CommonConstant.PREFIX_USER_TOKEN_PC + sysUser.getUsername());
|
||||
redisUtil.del(CommonConstant.PREFIX_USER_TOKEN_APP + sysUser.getUsername());
|
||||
redisUtil.del(CommonConstant.PREFIX_USER_TOKEN_PHONE + sysUser.getUsername());
|
||||
baseCommonService.addLog("用户名: "+sysUser.getRealname()+",退出成功!", CommonConstant.LOG_TYPE_1, null, sysUser);
|
||||
log.debug("【退出成功操作】异步处理,退出后,清理用户缓存: "+sysUser.getRealname());
|
||||
log.info("【退出成功】异步清理用户缓存: {} ", sysUser.getRealname());
|
||||
});
|
||||
}
|
||||
|
||||
@ -280,7 +275,7 @@ public class LoginController {
|
||||
Result<JSONObject> result = new Result<JSONObject>();
|
||||
String username = user.getUsername();
|
||||
if(oConvertUtils.isEmpty(username)) {
|
||||
LoginUser sysUser = (LoginUser)SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
username = sysUser.getUsername();
|
||||
}
|
||||
|
||||
@ -462,19 +457,12 @@ public class LoginController {
|
||||
String syspassword = sysUser.getPassword();
|
||||
JSONObject obj = new JSONObject(new LinkedHashMap<>());
|
||||
|
||||
//1.生成token,并设置超时时间
|
||||
String token = JwtUtil.sign(username, syspassword, clientType);
|
||||
redisUtil.set(CommonConstant.PREFIX_USER_TOKEN + token, token);
|
||||
// 根据客户端类型设置对应的过期时间
|
||||
long expireTime = CommonConstant.CLIENT_TYPE_APP.equalsIgnoreCase(clientType)
|
||||
? JwtUtil.APP_EXPIRE_TIME * 2 / 1000
|
||||
: JwtUtil.EXPIRE_TIME * 2 / 1000;
|
||||
redisUtil.expire(CommonConstant.PREFIX_USER_TOKEN + token, expireTime);
|
||||
//1.使用sa-token生成token(使用username作为loginId,将用户信息存入session)
|
||||
LoginUser loginUser = new LoginUser();
|
||||
BeanUtils.copyProperties(sysUser, loginUser);
|
||||
String token = LoginUserUtils.doLogin(loginUser);
|
||||
obj.put("token", token);
|
||||
|
||||
// 是否允许同一账号多地同时登录,踢掉之前的登录
|
||||
handleSingleSignOn(username, token, clientType);
|
||||
|
||||
//2.设置登录租户
|
||||
Result<JSONObject> loginTenantError = sysUserService.setLoginTenant(sysUser, obj, username,result);
|
||||
if (loginTenantError != null) {
|
||||
@ -529,55 +517,7 @@ public class LoginController {
|
||||
result.success("登录成功");
|
||||
return result;
|
||||
}
|
||||
|
||||
/**
|
||||
* 同一账号在同一客户端类型只能登录一次
|
||||
*
|
||||
* @author scott
|
||||
* @date 2025-10-31
|
||||
* PC端、APP端、手机号登录分别独立,互不影响
|
||||
*
|
||||
* @param username 用户名
|
||||
* @param newToken 新生成的token
|
||||
* @param clientType 客户端类型(PC、APP、PHONE)
|
||||
*/
|
||||
private void handleSingleSignOn(String username, String newToken, String clientType) {
|
||||
// 检查是否允许并发登录
|
||||
if (jeecgBaseConfig.getFirewall() == null || jeecgBaseConfig.getFirewall().getIsConcurrent()==null || Boolean.TRUE.equals(jeecgBaseConfig.getFirewall().getIsConcurrent())) {
|
||||
// 允许并发登录,只设置当前用户的token缓存,不踢掉之前的登录
|
||||
log.debug("并发登录已启用:用户[{}]在{}端允许多地同时登录", username, clientType);
|
||||
return;
|
||||
}
|
||||
|
||||
log.info("【并发登录限制已开启】 用户[{}]在{}端不允许多地同时登录", username, clientType);
|
||||
// 根据客户端类型选择对应的Redis key前缀
|
||||
String redisKeyPrefix;
|
||||
if (CommonConstant.CLIENT_TYPE_APP.equalsIgnoreCase(clientType)) {
|
||||
redisKeyPrefix = CommonConstant.PREFIX_USER_TOKEN_APP;
|
||||
} else if (CommonConstant.CLIENT_TYPE_PHONE.equalsIgnoreCase(clientType)) {
|
||||
redisKeyPrefix = CommonConstant.PREFIX_USER_TOKEN_PHONE;
|
||||
} else {
|
||||
redisKeyPrefix = CommonConstant.PREFIX_USER_TOKEN_PC;
|
||||
}
|
||||
|
||||
String userTokenKey = redisKeyPrefix + username;
|
||||
|
||||
// 获取该用户在当前客户端类型下之前的token
|
||||
Object oldTokenObj = redisUtil.get(userTokenKey);
|
||||
if (oldTokenObj != null && !oldTokenObj.equals(newToken)) {
|
||||
String oldToken = oldTokenObj.toString();
|
||||
// 清除旧登录token的缓存(设置 1 小时过期时间)
|
||||
redisUtil.del(CommonConstant.PREFIX_USER_TOKEN + oldToken);
|
||||
redisUtil.set(CommonConstant.PREFIX_USER_TOKEN_ERROR_MSG + oldToken, "不允许同一账号多地同时登录,当前登录被踢掉!", 60 * 1 * 60);
|
||||
log.info("【并发登录限制已开启】用户[{}]在{}端的旧登录已被踢下线!", username, clientType);
|
||||
log.info("【并发登录限制已开启】用户被踢下线,新token: {},旧token:{}", newToken, oldToken);
|
||||
}
|
||||
|
||||
// 保存新的token到单点登录缓存
|
||||
redisUtil.set(userTokenKey, newToken);
|
||||
redisUtil.expire(userTokenKey, JwtUtil.EXPIRE_TIME * 2 / 1000);
|
||||
}
|
||||
|
||||
|
||||
/**
|
||||
* 获取加密字符串
|
||||
* @return
|
||||
@ -624,7 +564,7 @@ public class LoginController {
|
||||
// /**
|
||||
// * 切换菜单表为vue3的表
|
||||
// */
|
||||
// @RequiresRoles({"admin"})
|
||||
// @SaCheckRole({"admin"})
|
||||
// @GetMapping(value = "/switchVue3Menu")
|
||||
// public Result<String> switchVue3Menu(HttpServletResponse response) {
|
||||
// Result<String> res = new Result<String>();
|
||||
@ -701,18 +641,16 @@ public class LoginController {
|
||||
obj.put("userInfo", sysUser);
|
||||
|
||||
//6. 生成token,并设置超时时间
|
||||
String token = JwtUtil.sign(username, syspassword, CommonConstant.CLIENT_TYPE_APP);
|
||||
redisUtil.set(CommonConstant.PREFIX_USER_TOKEN + token, token);
|
||||
redisUtil.expire(CommonConstant.PREFIX_USER_TOKEN + token, JwtUtil.APP_EXPIRE_TIME*2 / 1000);
|
||||
obj.put("token", token);
|
||||
LoginUser loginUser = new LoginUser();
|
||||
BeanUtils.copyProperties(sysUser, loginUser);
|
||||
String token = LoginUserUtils.doLogin(loginUser);
|
||||
log.info("App登录成功,用户名:{},token={}", username, token);
|
||||
|
||||
//token 信息
|
||||
obj.put("token", token);
|
||||
result.setResult(obj);
|
||||
result.setSuccess(true);
|
||||
result.setCode(200);
|
||||
|
||||
// 7.是否允许同一账号多地同时登录(APP端登录,踢掉之前的APP端登录)
|
||||
handleSingleSignOn(username, token, CommonConstant.CLIENT_TYPE_APP);
|
||||
|
||||
// 8.登录成功记录日志
|
||||
baseCommonService.addLog("用户名: " + username + ",登录成功[移动端]!", CommonConstant.LOG_TYPE_1, null);
|
||||
return result;
|
||||
}
|
||||
@ -838,7 +776,7 @@ public class LoginController {
|
||||
result.setSuccess(false);
|
||||
return result;
|
||||
}
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
String username = sysUser.getUsername();
|
||||
LambdaQueryWrapper<SysUser> query = new LambdaQueryWrapper<>();
|
||||
query.eq(SysUser::getUsername, username).eq(SysUser::getPhone, mobile);
|
||||
|
||||
@ -10,6 +10,7 @@ import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.commons.lang.StringUtils;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.api.dto.PushMessageDTO;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.config.TenantContext;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
@ -98,8 +99,8 @@ public class SysAnnouncementController {
|
||||
/**
|
||||
* QQYUN-5072【性能优化】线上通知消息打开有点慢
|
||||
*/
|
||||
public static ExecutorService cachedThreadPool = new ShiroThreadPoolExecutor(0, 1024,60L, TimeUnit.SECONDS, new SynchronousQueue<Runnable>());
|
||||
public static ExecutorService completeNoteThreadPool = new ShiroThreadPoolExecutor(0, 1024,60L, TimeUnit.SECONDS, new SynchronousQueue<Runnable>());
|
||||
public static ExecutorService cachedThreadPool = new ThreadPoolExecutor(0, 1024,60L, TimeUnit.SECONDS, new SynchronousQueue<Runnable>());
|
||||
public static ExecutorService completeNoteThreadPool = new ThreadPoolExecutor(0, 1024,60L, TimeUnit.SECONDS, new SynchronousQueue<Runnable>());
|
||||
|
||||
/**
|
||||
* 分页列表查询
|
||||
@ -388,7 +389,7 @@ public class SysAnnouncementController {
|
||||
long start = System.currentTimeMillis();
|
||||
Result<Map<String,Object>> result = new Result<Map<String,Object>>();
|
||||
Map<String,Object> sysMsgMap = new HashMap(5);
|
||||
LoginUser sysUser = (LoginUser)SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
String userId = sysUser.getId();
|
||||
|
||||
|
||||
@ -431,7 +432,7 @@ public class SysAnnouncementController {
|
||||
*/
|
||||
@RequestMapping(value = "/getUnreadMessageCount", method = RequestMethod.GET)
|
||||
public Result<Map<String, Integer>> getUnreadMessageCount(@RequestParam(required = false, defaultValue = "5") Integer pageSize, HttpServletRequest request) {
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
String userId = sysUser.getId();
|
||||
|
||||
// 获取上个月的第一天(只查近两个月的通知)
|
||||
@ -473,7 +474,7 @@ public class SysAnnouncementController {
|
||||
//导出文件名称
|
||||
mv.addObject(NormalExcelConstants.FILE_NAME, "系统通告列表");
|
||||
mv.addObject(NormalExcelConstants.CLASS, SysAnnouncement.class);
|
||||
LoginUser user = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser user = LoginUserUtils.getSessionUser();
|
||||
mv.addObject(NormalExcelConstants.PARAMS, new ExportParams("系统通告列表数据", "导出人:"+user.getRealname(), "导出信息"));
|
||||
mv.addObject(NormalExcelConstants.DATA_LIST, pageList);
|
||||
return mv;
|
||||
@ -574,7 +575,7 @@ public class SysAnnouncementController {
|
||||
boolean tokenOk = false;
|
||||
try {
|
||||
// 验证Token有效性
|
||||
tokenOk = TokenUtils.verifyToken(request, sysBaseApi, redisUtil);
|
||||
tokenOk = TokenUtils.verifyToken(request, sysBaseApi);
|
||||
} catch (Exception ignored) {
|
||||
}
|
||||
// 判断是否传递了Token,并且Token有效,如果传了就不做查看限制,直接返回
|
||||
@ -650,7 +651,7 @@ public class SysAnnouncementController {
|
||||
|
||||
JSONObject obj = new JSONObject();
|
||||
obj.put(WebsocketConst.MSG_CMD, WebsocketConst.CMD_USER);
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
webSocket.sendMessage(sysUser.getId(), obj.toJSONString());
|
||||
|
||||
// 4、性能统计耗时
|
||||
|
||||
@ -6,7 +6,7 @@ import java.util.Date;
|
||||
import jakarta.servlet.http.HttpServletRequest;
|
||||
|
||||
import org.apache.commons.lang3.StringUtils;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.constant.DataBaseConstant;
|
||||
@ -196,7 +196,7 @@ public class SysAnnouncementSendController {
|
||||
public Result<SysAnnouncementSend> editById(@RequestBody JSONObject json) {
|
||||
Result<SysAnnouncementSend> result = new Result<SysAnnouncementSend>();
|
||||
String anntId = json.getString("anntId");
|
||||
LoginUser sysUser = (LoginUser)SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
String userId = sysUser.getId();
|
||||
LambdaUpdateWrapper<SysAnnouncementSend> updateWrapper = new UpdateWrapper().lambda();
|
||||
updateWrapper.set(SysAnnouncementSend::getReadFlag, CommonConstant.HAS_READ_FLAG);
|
||||
@ -220,7 +220,7 @@ public class SysAnnouncementSendController {
|
||||
@RequestParam(name="pageNo", defaultValue="1") Integer pageNo,
|
||||
@RequestParam(name="pageSize", defaultValue="10") Integer pageSize) {
|
||||
Result<IPage<AnnouncementSendModel>> result = new Result<IPage<AnnouncementSendModel>>();
|
||||
LoginUser sysUser = (LoginUser)SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
String userId = sysUser.getId();
|
||||
announcementSendModel.setUserId(userId);
|
||||
announcementSendModel.setPageNo((pageNo-1)*pageSize);
|
||||
@ -246,7 +246,7 @@ public class SysAnnouncementSendController {
|
||||
@PutMapping(value = "/readAll")
|
||||
public Result<SysAnnouncementSend> readAll() {
|
||||
Result<SysAnnouncementSend> result = new Result<SysAnnouncementSend>();
|
||||
LoginUser sysUser = (LoginUser)SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
String userId = sysUser.getId();
|
||||
LambdaUpdateWrapper<SysAnnouncementSend> updateWrapper = new UpdateWrapper().lambda();
|
||||
updateWrapper.set(SysAnnouncementSend::getReadFlag, CommonConstant.HAS_READ_FLAG);
|
||||
@ -290,7 +290,7 @@ public class SysAnnouncementSendController {
|
||||
//刷新未读数量
|
||||
JSONObject obj = new JSONObject();
|
||||
obj.put(WebsocketConst.MSG_CMD, WebsocketConst.CMD_USER);
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
webSocket.sendMessage(sysUser.getId(), obj.toJSONString());
|
||||
|
||||
return Result.ok();
|
||||
|
||||
@ -3,7 +3,7 @@ package org.jeecg.modules.system.controller;
|
||||
import io.swagger.v3.oas.annotations.Operation;
|
||||
import io.swagger.v3.oas.annotations.tags.Tag;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.authz.annotation.RequiresRoles;
|
||||
import cn.dev33.satoken.annotation.SaCheckRole;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.util.RedisUtil;
|
||||
import org.jeecg.common.util.oConvertUtils;
|
||||
@ -57,7 +57,7 @@ public class SysAppVersionController{
|
||||
* @param sysAppVersion
|
||||
* @return
|
||||
*/
|
||||
@RequiresRoles({"admin"})
|
||||
@SaCheckRole({"admin"})
|
||||
@Operation(summary="app系统配置-保存")
|
||||
@PostMapping(value = "/saveVersion")
|
||||
public Result<?> saveVersion(@RequestBody SysAppVersion sysAppVersion) {
|
||||
|
||||
@ -7,7 +7,7 @@ import com.baomidou.mybatisplus.core.metadata.IPage;
|
||||
import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.commons.lang.StringUtils;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.config.TenantContext;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
@ -238,7 +238,7 @@ public class SysCategoryController {
|
||||
//导出文件名称
|
||||
mv.addObject(NormalExcelConstants.FILE_NAME, "分类字典列表");
|
||||
mv.addObject(NormalExcelConstants.CLASS, SysCategory.class);
|
||||
LoginUser user = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser user = LoginUserUtils.getSessionUser();
|
||||
//导出支持xlsx
|
||||
mv.addObject(NormalExcelConstants.PARAMS, new ExportParams("分类字典列表数据", "导出人:"+user.getRealname(), "导出信息", ExcelType.XSSF));
|
||||
//分类字典导出支持导出字段
|
||||
|
||||
@ -6,7 +6,7 @@ import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
import io.swagger.v3.oas.annotations.tags.Tag;
|
||||
import io.swagger.v3.oas.annotations.Operation;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.api.dto.DataLogDTO;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
@ -126,7 +126,7 @@ public class SysCommentController extends JeecgController<SysComment, ISysCommen
|
||||
if(comment==null){
|
||||
return Result.error("该评论已被删除!");
|
||||
}
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
String username = sysUser.getUsername();
|
||||
String admin = "admin";
|
||||
//除了admin外 其他人只能删除自己的评论
|
||||
@ -182,7 +182,7 @@ public class SysCommentController extends JeecgController<SysComment, ISysCommen
|
||||
* @return
|
||||
*/
|
||||
@Operation(summary = "系统评论回复表-添加")
|
||||
//@RequiresPermissions("org.jeecg.modules.demo:sys_comment:add")
|
||||
//@SaCheckPermission("org.jeecg.modules.demo:sys_comment:add")
|
||||
@PostMapping(value = "/add")
|
||||
public Result<String> add(@RequestBody SysComment sysComment) {
|
||||
sysCommentService.save(sysComment);
|
||||
@ -197,7 +197,7 @@ public class SysCommentController extends JeecgController<SysComment, ISysCommen
|
||||
*/
|
||||
//@AutoLog(value = "系统评论回复表-编辑")
|
||||
@Operation(summary = "系统评论回复表-编辑")
|
||||
//@RequiresPermissions("org.jeecg.modules.demo:sys_comment:edit")
|
||||
//@SaCheckPermission("org.jeecg.modules.demo:sys_comment:edit")
|
||||
@RequestMapping(value = "/edit", method = {RequestMethod.PUT, RequestMethod.POST})
|
||||
public Result<String> edit(@RequestBody SysComment sysComment) {
|
||||
sysCommentService.updateById(sysComment);
|
||||
@ -212,7 +212,7 @@ public class SysCommentController extends JeecgController<SysComment, ISysCommen
|
||||
*/
|
||||
//@AutoLog(value = "系统评论回复表-通过id删除")
|
||||
@Operation(summary = "系统评论回复表-通过id删除")
|
||||
//@RequiresPermissions("org.jeecg.modules.demo:sys_comment:delete")
|
||||
//@SaCheckPermission("org.jeecg.modules.demo:sys_comment:delete")
|
||||
@DeleteMapping(value = "/delete")
|
||||
public Result<String> delete(@RequestParam(name = "id", required = true) String id) {
|
||||
sysCommentService.removeById(id);
|
||||
@ -227,7 +227,7 @@ public class SysCommentController extends JeecgController<SysComment, ISysCommen
|
||||
*/
|
||||
//@AutoLog(value = "系统评论回复表-批量删除")
|
||||
@Operation(summary = "系统评论回复表-批量删除")
|
||||
//@RequiresPermissions("org.jeecg.modules.demo:sys_comment:deleteBatch")
|
||||
//@SaCheckPermission("org.jeecg.modules.demo:sys_comment:deleteBatch")
|
||||
@DeleteMapping(value = "/deleteBatch")
|
||||
public Result<String> deleteBatch(@RequestParam(name = "ids", required = true) String ids) {
|
||||
this.sysCommentService.removeByIds(Arrays.asList(ids.split(",")));
|
||||
@ -257,7 +257,7 @@ public class SysCommentController extends JeecgController<SysComment, ISysCommen
|
||||
* @param request
|
||||
* @param sysComment
|
||||
*/
|
||||
//@RequiresPermissions("org.jeecg.modules.demo:sys_comment:exportXls")
|
||||
//@SaCheckPermission("org.jeecg.modules.demo:sys_comment:exportXls")
|
||||
@RequestMapping(value = "/exportXls")
|
||||
public ModelAndView exportXls(HttpServletRequest request, SysComment sysComment) {
|
||||
return super.exportXls(request, sysComment, SysComment.class, "系统评论回复表");
|
||||
@ -270,7 +270,7 @@ public class SysCommentController extends JeecgController<SysComment, ISysCommen
|
||||
* @param response
|
||||
* @return
|
||||
*/
|
||||
//@RequiresPermissions("sys_comment:importExcel")
|
||||
//@SaCheckPermission("sys_comment:importExcel")
|
||||
@RequestMapping(value = "/importExcel", method = RequestMethod.POST)
|
||||
public Result<?> importExcel(HttpServletRequest request, HttpServletResponse response) {
|
||||
return super.importExcel(request, response, SysComment.class);
|
||||
|
||||
@ -11,8 +11,8 @@ import io.swagger.v3.oas.annotations.tags.Tag;
|
||||
import io.swagger.v3.oas.annotations.Operation;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.commons.lang.StringUtils;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import org.apache.shiro.authz.annotation.RequiresRoles;
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
import cn.dev33.satoken.annotation.SaCheckRole;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.aspect.annotation.AutoLog;
|
||||
import org.jeecg.common.config.TenantContext;
|
||||
@ -63,7 +63,7 @@ public class SysDataSourceController extends JeecgController<SysDataSource, ISys
|
||||
*/
|
||||
@AutoLog(value = "多数据源管理-分页列表查询")
|
||||
@Operation(summary = "多数据源管理-分页列表查询")
|
||||
@RequiresPermissions("system:datasource:list")
|
||||
@SaCheckPermission("system:datasource:list")
|
||||
@GetMapping(value = "/list")
|
||||
public Result<?> queryPageList(
|
||||
SysDataSource sysDataSource,
|
||||
|
||||
@ -1,14 +1,14 @@
|
||||
package org.jeecg.modules.system.controller;
|
||||
|
||||
import cn.dev33.satoken.annotation.SaCheckRole;
|
||||
import com.alibaba.fastjson.JSONObject;
|
||||
import com.baomidou.mybatisplus.core.conditions.query.LambdaQueryWrapper;
|
||||
import com.baomidou.mybatisplus.core.metadata.IPage;
|
||||
import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.commons.lang3.StringUtils;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import org.apache.shiro.authz.annotation.RequiresRoles;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.config.TenantContext;
|
||||
import org.jeecg.common.constant.CacheConstant;
|
||||
@ -19,6 +19,8 @@ import org.jeecg.common.util.ImportExcelUtil;
|
||||
import org.jeecg.common.util.RedisUtil;
|
||||
import org.jeecg.common.util.oConvertUtils;
|
||||
import org.jeecg.config.mybatis.MybatisPlusSaasConfig;
|
||||
import org.jeecg.modules.jmreport.common.annotation.RequiresPermissions;
|
||||
import org.jeecg.modules.jmreport.common.annotation.RequiresRoles;
|
||||
import org.jeecg.modules.system.entity.SysDepart;
|
||||
import org.jeecg.modules.system.entity.SysUser;
|
||||
import org.jeecg.modules.system.excelstyle.ExcelExportSysUserStyle;
|
||||
@ -80,7 +82,7 @@ public class SysDepartController {
|
||||
@RequestMapping(value = "/queryMyDeptTreeList", method = RequestMethod.GET)
|
||||
public Result<List<SysDepartTreeModel>> queryMyDeptTreeList() {
|
||||
Result<List<SysDepartTreeModel>> result = new Result<>();
|
||||
LoginUser user = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser user = LoginUserUtils.getSessionUser();
|
||||
try {
|
||||
if(oConvertUtils.isNotEmpty(user.getUserIdentity()) && user.getUserIdentity().equals( CommonConstant.USER_IDENTITY_2 )){
|
||||
// 代码逻辑说明: 部门查询ids为空后的前端显示问题 issues/I3UD06
|
||||
@ -209,7 +211,7 @@ public class SysDepartController {
|
||||
* @param sysDepart
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:depart:add")
|
||||
@SaCheckPermission("system:depart:add")
|
||||
@RequestMapping(value = "/add", method = RequestMethod.POST)
|
||||
@CacheEvict(value= {CacheConstant.SYS_DEPARTS_CACHE,CacheConstant.SYS_DEPART_IDS_CACHE}, allEntries=true)
|
||||
public Result<SysDepart> add(@RequestBody SysDepart sysDepart, HttpServletRequest request) {
|
||||
@ -235,7 +237,7 @@ public class SysDepartController {
|
||||
* @param sysDepart
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:depart:edit")
|
||||
@SaCheckPermission("system:depart:edit")
|
||||
@RequestMapping(value = "/edit", method = {RequestMethod.PUT,RequestMethod.POST})
|
||||
@CacheEvict(value= {CacheConstant.SYS_DEPARTS_CACHE,CacheConstant.SYS_DEPART_IDS_CACHE}, allEntries=true)
|
||||
public Result<SysDepart> edit(@RequestBody SysDepart sysDepart, HttpServletRequest request) {
|
||||
@ -263,7 +265,7 @@ public class SysDepartController {
|
||||
* @param id
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:depart:delete")
|
||||
@SaCheckPermission("system:depart:delete")
|
||||
@RequestMapping(value = "/delete", method = RequestMethod.DELETE)
|
||||
@CacheEvict(value= {CacheConstant.SYS_DEPARTS_CACHE,CacheConstant.SYS_DEPART_IDS_CACHE}, allEntries=true)
|
||||
public Result<SysDepart> delete(@RequestParam(name="id",required=true) String id) {
|
||||
@ -289,7 +291,7 @@ public class SysDepartController {
|
||||
* @param ids
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:depart:deleteBatch")
|
||||
@SaCheckPermission("system:depart:deleteBatch")
|
||||
@RequestMapping(value = "/deleteBatch", method = RequestMethod.DELETE)
|
||||
@CacheEvict(value= {CacheConstant.SYS_DEPARTS_CACHE,CacheConstant.SYS_DEPART_IDS_CACHE}, allEntries=true)
|
||||
public Result<SysDepart> deleteBatch(@RequestParam(name = "ids", required = true) String ids) {
|
||||
@ -356,7 +358,7 @@ public class SysDepartController {
|
||||
@RequestParam(name = "departIds", required = false) String depIds) {
|
||||
Result<List<SysDepartTreeModel>> result = new Result<List<SysDepartTreeModel>>();
|
||||
//部门查询,myDeptSearch为1时为我的部门查询,登录用户为上级时查只查负责部门下数据
|
||||
LoginUser user = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser user = LoginUserUtils.getSessionUser();
|
||||
String departIds = null;
|
||||
if(oConvertUtils.isNotEmpty(user.getUserIdentity()) && user.getUserIdentity().equals( CommonConstant.USER_IDENTITY_2 )){
|
||||
departIds = user.getDepartIds();
|
||||
@ -411,7 +413,7 @@ public class SysDepartController {
|
||||
//导出文件名称
|
||||
mv.addObject(NormalExcelConstants.FILE_NAME, "部门列表");
|
||||
mv.addObject(NormalExcelConstants.CLASS, SysDepartExportVo.class);
|
||||
LoginUser user = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser user = LoginUserUtils.getSessionUser();
|
||||
ExportParams exportParams = new ExportParams("导入规则:\n" +
|
||||
"1、标题为第三行,部门路径和部门名称的标题不允许修改,否则会匹配失败;第四行为数据填写范围;\n" +
|
||||
"2、部门路径用英文字符/分割,部门名称为部门路径的最后一位;\n" +
|
||||
@ -434,7 +436,7 @@ public class SysDepartController {
|
||||
* @param response
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:depart:importExcel")
|
||||
@SaCheckPermission("system:depart:importExcel")
|
||||
@RequestMapping(value = "/importExcel", method = RequestMethod.POST)
|
||||
@CacheEvict(value= {CacheConstant.SYS_DEPARTS_CACHE,CacheConstant.SYS_DEPART_IDS_CACHE}, allEntries=true)
|
||||
public Result<?> importExcel(HttpServletRequest request, HttpServletResponse response) {
|
||||
@ -668,7 +670,7 @@ public class SysDepartController {
|
||||
//导出文件名称
|
||||
mv.addObject(NormalExcelConstants.FILE_NAME, "部门列表");
|
||||
mv.addObject(NormalExcelConstants.CLASS, ExportDepartVo.class);
|
||||
LoginUser user = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser user = LoginUserUtils.getSessionUser();
|
||||
mv.addObject(NormalExcelConstants.PARAMS, new ExportParams("部门列表数据", "导出人:"+user.getRealname(), "导出信息"));
|
||||
mv.addObject(NormalExcelConstants.DATA_LIST, pageList);
|
||||
return mv;
|
||||
@ -771,8 +773,8 @@ public class SysDepartController {
|
||||
* @return
|
||||
*/
|
||||
@PutMapping("/updateChangeDepart")
|
||||
@RequiresPermissions("system:depart:updateChange")
|
||||
@RequiresRoles({"admin"})
|
||||
@SaCheckPermission("system:depart:updateChange")
|
||||
@SaCheckRole({"admin"})
|
||||
public Result<String> updateChangeDepart(@RequestBody SysChangeDepartVo changeDepartVo) {
|
||||
sysDepartService.updateChangeDepart(changeDepartVo);
|
||||
return Result.ok("调整部门位置成功!");
|
||||
|
||||
@ -7,11 +7,10 @@ import jakarta.servlet.http.HttpServletResponse;
|
||||
|
||||
import com.alibaba.fastjson.JSONObject;
|
||||
import com.baomidou.mybatisplus.core.conditions.query.LambdaQueryWrapper;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.system.query.QueryGenerator;
|
||||
import org.jeecg.common.aspect.annotation.AutoLog;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.jeecg.common.util.oConvertUtils;
|
||||
import org.jeecg.modules.base.service.BaseCommonService;
|
||||
@ -260,7 +259,7 @@ public class SysDepartPermissionController extends JeecgController<SysDepartPerm
|
||||
this.sysDepartRolePermissionService.saveDeptRolePermission(roleId, permissionIds, lastPermissionIds);
|
||||
result.success("保存成功!");
|
||||
// 代码逻辑说明: [VUEN-234]部门角色授权添加敏感日志------------
|
||||
LoginUser loginUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser loginUser = LoginUserUtils.getSessionUser();
|
||||
baseCommonService.addLog("修改部门角色ID:"+roleId+"的权限配置,操作人: " +loginUser.getUsername() ,CommonConstant.LOG_TYPE_2, 2);
|
||||
log.info("======部门角色授权成功=====耗时:" + (System.currentTimeMillis() - start) + "毫秒");
|
||||
} catch (Exception e) {
|
||||
|
||||
@ -7,9 +7,8 @@ import jakarta.servlet.http.HttpServletResponse;
|
||||
|
||||
import com.alibaba.fastjson.JSONObject;
|
||||
import com.baomidou.mybatisplus.core.conditions.query.LambdaQueryWrapper;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import org.apache.shiro.authz.annotation.RequiresRoles;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.system.query.QueryGenerator;
|
||||
@ -78,7 +77,7 @@ public class SysDepartRoleController extends JeecgController<SysDepartRole, ISys
|
||||
HttpServletRequest req) {
|
||||
QueryWrapper<SysDepartRole> queryWrapper = QueryGenerator.initQueryWrapper(sysDepartRole, req.getParameterMap());
|
||||
Page<SysDepartRole> page = new Page<SysDepartRole>(pageNo, pageSize);
|
||||
// LoginUser user = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
// LoginUser user = LoginUserUtils.getLoginUser();
|
||||
// List<String> deptIds = null;
|
||||
// if(oConvertUtils.isEmpty(deptId)){
|
||||
// if(oConvertUtils.isNotEmpty(user.getUserIdentity()) && user.getUserIdentity().equals(CommonConstant.USER_IDENTITY_2) ){
|
||||
@ -108,7 +107,7 @@ public class SysDepartRoleController extends JeecgController<SysDepartRole, ISys
|
||||
* @param sysDepartRole
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:depart:role:add")
|
||||
@SaCheckPermission("system:depart:role:add")
|
||||
@Operation(summary="部门角色-添加")
|
||||
@PostMapping(value = "/add")
|
||||
public Result<?> add(@RequestBody SysDepartRole sysDepartRole) {
|
||||
@ -123,7 +122,7 @@ public class SysDepartRoleController extends JeecgController<SysDepartRole, ISys
|
||||
* @return
|
||||
*/
|
||||
@Operation(summary="部门角色-编辑")
|
||||
@RequiresPermissions("system:depart:role:edit")
|
||||
@SaCheckPermission("system:depart:role:edit")
|
||||
@RequestMapping(value = "/edit", method = {RequestMethod.PUT,RequestMethod.POST})
|
||||
public Result<?> edit(@RequestBody SysDepartRole sysDepartRole) {
|
||||
sysDepartRoleService.updateById(sysDepartRole);
|
||||
@ -138,7 +137,7 @@ public class SysDepartRoleController extends JeecgController<SysDepartRole, ISys
|
||||
*/
|
||||
@AutoLog(value = "部门角色-通过id删除")
|
||||
@Operation(summary="部门角色-通过id删除")
|
||||
@RequiresPermissions("system:depart:role:delete")
|
||||
@SaCheckPermission("system:depart:role:delete")
|
||||
@DeleteMapping(value = "/delete")
|
||||
public Result<?> delete(@RequestParam(name="id",required=true) String id) {
|
||||
sysDepartRoleService.removeById(id);
|
||||
@ -153,7 +152,7 @@ public class SysDepartRoleController extends JeecgController<SysDepartRole, ISys
|
||||
*/
|
||||
@AutoLog(value = "部门角色-批量删除")
|
||||
@Operation(summary="部门角色-批量删除")
|
||||
@RequiresPermissions("system:depart:role:deleteBatch")
|
||||
@SaCheckPermission("system:depart:role:deleteBatch")
|
||||
@DeleteMapping(value = "/deleteBatch")
|
||||
public Result<?> deleteBatch(@RequestParam(name="ids",required=true) String ids) {
|
||||
this.sysDepartRoleService.deleteDepartRole(Arrays.asList(ids.split(",")));
|
||||
@ -194,15 +193,15 @@ public class SysDepartRoleController extends JeecgController<SysDepartRole, ISys
|
||||
* @param json
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:depart:role:userAdd")
|
||||
@SaCheckPermission("system:depart:role:userAdd")
|
||||
@RequestMapping(value = "/deptRoleUserAdd", method = RequestMethod.POST)
|
||||
public Result<?> deptRoleAdd(@RequestBody JSONObject json) {
|
||||
String newRoleId = json.getString("newRoleId");
|
||||
String oldRoleId = json.getString("oldRoleId");
|
||||
String userId = json.getString("userId");
|
||||
departRoleUserService.deptRoleUserAdd(userId,newRoleId,oldRoleId);
|
||||
// 代码逻辑说明: [VUEN-234]部门角色分配添加敏感日志------------
|
||||
LoginUser loginUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
// 代码逻辑说明: [VUEN-234]部门角色分配添加敏感日志
|
||||
LoginUser loginUser = LoginUserUtils.getSessionUser();
|
||||
baseCommonService.addLog("给部门用户ID:"+userId+"分配角色,操作人: " +loginUser.getUsername() ,CommonConstant.LOG_TYPE_2, 2);
|
||||
return Result.ok("添加成功!");
|
||||
}
|
||||
|
||||
@ -10,8 +10,9 @@ import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.commons.lang.StringUtils;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import org.apache.shiro.subject.Subject;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.config.TenantContext;
|
||||
import org.jeecg.common.constant.CacheConstant;
|
||||
@ -23,7 +24,6 @@ import org.jeecg.common.system.vo.DictQuery;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.jeecg.common.util.*;
|
||||
import org.jeecg.config.mybatis.MybatisPlusSaasConfig;
|
||||
import org.jeecg.config.shiro.ShiroRealm;
|
||||
import org.jeecg.modules.system.constant.DefIndexConst;
|
||||
import org.jeecg.modules.system.entity.SysDict;
|
||||
import org.jeecg.modules.system.entity.SysDictItem;
|
||||
@ -75,8 +75,6 @@ public class SysDictController {
|
||||
public RedisTemplate<String, Object> redisTemplate;
|
||||
@Autowired
|
||||
private RedisUtil redisUtil;
|
||||
@Autowired
|
||||
private ShiroRealm shiroRealm;
|
||||
|
||||
@RequestMapping(value = "/list", method = RequestMethod.GET)
|
||||
public Result<IPage<SysDict>> queryPageList(
|
||||
@ -390,7 +388,7 @@ public class SysDictController {
|
||||
* @param sysDict
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:dict:add")
|
||||
@SaCheckPermission("system:dict:add")
|
||||
@RequestMapping(value = "/add", method = RequestMethod.POST)
|
||||
public Result<SysDict> add(@RequestBody SysDict sysDict) {
|
||||
Result<SysDict> result = new Result<SysDict>();
|
||||
@ -411,7 +409,7 @@ public class SysDictController {
|
||||
* @param sysDict
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:dict:edit")
|
||||
@SaCheckPermission("system:dict:edit")
|
||||
@RequestMapping(value = "/edit", method = { RequestMethod.PUT,RequestMethod.POST })
|
||||
public Result<SysDict> edit(@RequestBody SysDict sysDict) {
|
||||
Result<SysDict> result = new Result<SysDict>();
|
||||
@ -433,7 +431,7 @@ public class SysDictController {
|
||||
* @param id
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:dict:delete")
|
||||
@SaCheckPermission("system:dict:delete")
|
||||
@RequestMapping(value = "/delete", method = RequestMethod.DELETE)
|
||||
@CacheEvict(value={CacheConstant.SYS_DICT_CACHE, CacheConstant.SYS_ENABLE_DICT_CACHE}, allEntries=true)
|
||||
public Result<SysDict> delete(@RequestParam(name="id",required=true) String id) {
|
||||
@ -452,7 +450,7 @@ public class SysDictController {
|
||||
* @param ids
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:dict:deleteBatch")
|
||||
@SaCheckPermission("system:dict:deleteBatch")
|
||||
@RequestMapping(value = "/deleteBatch", method = RequestMethod.DELETE)
|
||||
@CacheEvict(value= {CacheConstant.SYS_DICT_CACHE, CacheConstant.SYS_ENABLE_DICT_CACHE}, allEntries=true)
|
||||
public Result<SysDict> deleteBatch(@RequestParam(name="ids",required=true) String ids) {
|
||||
@ -491,7 +489,7 @@ public class SysDictController {
|
||||
// redisTemplate.delete(keys6);
|
||||
// redisTemplate.delete(keys7);
|
||||
|
||||
// 代码逻辑说明: [issue/4358]springCache中的清除缓存的操作使用了“keys”
|
||||
// springCache中的清除缓存的操作使用了“keys”
|
||||
redisUtil.removeAll(CacheConstant.SYS_DICT_CACHE);
|
||||
redisUtil.removeAll(CacheConstant.SYS_ENABLE_DICT_CACHE);
|
||||
redisUtil.removeAll(CacheConstant.SYS_DICT_TABLE_CACHE);
|
||||
@ -500,15 +498,6 @@ public class SysDictController {
|
||||
redisUtil.removeAll(CacheConstant.SYS_DEPART_IDS_CACHE);
|
||||
redisUtil.removeAll("jmreport:cache:dict");
|
||||
redisUtil.removeAll("jmreport:cache:dictTable");
|
||||
|
||||
// 清除当前用户的授权缓存信息
|
||||
Subject currentUser = SecurityUtils.getSubject();
|
||||
if (currentUser.isAuthenticated()) {
|
||||
shiroRealm.clearCache(currentUser.getPrincipals());
|
||||
}
|
||||
|
||||
// 清空默认首页缓存(开源版和商业版会串)
|
||||
redisUtil.del(DefIndexConst.CACHE_KEY + "::" + DefIndexConst.DEF_INDEX_ALL);
|
||||
return result;
|
||||
}
|
||||
|
||||
@ -551,8 +540,8 @@ public class SysDictController {
|
||||
// 注解对象Class
|
||||
mv.addObject(NormalExcelConstants.CLASS, SysDictPage.class);
|
||||
// 自定义表格参数
|
||||
LoginUser user = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
mv.addObject(NormalExcelConstants.PARAMS, new ExportParams("数据字典列表", "导出人:"+user.getRealname(), "数据字典", ExcelType.XSSF));
|
||||
LoginUser user = LoginUserUtils.getSessionUser();
|
||||
mv.addObject(NormalExcelConstants.PARAMS, new ExportParams("数据字典列表", "导出人:"+user.getRealname(), "数据字典"));
|
||||
// 导出数据列表
|
||||
mv.addObject(NormalExcelConstants.DATA_LIST, pageList);
|
||||
return mv;
|
||||
@ -565,7 +554,7 @@ public class SysDictController {
|
||||
* @param
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:dict:importExcel")
|
||||
@SaCheckPermission("system:dict:importExcel")
|
||||
@RequestMapping(value = "/importExcel", method = RequestMethod.POST)
|
||||
public Result<?> importExcel(HttpServletRequest request, HttpServletResponse response) {
|
||||
MultipartHttpServletRequest multipartRequest = (MultipartHttpServletRequest) request;
|
||||
@ -702,7 +691,7 @@ public class SysDictController {
|
||||
* @param ids 被删除的字典ID,多个id用半角逗号分割
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:dict:deleteRecycleBin")
|
||||
@SaCheckPermission("system:dict:deleteRecycleBin")
|
||||
@RequestMapping(value = "/deleteRecycleBin", method = RequestMethod.DELETE)
|
||||
public Result deleteRecycleBin(@RequestParam("ids") String ids) {
|
||||
try {
|
||||
|
||||
@ -10,8 +10,8 @@ import com.baomidou.mybatisplus.core.conditions.query.LambdaQueryWrapper;
|
||||
import io.swagger.v3.oas.annotations.tags.Tag;
|
||||
import io.swagger.v3.oas.annotations.Operation;
|
||||
import org.apache.commons.lang.StringUtils;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import org.apache.shiro.authz.annotation.RequiresRoles;
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
import cn.dev33.satoken.annotation.SaCheckRole;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.constant.CacheConstant;
|
||||
import org.jeecg.common.system.query.QueryGenerator;
|
||||
@ -74,7 +74,7 @@ public class SysDictItemController {
|
||||
* @功能:新增
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:dict:item:add")
|
||||
@SaCheckPermission("system:dict:item:add")
|
||||
@RequestMapping(value = "/add", method = RequestMethod.POST)
|
||||
@CacheEvict(value= {CacheConstant.SYS_DICT_CACHE, CacheConstant.SYS_ENABLE_DICT_CACHE}, allEntries=true)
|
||||
public Result<SysDictItem> add(@RequestBody SysDictItem sysDictItem) {
|
||||
@ -95,7 +95,7 @@ public class SysDictItemController {
|
||||
* @param sysDictItem
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:dict:item:edit")
|
||||
@SaCheckPermission("system:dict:item:edit")
|
||||
@RequestMapping(value = "/edit", method = { RequestMethod.PUT,RequestMethod.POST })
|
||||
@CacheEvict(value={CacheConstant.SYS_DICT_CACHE, CacheConstant.SYS_ENABLE_DICT_CACHE}, allEntries=true)
|
||||
public Result<SysDictItem> edit(@RequestBody SysDictItem sysDictItem) {
|
||||
@ -119,7 +119,7 @@ public class SysDictItemController {
|
||||
* @param id
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:dict:item:delete")
|
||||
@SaCheckPermission("system:dict:item:delete")
|
||||
@RequestMapping(value = "/delete", method = RequestMethod.DELETE)
|
||||
@CacheEvict(value={CacheConstant.SYS_DICT_CACHE, CacheConstant.SYS_ENABLE_DICT_CACHE}, allEntries=true)
|
||||
public Result<SysDictItem> delete(@RequestParam(name="id",required=true) String id) {
|
||||
@ -141,7 +141,7 @@ public class SysDictItemController {
|
||||
* @param ids
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:dict:item:deleteBatch")
|
||||
@SaCheckPermission("system:dict:item:deleteBatch")
|
||||
@RequestMapping(value = "/deleteBatch", method = RequestMethod.DELETE)
|
||||
@CacheEvict(value={CacheConstant.SYS_DICT_CACHE, CacheConstant.SYS_ENABLE_DICT_CACHE}, allEntries=true)
|
||||
public Result<SysDictItem> deleteBatch(@RequestParam(name="ids",required=true) String ids) {
|
||||
|
||||
@ -6,7 +6,7 @@ import com.baomidou.mybatisplus.core.conditions.query.LambdaQueryWrapper;
|
||||
import io.swagger.v3.oas.annotations.tags.Tag;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.commons.lang.StringUtils;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.system.base.controller.JeecgController;
|
||||
import org.jeecg.common.util.oConvertUtils;
|
||||
@ -70,7 +70,7 @@ public class SysGatewayRouteController extends JeecgController<SysGatewayRoute,
|
||||
* @param id
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:getway:delete")
|
||||
@SaCheckPermission("system:getway:delete")
|
||||
@RequestMapping(value = "/delete", method = RequestMethod.DELETE)
|
||||
public Result<?> delete(@RequestParam(name = "id", required = true) String id) {
|
||||
sysGatewayRouteService.deleteById(id);
|
||||
@ -96,7 +96,7 @@ public class SysGatewayRouteController extends JeecgController<SysGatewayRoute,
|
||||
* @param jsonObject
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:gateway:putRecycleBin")
|
||||
@SaCheckPermission("system:gateway:putRecycleBin")
|
||||
@RequestMapping(value = "/putRecycleBin", method = RequestMethod.PUT)
|
||||
public Result putRecycleBin(@RequestBody JSONObject jsonObject, HttpServletRequest request) {
|
||||
try {
|
||||
@ -117,7 +117,7 @@ public class SysGatewayRouteController extends JeecgController<SysGatewayRoute,
|
||||
* @param ids 被删除的路由ID,多个id用半角逗号分割
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:gateway:deleteRecycleBin")
|
||||
@SaCheckPermission("system:gateway:deleteRecycleBin")
|
||||
@RequestMapping(value = "/deleteRecycleBin", method = RequestMethod.DELETE)
|
||||
public Result deleteRecycleBin(@RequestParam("ids") String ids) {
|
||||
try {
|
||||
@ -136,7 +136,7 @@ public class SysGatewayRouteController extends JeecgController<SysGatewayRoute,
|
||||
* @param id 路由id
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:gateway:copyRoute")
|
||||
@SaCheckPermission("system:gateway:copyRoute")
|
||||
@RequestMapping(value = "/copyRoute", method = RequestMethod.GET)
|
||||
public Result<SysGatewayRoute> copyRoute(@RequestParam(name = "id", required = true) String id, HttpServletRequest req) {
|
||||
Result<SysGatewayRoute> result = new Result<>();
|
||||
|
||||
@ -7,8 +7,8 @@ import java.util.List;
|
||||
import jakarta.annotation.Resource;
|
||||
import jakarta.servlet.http.HttpServletRequest;
|
||||
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.system.base.controller.JeecgController;
|
||||
import org.jeecg.common.system.query.QueryGenerator;
|
||||
@ -71,7 +71,7 @@ public class SysLogController extends JeecgController<SysLog, ISysLogService> {
|
||||
* @return
|
||||
*/
|
||||
@RequestMapping(value = "/list", method = RequestMethod.GET)
|
||||
//@RequiresPermissions("system:log:list")
|
||||
//@SaCheckPermission("system:log:list")
|
||||
public Result<IPage<SysLog>> queryPageList(SysLog syslog,@RequestParam(name="pageNo", defaultValue="1") Integer pageNo,
|
||||
@RequestParam(name="pageSize", defaultValue="10") Integer pageSize,HttpServletRequest req) {
|
||||
Result<IPage<SysLog>> result = new Result<IPage<SysLog>>();
|
||||
@ -102,7 +102,7 @@ public class SysLogController extends JeecgController<SysLog, ISysLogService> {
|
||||
* @return
|
||||
*/
|
||||
@RequestMapping(value = "/delete", method = RequestMethod.DELETE)
|
||||
//@RequiresPermissions("system:log:delete")
|
||||
//@SaCheckPermission("system:log:delete")
|
||||
public Result<SysLog> delete(@RequestParam(name="id",required=true) String id) {
|
||||
Result<SysLog> result = new Result<SysLog>();
|
||||
SysLog sysLog = sysLogService.getById(id);
|
||||
@ -123,7 +123,7 @@ public class SysLogController extends JeecgController<SysLog, ISysLogService> {
|
||||
* @return
|
||||
*/
|
||||
@RequestMapping(value = "/deleteBatch", method = RequestMethod.DELETE)
|
||||
//@RequiresPermissions("system:log:deleteBatch")
|
||||
//@SaCheckPermission("system:log:deleteBatch")
|
||||
public Result<SysRole> deleteBatch(@RequestParam(name="ids",required=true) String ids) {
|
||||
Result<SysRole> result = new Result<SysRole>();
|
||||
if(ids==null || "".equals(ids.trim())) {
|
||||
|
||||
@ -1,14 +1,15 @@
|
||||
package org.jeecg.modules.system.controller;
|
||||
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
import com.alibaba.fastjson.JSONArray;
|
||||
import com.alibaba.fastjson.JSONObject;
|
||||
import com.baomidou.mybatisplus.core.conditions.query.LambdaQueryWrapper;
|
||||
import com.baomidou.mybatisplus.core.conditions.query.QueryWrapper;
|
||||
import com.baomidou.mybatisplus.core.metadata.IPage;
|
||||
import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import org.apache.shiro.subject.Subject;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.constant.SymbolConstant;
|
||||
import org.jeecg.common.exception.JeecgBootException;
|
||||
@ -16,8 +17,8 @@ import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.jeecg.common.util.Md5Util;
|
||||
import org.jeecg.common.util.oConvertUtils;
|
||||
import org.jeecg.config.JeecgBaseConfig;
|
||||
import org.jeecg.config.shiro.ShiroRealm;
|
||||
import org.jeecg.modules.base.service.BaseCommonService;
|
||||
import org.jeecg.modules.jmreport.common.annotation.RequiresPermissions;
|
||||
import org.jeecg.modules.system.constant.DefIndexConst;
|
||||
import org.jeecg.modules.system.entity.*;
|
||||
import org.jeecg.modules.system.model.SysPermissionTree;
|
||||
@ -67,9 +68,6 @@ public class SysPermissionController {
|
||||
|
||||
@Autowired
|
||||
private ISysRoleIndexService sysRoleIndexService;
|
||||
|
||||
@Autowired
|
||||
private ShiroRealm shiroRealm;
|
||||
|
||||
/**
|
||||
* 子菜单
|
||||
@ -81,7 +79,7 @@ public class SysPermissionController {
|
||||
*
|
||||
* @return
|
||||
*/
|
||||
//@RequiresPermissions("system:permission:list")
|
||||
//@SaCheckPermission("system:permission:list")
|
||||
@RequestMapping(value = "/list", method = RequestMethod.GET)
|
||||
public Result<List<SysPermissionTree>> list(SysPermission sysPermission, HttpServletRequest req) {
|
||||
long start = System.currentTimeMillis();
|
||||
@ -242,8 +240,8 @@ public class SysPermissionController {
|
||||
public Result<?> getUserPermissionByToken(HttpServletRequest request) {
|
||||
Result<JSONObject> result = new Result<JSONObject>();
|
||||
try {
|
||||
//直接获取当前用户不适用前端token
|
||||
LoginUser loginUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
//直接获取当前用户
|
||||
LoginUser loginUser = LoginUserUtils.getSessionUser();
|
||||
if (oConvertUtils.isEmpty(loginUser)) {
|
||||
return Result.error("请登录系统!");
|
||||
}
|
||||
@ -351,7 +349,7 @@ public class SysPermissionController {
|
||||
public Result<?> getPermCode() {
|
||||
try {
|
||||
// 直接获取当前用户
|
||||
LoginUser loginUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser loginUser = LoginUserUtils.getSessionUser();
|
||||
if (oConvertUtils.isEmpty(loginUser)) {
|
||||
return Result.error("请登录系统!");
|
||||
}
|
||||
@ -392,7 +390,7 @@ public class SysPermissionController {
|
||||
* @param permission
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:permission:add")
|
||||
@SaCheckPermission("system:permission:add")
|
||||
@RequestMapping(value = "/add", method = RequestMethod.POST)
|
||||
public Result<SysPermission> add(@RequestBody SysPermission permission) {
|
||||
Result<SysPermission> result = new Result<SysPermission>();
|
||||
@ -412,7 +410,7 @@ public class SysPermissionController {
|
||||
* @param permission
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:permission:edit")
|
||||
@SaCheckPermission("system:permission:edit")
|
||||
@RequestMapping(value = "/edit", method = { RequestMethod.PUT, RequestMethod.POST })
|
||||
public Result<SysPermission> edit(@RequestBody SysPermission permission) {
|
||||
Result<SysPermission> result = new Result<>();
|
||||
@ -454,7 +452,7 @@ public class SysPermissionController {
|
||||
* @param id
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:permission:delete")
|
||||
@SaCheckPermission("system:permission:delete")
|
||||
@RequestMapping(value = "/delete", method = RequestMethod.DELETE)
|
||||
public Result<SysPermission> delete(@RequestParam(name = "id", required = true) String id) {
|
||||
Result<SysPermission> result = new Result<>();
|
||||
@ -473,7 +471,7 @@ public class SysPermissionController {
|
||||
* @param ids
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:permission:deleteBatch")
|
||||
@SaCheckPermission("system:permission:deleteBatch")
|
||||
@RequestMapping(value = "/deleteBatch", method = RequestMethod.DELETE)
|
||||
public Result<SysPermission> deleteBatch(@RequestParam(name = "ids", required = true) String ids) {
|
||||
Result<SysPermission> result = new Result<>();
|
||||
@ -581,7 +579,7 @@ public class SysPermissionController {
|
||||
* @return
|
||||
*/
|
||||
@RequestMapping(value = "/saveRolePermission", method = RequestMethod.POST)
|
||||
@RequiresPermissions("system:permission:saveRole")
|
||||
@SaCheckPermission("system:permission:saveRole")
|
||||
public Result<String> saveRolePermission(@RequestBody JSONObject json) {
|
||||
long start = System.currentTimeMillis();
|
||||
Result<String> result = new Result<>();
|
||||
@ -590,24 +588,61 @@ public class SysPermissionController {
|
||||
String permissionIds = json.getString("permissionIds");
|
||||
String lastPermissionIds = json.getString("lastpermissionIds");
|
||||
this.sysRolePermissionService.saveRolePermission(roleId, permissionIds, lastPermissionIds);
|
||||
// 代码逻辑说明: [VUEN-234]用户管理角色授权添加敏感日志------------
|
||||
LoginUser loginUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
// 代码逻辑说明: [VUEN-234]用户管理角色授权添加敏感日志------------
|
||||
LoginUser loginUser = LoginUserUtils.getSessionUser();
|
||||
baseCommonService.addLog("修改角色ID: "+roleId+" 的权限配置,操作人: " +loginUser.getUsername() ,CommonConstant.LOG_TYPE_2, 2);
|
||||
result.success("保存成功!");
|
||||
log.info("======角色授权成功=====耗时:" + (System.currentTimeMillis() - start) + "毫秒");
|
||||
|
||||
// 清除当前用户的授权缓存信息
|
||||
Subject currentUser = SecurityUtils.getSubject();
|
||||
if (currentUser.isAuthenticated()) {
|
||||
shiroRealm.clearCache(currentUser.getPrincipals());
|
||||
}
|
||||
|
||||
} catch (Exception e) {
|
||||
|
||||
// 清除拥有该角色的所有用户的权限和角色缓存
|
||||
clearRolePermissionCache(roleId);
|
||||
} catch (Exception e) {
|
||||
result.error500("授权失败!");
|
||||
log.error(e.getMessage(), e);
|
||||
}
|
||||
return result;
|
||||
}
|
||||
|
||||
/**
|
||||
* 清除拥有指定角色的所有用户的权限和角色缓存
|
||||
* <p>原理:查询拥有该角色的所有用户,调用 StpInterfaceImpl.clearUserCache() 清除缓存</p>
|
||||
*
|
||||
* @param roleId 角色ID
|
||||
*/
|
||||
private void clearRolePermissionCache(String roleId) {
|
||||
log.info("开始清除角色权限缓存 [ roleId={} ]", roleId);
|
||||
List<String> usernameList = new ArrayList<>();
|
||||
|
||||
// 分页查询拥有该角色的用户(避免一次性加载大量数据)
|
||||
int pageNo = 1, pageSize = 100;
|
||||
while (true) {
|
||||
Page<SysUser> page = new Page<>(pageNo, pageSize);
|
||||
IPage<SysUser> userPage = sysUserService.getUserByRoleId(page, roleId, null, null);
|
||||
|
||||
if (userPage.getRecords().isEmpty()) {
|
||||
break;
|
||||
}
|
||||
|
||||
// 收集用户名
|
||||
for (SysUser user : userPage.getRecords()) {
|
||||
usernameList.add(user.getUsername());
|
||||
}
|
||||
|
||||
// 判断是否还有下一页
|
||||
if (pageNo >= userPage.getPages()) {
|
||||
break;
|
||||
}
|
||||
pageNo++;
|
||||
}
|
||||
|
||||
// 批量清除缓存
|
||||
if (!usernameList.isEmpty()) {
|
||||
org.jeecg.config.satoken.StpInterfaceImpl.clearUserCache(usernameList);
|
||||
log.info("角色权限缓存清理完成 [ roleId={}, affectedUsers={} ]", roleId, usernameList.size());
|
||||
} else {
|
||||
log.info("该角色下无用户,无需清除缓存 [ roleId={} ]", roleId);
|
||||
}
|
||||
}
|
||||
|
||||
private void getTreeList(List<SysPermissionTree> treeList, List<SysPermission> metaList, SysPermissionTree temp) {
|
||||
for (SysPermission permission : metaList) {
|
||||
@ -913,7 +948,7 @@ public class SysPermissionController {
|
||||
* @param sysPermissionDataRule
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:permission:addRule")
|
||||
@SaCheckPermission("system:permission:addRule")
|
||||
@RequestMapping(value = "/addPermissionRule", method = RequestMethod.POST)
|
||||
public Result<SysPermissionDataRule> addPermissionRule(@RequestBody SysPermissionDataRule sysPermissionDataRule) {
|
||||
Result<SysPermissionDataRule> result = new Result<SysPermissionDataRule>();
|
||||
@ -928,7 +963,7 @@ public class SysPermissionController {
|
||||
return result;
|
||||
}
|
||||
|
||||
@RequiresPermissions("system:permission:editRule")
|
||||
@SaCheckPermission("system:permission:editRule")
|
||||
@RequestMapping(value = "/editPermissionRule", method = { RequestMethod.PUT, RequestMethod.POST })
|
||||
public Result<SysPermissionDataRule> editPermissionRule(@RequestBody SysPermissionDataRule sysPermissionDataRule) {
|
||||
Result<SysPermissionDataRule> result = new Result<SysPermissionDataRule>();
|
||||
@ -948,7 +983,7 @@ public class SysPermissionController {
|
||||
* @param id
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:permission:deleteRule")
|
||||
@SaCheckPermission("system:permission:deleteRule")
|
||||
@RequestMapping(value = "/deletePermissionRule", method = RequestMethod.DELETE)
|
||||
public Result<SysPermissionDataRule> deletePermissionRule(@RequestParam(name = "id", required = true) String id) {
|
||||
Result<SysPermissionDataRule> result = new Result<SysPermissionDataRule>();
|
||||
@ -1005,7 +1040,7 @@ public class SysPermissionController {
|
||||
* @return
|
||||
*/
|
||||
@RequestMapping(value = "/saveDepartPermission", method = RequestMethod.POST)
|
||||
@RequiresPermissions("system:permission:saveDepart")
|
||||
@SaCheckPermission("system:permission:saveDepart")
|
||||
public Result<String> saveDepartPermission(@RequestBody JSONObject json) {
|
||||
long start = System.currentTimeMillis();
|
||||
Result<String> result = new Result<>();
|
||||
|
||||
@ -8,7 +8,7 @@ import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
import io.swagger.v3.oas.annotations.tags.Tag;
|
||||
import io.swagger.v3.oas.annotations.Operation;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.aspect.annotation.AutoLog;
|
||||
import org.jeecg.common.config.TenantContext;
|
||||
@ -247,7 +247,7 @@ public class SysPositionController {
|
||||
//Step.2 AutoPoi 导出Excel
|
||||
ModelAndView mv = new ModelAndView(new JeecgEntityExcelView());
|
||||
List<SysPosition> pageList = sysPositionService.list(queryWrapper);
|
||||
LoginUser user = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser user = LoginUserUtils.getSessionUser();
|
||||
//导出文件名称
|
||||
mv.addObject(NormalExcelConstants.FILE_NAME, "职务表列表");
|
||||
mv.addObject(NormalExcelConstants.CLASS, SysPosition.class);
|
||||
|
||||
@ -1,10 +1,8 @@
|
||||
package org.jeecg.modules.system.controller;
|
||||
|
||||
|
||||
import java.io.File;
|
||||
import java.io.IOException;
|
||||
import java.util.ArrayList;
|
||||
import java.util.Arrays;
|
||||
import java.util.Date;
|
||||
import java.util.HashMap;
|
||||
import java.util.List;
|
||||
@ -15,9 +13,8 @@ import jakarta.servlet.http.HttpServletResponse;
|
||||
|
||||
import cn.hutool.core.util.RandomUtil;
|
||||
import com.baomidou.mybatisplus.extension.plugins.pagination.PageDTO;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.base.BaseMap;
|
||||
import org.jeecg.common.config.TenantContext;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.constant.SymbolConstant;
|
||||
@ -49,7 +46,7 @@ import org.springframework.web.multipart.MultipartFile;
|
||||
import org.springframework.web.multipart.MultipartHttpServletRequest;
|
||||
import org.springframework.web.servlet.ModelAndView;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import com.alibaba.fastjson.JSONObject;
|
||||
import com.baomidou.mybatisplus.core.conditions.query.LambdaQueryWrapper;
|
||||
import com.baomidou.mybatisplus.core.conditions.query.QueryWrapper;
|
||||
@ -97,7 +94,7 @@ public class SysRoleController {
|
||||
* @param req
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:role:list")
|
||||
@SaCheckPermission("system:role:list")
|
||||
@RequestMapping(value = "/list", method = RequestMethod.GET)
|
||||
public Result<IPage<SysRole>> queryPageList(SysRole role,
|
||||
@RequestParam(name="pageNo", defaultValue="1") Integer pageNo,
|
||||
@ -152,7 +149,7 @@ public class SysRoleController {
|
||||
* @return
|
||||
*/
|
||||
@RequestMapping(value = "/add", method = RequestMethod.POST)
|
||||
@RequiresPermissions("system:role:add")
|
||||
@SaCheckPermission("system:role:add")
|
||||
public Result<SysRole> add(@RequestBody SysRole role) {
|
||||
Result<SysRole> result = new Result<SysRole>();
|
||||
try {
|
||||
@ -176,7 +173,7 @@ public class SysRoleController {
|
||||
* @param role
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:role:edit")
|
||||
@SaCheckPermission("system:role:edit")
|
||||
@RequestMapping(value = "/edit",method = {RequestMethod.PUT,RequestMethod.POST})
|
||||
public Result<SysRole> edit(@RequestBody SysRole role) {
|
||||
Result<SysRole> result = new Result<SysRole>();
|
||||
@ -190,7 +187,7 @@ public class SysRoleController {
|
||||
//如果是saas隔离的情况下,判断当前租户id是否是当前租户下的
|
||||
if (MybatisPlusSaasConfig.OPEN_SYSTEM_TENANT_CONTROL) {
|
||||
//获取当前用户
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
Integer tenantId = oConvertUtils.getInt(TenantContext.getTenant(), 0);
|
||||
String username = "admin";
|
||||
if (!tenantId.equals(sysrole.getTenantId()) && !username.equals(sysUser.getUsername())) {
|
||||
@ -213,13 +210,13 @@ public class SysRoleController {
|
||||
* @param id
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:role:delete")
|
||||
@SaCheckPermission("system:role:delete")
|
||||
@RequestMapping(value = "/delete", method = RequestMethod.DELETE)
|
||||
public Result<?> delete(@RequestParam(name="id",required=true) String id) {
|
||||
//如果是saas隔离的情况下,判断当前租户id是否是当前租户下的
|
||||
if(MybatisPlusSaasConfig.OPEN_SYSTEM_TENANT_CONTROL){
|
||||
//获取当前用户
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
int tenantId = oConvertUtils.getInt(TenantContext.getTenant(), 0);
|
||||
Long getRoleCount = sysRoleService.getRoleCountByTenantId(id, tenantId);
|
||||
String username = "admin";
|
||||
@ -242,7 +239,7 @@ public class SysRoleController {
|
||||
* @param ids
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:role:deleteBatch")
|
||||
@SaCheckPermission("system:role:deleteBatch")
|
||||
@RequestMapping(value = "/deleteBatch", method = RequestMethod.DELETE)
|
||||
public Result<SysRole> deleteBatch(@RequestParam(name="ids",required=true) String ids) {
|
||||
baseCommonService.addLog("删除角色操作,角色ids:" + ids, CommonConstant.LOG_TYPE_2, CommonConstant.OPERATE_TYPE_4);
|
||||
@ -254,7 +251,7 @@ public class SysRoleController {
|
||||
if(MybatisPlusSaasConfig.OPEN_SYSTEM_TENANT_CONTROL){
|
||||
int tenantId = oConvertUtils.getInt(TenantContext.getTenant(), 0);
|
||||
String[] roleIds = ids.split(SymbolConstant.COMMA);
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
String username = "admin";
|
||||
for (String id:roleIds) {
|
||||
Long getRoleCount = sysRoleService.getRoleCountByTenantId(id, tenantId);
|
||||
@ -321,7 +318,7 @@ public class SysRoleController {
|
||||
*
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:role:queryallNoByTenant")
|
||||
@SaCheckPermission("system:role:queryallNoByTenant")
|
||||
@RequestMapping(value = "/queryallNoByTenant", method = RequestMethod.GET)
|
||||
public Result<List<SysRole>> queryallNoByTenant() {
|
||||
Result<List<SysRole>> result = new Result<>();
|
||||
@ -397,7 +394,7 @@ public class SysRoleController {
|
||||
//导出文件名称
|
||||
mv.addObject(NormalExcelConstants.FILE_NAME,"角色列表");
|
||||
mv.addObject(NormalExcelConstants.CLASS,SysRole.class);
|
||||
LoginUser user = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser user = LoginUserUtils.getSessionUser();
|
||||
//导出支持xlsx
|
||||
mv.addObject(NormalExcelConstants.PARAMS,new ExportParams("角色列表数据","导出人:"+user.getRealname(),"导出信息", ExcelType.XSSF));
|
||||
mv.addObject(NormalExcelConstants.DATA_LIST,pageList);
|
||||
|
||||
@ -9,7 +9,7 @@ import io.swagger.v3.oas.annotations.Operation;
|
||||
import jakarta.servlet.http.HttpServletRequest;
|
||||
import jakarta.servlet.http.HttpServletResponse;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.aspect.annotation.AutoLog;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
@ -80,7 +80,7 @@ public class SysRoleIndexController extends JeecgController<SysRoleIndex, ISysRo
|
||||
* @param sysRoleIndex
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:roleindex:add")
|
||||
@SaCheckPermission("system:roleindex:add")
|
||||
@AutoLog(value = "角色首页配置-添加")
|
||||
@Operation(summary = "角色首页配置-添加")
|
||||
@PostMapping(value = "/add")
|
||||
@ -103,7 +103,7 @@ public class SysRoleIndexController extends JeecgController<SysRoleIndex, ISysRo
|
||||
* @param sysRoleIndex
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:roleindex:edit")
|
||||
@SaCheckPermission("system:roleindex:edit")
|
||||
@AutoLog(value = "角色首页配置-编辑")
|
||||
@Operation(summary = "角色首页配置-编辑")
|
||||
@RequestMapping(value = "/edit", method = {RequestMethod.PUT, RequestMethod.POST})
|
||||
@ -128,7 +128,7 @@ public class SysRoleIndexController extends JeecgController<SysRoleIndex, ISysRo
|
||||
*/
|
||||
@AutoLog(value = "角色首页配置-通过id删除")
|
||||
@Operation(summary = "角色首页配置-通过id删除")
|
||||
@RequiresPermissions("system:roleindex:delete")
|
||||
@SaCheckPermission("system:roleindex:delete")
|
||||
@DeleteMapping(value = "/delete")
|
||||
public Result<?> delete(@RequestParam(name = "id", required = true) String id) {
|
||||
sysRoleIndexService.removeById(id);
|
||||
@ -143,7 +143,7 @@ public class SysRoleIndexController extends JeecgController<SysRoleIndex, ISysRo
|
||||
*/
|
||||
@AutoLog(value = "角色首页配置-批量删除")
|
||||
@Operation(summary = "角色首页配置-批量删除")
|
||||
@RequiresPermissions("system:roleindex:deleteBatch")
|
||||
@SaCheckPermission("system:roleindex:deleteBatch")
|
||||
@DeleteMapping(value = "/deleteBatch")
|
||||
public Result<?> deleteBatch(@RequestParam(name = "ids", required = true) String ids) {
|
||||
baseCommonService.addLog("批量删除用户, ids: " +ids ,CommonConstant.LOG_TYPE_2, 3);
|
||||
@ -215,7 +215,7 @@ public class SysRoleIndexController extends JeecgController<SysRoleIndex, ISysRo
|
||||
/**
|
||||
* 更新默认首页配置
|
||||
*/
|
||||
@RequiresPermissions("system:permission:setDefIndex")
|
||||
@SaCheckPermission("system:permission:setDefIndex")
|
||||
@PutMapping("/updateDefIndex")
|
||||
public Result<?> updateDefIndex(
|
||||
@RequestParam("url") String url,
|
||||
|
||||
@ -6,8 +6,8 @@ import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
import io.swagger.v3.oas.annotations.tags.Tag;
|
||||
import io.swagger.v3.oas.annotations.Operation;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import org.apache.shiro.authz.annotation.RequiresRoles;
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
import cn.dev33.satoken.annotation.SaCheckRole;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.aspect.annotation.AutoLog;
|
||||
import org.jeecg.common.system.base.controller.JeecgController;
|
||||
@ -43,8 +43,8 @@ public class SysTableWhiteListController extends JeecgController<SysTableWhiteLi
|
||||
* @param req
|
||||
* @return
|
||||
*/
|
||||
//@RequiresRoles("admin")
|
||||
@RequiresPermissions("system:tableWhite:list")
|
||||
//@SaCheckRole("admin")
|
||||
@SaCheckPermission("system:tableWhite:list")
|
||||
@GetMapping(value = "/list")
|
||||
public Result<?> queryPageList(
|
||||
SysTableWhiteList sysTableWhiteList,
|
||||
@ -66,8 +66,8 @@ public class SysTableWhiteListController extends JeecgController<SysTableWhiteLi
|
||||
*/
|
||||
@AutoLog(value = "系统表白名单-添加")
|
||||
@Operation(summary = "系统表白名单-添加")
|
||||
//@RequiresRoles("admin")
|
||||
@RequiresPermissions("system:tableWhite:add")
|
||||
//@SaCheckRole("admin")
|
||||
@SaCheckPermission("system:tableWhite:add")
|
||||
@PostMapping(value = "/add")
|
||||
public Result<?> add(@RequestBody SysTableWhiteList sysTableWhiteList) {
|
||||
if (sysTableWhiteListService.add(sysTableWhiteList)) {
|
||||
@ -85,8 +85,8 @@ public class SysTableWhiteListController extends JeecgController<SysTableWhiteLi
|
||||
*/
|
||||
@AutoLog(value = "系统表白名单-编辑")
|
||||
@Operation(summary = "系统表白名单-编辑")
|
||||
//@RequiresRoles("admin")
|
||||
@RequiresPermissions("system:tableWhite:edit")
|
||||
//@SaCheckRole("admin")
|
||||
@SaCheckPermission("system:tableWhite:edit")
|
||||
@RequestMapping(value = "/edit", method = {RequestMethod.PUT, RequestMethod.POST})
|
||||
public Result<?> edit(@RequestBody SysTableWhiteList sysTableWhiteList) {
|
||||
if (sysTableWhiteListService.edit(sysTableWhiteList)) {
|
||||
@ -104,8 +104,8 @@ public class SysTableWhiteListController extends JeecgController<SysTableWhiteLi
|
||||
*/
|
||||
@AutoLog(value = "系统表白名单-通过id删除")
|
||||
@Operation(summary = "系统表白名单-通过id删除")
|
||||
// @RequiresRoles("admin")
|
||||
@RequiresPermissions("system:tableWhite:delete")
|
||||
// @SaCheckRole("admin")
|
||||
@SaCheckPermission("system:tableWhite:delete")
|
||||
@DeleteMapping(value = "/delete")
|
||||
public Result<?> delete(@RequestParam(name = "id") String id) {
|
||||
if (sysTableWhiteListService.deleteByIds(id)) {
|
||||
@ -123,8 +123,8 @@ public class SysTableWhiteListController extends JeecgController<SysTableWhiteLi
|
||||
*/
|
||||
@AutoLog(value = "系统表白名单-批量删除")
|
||||
@Operation(summary = "系统表白名单-批量删除")
|
||||
// @RequiresRoles("admin")
|
||||
@RequiresPermissions("system:tableWhite:deleteBatch")
|
||||
// @SaCheckRole("admin")
|
||||
@SaCheckPermission("system:tableWhite:deleteBatch")
|
||||
@DeleteMapping(value = "/deleteBatch")
|
||||
public Result<?> deleteBatch(@RequestParam(name = "ids") String ids) {
|
||||
if (sysTableWhiteListService.deleteByIds(ids)) {
|
||||
@ -142,8 +142,8 @@ public class SysTableWhiteListController extends JeecgController<SysTableWhiteLi
|
||||
*/
|
||||
@AutoLog(value = "系统表白名单-通过id查询")
|
||||
@Operation(summary = "系统表白名单-通过id查询")
|
||||
// @RequiresRoles("admin")
|
||||
@RequiresPermissions("system:tableWhite:queryById")
|
||||
// @SaCheckRole("admin")
|
||||
@SaCheckPermission("system:tableWhite:queryById")
|
||||
@GetMapping(value = "/queryById")
|
||||
public Result<?> queryById(@RequestParam(name = "id", required = true) String id) {
|
||||
SysTableWhiteList sysTableWhiteList = sysTableWhiteListService.getById(id);
|
||||
|
||||
@ -9,7 +9,8 @@ import com.baomidou.mybatisplus.core.metadata.IPage;
|
||||
import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.aspect.annotation.PermissionData;
|
||||
import org.jeecg.common.config.TenantContext;
|
||||
@ -74,7 +75,7 @@ public class SysTenantController {
|
||||
* @param req
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:tenant:list")
|
||||
@SaCheckPermission("system:tenant:list")
|
||||
@PermissionData(pageComponent = "system/TenantList")
|
||||
@RequestMapping(value = "/list", method = RequestMethod.GET)
|
||||
public Result<IPage<SysTenant>> queryPageList(SysTenant sysTenant,@RequestParam(name="pageNo", defaultValue="1") Integer pageNo,
|
||||
@ -113,7 +114,7 @@ public class SysTenantController {
|
||||
* @return
|
||||
*/
|
||||
@GetMapping("/recycleBinPageList")
|
||||
@RequiresPermissions("system:tenant:recycleBinPageList")
|
||||
@SaCheckPermission("system:tenant:recycleBinPageList")
|
||||
public Result<IPage<SysTenant>> recycleBinPageList(SysTenant sysTenant,@RequestParam(name="pageNo", defaultValue="1") Integer pageNo,
|
||||
@RequestParam(name="pageSize", defaultValue="10") Integer pageSize,HttpServletRequest req){
|
||||
Result<IPage<SysTenant>> result = new Result<IPage<SysTenant>>();
|
||||
@ -129,7 +130,7 @@ public class SysTenantController {
|
||||
* @param
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:tenant:add")
|
||||
@SaCheckPermission("system:tenant:add")
|
||||
@RequestMapping(value = "/add", method = RequestMethod.POST)
|
||||
public Result<SysTenant> add(@RequestBody SysTenant sysTenant) {
|
||||
Result<SysTenant> result = new Result();
|
||||
@ -155,7 +156,7 @@ public class SysTenantController {
|
||||
* @author chenrui
|
||||
* @date 2025/2/6 18:24
|
||||
*/
|
||||
@RequiresPermissions("system:tenant:syncDefaultPack")
|
||||
@SaCheckPermission("system:tenant:syncDefaultPack")
|
||||
@PostMapping(value = "/syncDefaultPack")
|
||||
public Result<?> syncDefaultPack(@RequestParam(name="tenantId",required=true) Integer tenantId) {
|
||||
//同步默认产品包
|
||||
@ -168,7 +169,7 @@ public class SysTenantController {
|
||||
* @param
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:tenant:edit")
|
||||
@SaCheckPermission("system:tenant:edit")
|
||||
@RequestMapping(value = "/edit", method ={RequestMethod.PUT, RequestMethod.POST})
|
||||
public Result<SysTenant> edit(@RequestBody SysTenant tenant) {
|
||||
Result<SysTenant> result = new Result();
|
||||
@ -191,14 +192,14 @@ public class SysTenantController {
|
||||
* @param id
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:tenant:delete")
|
||||
@SaCheckPermission("system:tenant:delete")
|
||||
@RequestMapping(value = "/delete", method ={RequestMethod.DELETE, RequestMethod.POST})
|
||||
public Result<?> delete(@RequestParam(name="id",required=true) String id) {
|
||||
//------------------------------------------------------------------
|
||||
//如果是saas隔离的情况下,判断当前租户id是否是当前租户下的
|
||||
if (MybatisPlusSaasConfig.OPEN_SYSTEM_TENANT_CONTROL) {
|
||||
//获取当前用户
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
SysTenant sysTenant = sysTenantService.getById(id);
|
||||
|
||||
String username = "admin";
|
||||
@ -219,7 +220,7 @@ public class SysTenantController {
|
||||
* @param ids
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:tenant:deleteBatch")
|
||||
@SaCheckPermission("system:tenant:deleteBatch")
|
||||
@RequestMapping(value = "/deleteBatch", method = RequestMethod.DELETE)
|
||||
public Result<?> deleteBatch(@RequestParam(name="ids",required=true) String ids) {
|
||||
Result<?> result = new Result<>();
|
||||
@ -234,7 +235,7 @@ public class SysTenantController {
|
||||
//如果是saas隔离的情况下,判断当前租户id是否是当前租户下的
|
||||
if (MybatisPlusSaasConfig.OPEN_SYSTEM_TENANT_CONTROL) {
|
||||
//获取当前用户
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
SysTenant sysTenant = sysTenantService.getById(id);
|
||||
|
||||
String username = "admin";
|
||||
@ -268,7 +269,7 @@ public class SysTenantController {
|
||||
}
|
||||
//------------------------------------------------------------------------------------------------
|
||||
//获取登录用户信息
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
//是否开启系统管理模块的多租户数据隔离【SAAS多租户模式】, admin给特权可以管理所有租户
|
||||
if(MybatisPlusSaasConfig.OPEN_SYSTEM_TENANT_CONTROL && !"admin".equals(sysUser.getUsername())){
|
||||
Integer loginSessionTenant = oConvertUtils.getInt(TenantContext.getTenant());
|
||||
@ -293,7 +294,7 @@ public class SysTenantController {
|
||||
* 查询有效的 租户数据
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:tenant:queryList")
|
||||
@SaCheckPermission("system:tenant:queryList")
|
||||
@RequestMapping(value = "/queryList", method = RequestMethod.GET)
|
||||
public Result<List<SysTenant>> queryList(@RequestParam(name="ids",required=false) String ids) {
|
||||
Result<List<SysTenant>> result = new Result<List<SysTenant>>();
|
||||
@ -319,7 +320,7 @@ public class SysTenantController {
|
||||
* @return
|
||||
*/
|
||||
@GetMapping(value = "/packList")
|
||||
@RequiresPermissions("system:tenant:packList")
|
||||
@SaCheckPermission("system:tenant:packList")
|
||||
public Result<IPage<SysTenantPack>> queryPackPageList(SysTenantPack sysTenantPack,
|
||||
@RequestParam(name = "pageNo", defaultValue = "1") Integer pageNo,
|
||||
@RequestParam(name = "pageSize", defaultValue = "10") Integer pageSize,
|
||||
@ -341,7 +342,7 @@ public class SysTenantController {
|
||||
* @return
|
||||
*/
|
||||
@PostMapping(value = "/addPackPermission")
|
||||
@RequiresPermissions("system:tenant:add:pack")
|
||||
@SaCheckPermission("system:tenant:add:pack")
|
||||
public Result<String> addPackPermission(@RequestBody SysTenantPack sysTenantPack) {
|
||||
sysTenantPackService.addPackPermission(sysTenantPack);
|
||||
return Result.ok("创建租户产品包成功");
|
||||
@ -354,7 +355,7 @@ public class SysTenantController {
|
||||
* @return
|
||||
*/
|
||||
@PutMapping(value = "/editPackPermission")
|
||||
@RequiresPermissions("system:tenant:edit:pack")
|
||||
@SaCheckPermission("system:tenant:edit:pack")
|
||||
public Result<String> editPackPermission(@RequestBody SysTenantPack sysTenantPack) {
|
||||
sysTenantPackService.editPackPermission(sysTenantPack);
|
||||
return Result.ok("修改租户产品包成功");
|
||||
@ -367,7 +368,7 @@ public class SysTenantController {
|
||||
* @return
|
||||
*/
|
||||
@DeleteMapping("/deleteTenantPack")
|
||||
@RequiresPermissions("system:tenant:delete:pack")
|
||||
@SaCheckPermission("system:tenant:delete:pack")
|
||||
public Result<String> deleteTenantPack(@RequestParam(value = "ids") String ids) {
|
||||
sysTenantPackService.deleteTenantPack(ids);
|
||||
return Result.ok("删除租户产品包成功");
|
||||
@ -409,7 +410,7 @@ public class SysTenantController {
|
||||
* @return
|
||||
*/
|
||||
@PutMapping("/invitationUserJoin")
|
||||
@RequiresPermissions("system:tenant:invitation:user")
|
||||
@SaCheckPermission("system:tenant:invitation:user")
|
||||
public Result<String> invitationUserJoin(@RequestParam("ids") String ids,@RequestParam(value = "phone", required = false) String phone, @RequestParam(value = "username", required = false) String username){
|
||||
if(oConvertUtils.isEmpty(phone) && oConvertUtils.isEmpty(username)){
|
||||
return Result.error("手机号和用户账号不能同时为空!");
|
||||
@ -427,7 +428,7 @@ public class SysTenantController {
|
||||
* @return
|
||||
*/
|
||||
@RequestMapping(value = "/getTenantUserList", method = RequestMethod.GET)
|
||||
@RequiresPermissions("system:tenant:user:list")
|
||||
@SaCheckPermission("system:tenant:user:list")
|
||||
public Result<IPage<SysUser>> getTenantUserList(SysUser user,
|
||||
@RequestParam(name="pageNo", defaultValue="1") Integer pageNo,
|
||||
@RequestParam(name="pageSize", defaultValue="10") Integer pageSize,
|
||||
@ -448,12 +449,12 @@ public class SysTenantController {
|
||||
* @return
|
||||
*/
|
||||
@PutMapping("/leaveTenant")
|
||||
@RequiresPermissions("system:tenant:leave")
|
||||
@SaCheckPermission("system:tenant:leave")
|
||||
public Result<String> leaveTenant(@RequestParam("userIds") String userIds,
|
||||
@RequestParam("tenantId") String tenantId){
|
||||
Result<String> result = new Result<>();
|
||||
//是否开启系统管理模块的多租户数据隔离【SAAS多租户模式】
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
if(MybatisPlusSaasConfig.OPEN_SYSTEM_TENANT_CONTROL && !"admin".equals(sysUser.getUsername())){
|
||||
Integer loginSessionTenant = oConvertUtils.getInt(TenantContext.getTenant());
|
||||
if(loginSessionTenant!=null && !loginSessionTenant.equals(Integer.valueOf(tenantId))){
|
||||
@ -499,7 +500,7 @@ public class SysTenantController {
|
||||
@PostMapping("/saveTenantJoinUser")
|
||||
public Result<Integer> saveTenantJoinUser(@RequestBody SysTenant sysTenant){
|
||||
Result<Integer> result = new Result<>();
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
Integer tenantId = sysTenantService.saveTenantJoinUser(sysTenant, sysUser.getId());
|
||||
result.setSuccess(true);
|
||||
result.setMessage("创建成功");
|
||||
@ -513,7 +514,7 @@ public class SysTenantController {
|
||||
*/
|
||||
@PostMapping("/joinTenantByHouseNumber")
|
||||
public Result<Integer> joinTenantByHouseNumber(@RequestBody SysTenant sysTenant){
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
Integer tenantId = sysTenantService.joinTenantByHouseNumber(sysTenant, sysUser.getId());
|
||||
Result<Integer> result = new Result<>();
|
||||
if(tenantId != 0){
|
||||
@ -539,7 +540,7 @@ public class SysTenantController {
|
||||
* @return
|
||||
*/
|
||||
@GetMapping("/getUserTenantPageList")
|
||||
//@RequiresPermissions("system:tenant:tenantPageList")
|
||||
//@SaCheckPermission("system:tenant:tenantPageList")
|
||||
public Result<IPage<SysUserTenantVo>> getUserTenantPageList(@RequestParam(name = "pageNo", defaultValue = "1") Integer pageNo,
|
||||
@RequestParam(name = "pageSize", defaultValue = "10") Integer pageSize,
|
||||
@RequestParam(name = "userTenantStatus") String userTenantStatus,
|
||||
@ -547,7 +548,7 @@ public class SysTenantController {
|
||||
SysUser user,
|
||||
HttpServletRequest req) {
|
||||
Page<SysUserTenantVo> page = new Page<SysUserTenantVo>(pageNo, pageSize);
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
String tenantId = oConvertUtils.getString(TenantContext.getTenant(), "0");
|
||||
IPage<SysUserTenantVo> list = relationService.getUserTenantPageList(page, Arrays.asList(userTenantStatus.split(SymbolConstant.COMMA)), user, Integer.valueOf(tenantId));
|
||||
return Result.ok(list);
|
||||
@ -560,9 +561,9 @@ public class SysTenantController {
|
||||
* @return
|
||||
*/
|
||||
@GetMapping("/getTenantListByUserId")
|
||||
//@RequiresPermissions("system:tenant:getTenantListByUserId")
|
||||
//@SaCheckPermission("system:tenant:getTenantListByUserId")
|
||||
public Result<List<SysUserTenantVo>> getTenantListByUserId(@RequestParam(name = "userTenantStatus", required = false) String userTenantStatus) {
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
List<String> list = null;
|
||||
if (oConvertUtils.isNotEmpty(userTenantStatus)) {
|
||||
list = Arrays.asList(userTenantStatus.split(SymbolConstant.COMMA));
|
||||
@ -576,7 +577,7 @@ public class SysTenantController {
|
||||
* 更新用户租户关系状态【低代码应用专用接口】
|
||||
*/
|
||||
@PutMapping("/updateUserTenantStatus")
|
||||
//@RequiresPermissions("system:tenant:updateUserTenantStatus")
|
||||
//@SaCheckPermission("system:tenant:updateUserTenantStatus")
|
||||
public Result<String> updateUserTenantStatus(@RequestBody SysUserTenant userTenant) {
|
||||
String tenantId = TenantContext.getTenant();
|
||||
if (oConvertUtils.isEmpty(tenantId)) {
|
||||
@ -593,9 +594,9 @@ public class SysTenantController {
|
||||
* @return
|
||||
*/
|
||||
@PutMapping("/cancelTenant")
|
||||
//@RequiresPermissions("system:tenant:cancelTenant")
|
||||
//@SaCheckPermission("system:tenant:cancelTenant")
|
||||
public Result<String> cancelTenant(@RequestBody SysTenant sysTenant,HttpServletRequest request) {
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
SysTenant tenant = sysTenantService.getById(sysTenant.getId());
|
||||
if (null == tenant) {
|
||||
return Result.error("未找到当前租户信息");
|
||||
@ -637,7 +638,7 @@ public class SysTenantController {
|
||||
*/
|
||||
@PutMapping("/cancelApplyTenant")
|
||||
public Result<String> cancelApplyTenant(@RequestParam("tenantId") String tenantId){
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
sysTenantService.leaveTenant(sysUser.getId(),tenantId);
|
||||
return Result.ok("取消申请成功");
|
||||
}
|
||||
@ -650,7 +651,7 @@ public class SysTenantController {
|
||||
* @return
|
||||
*/
|
||||
@DeleteMapping("/deleteLogicDeleted")
|
||||
@RequiresPermissions("system:tenant:deleteTenantLogic")
|
||||
@SaCheckPermission("system:tenant:deleteTenantLogic")
|
||||
public Result<String> deleteTenantLogic(@RequestParam("ids") String ids){
|
||||
sysTenantService.deleteTenantLogic(ids);
|
||||
return Result.ok("彻底删除成功");
|
||||
@ -662,7 +663,7 @@ public class SysTenantController {
|
||||
* @return
|
||||
*/
|
||||
@PutMapping("/revertTenantLogic")
|
||||
@RequiresPermissions("system:tenant:revertTenantLogic")
|
||||
@SaCheckPermission("system:tenant:revertTenantLogic")
|
||||
public Result<String> revertTenantLogic(@RequestParam("ids") String ids){
|
||||
sysTenantService.revertTenantLogic(ids);
|
||||
return Result.ok("还原成功");
|
||||
@ -676,7 +677,7 @@ public class SysTenantController {
|
||||
*/
|
||||
@DeleteMapping("/exitUserTenant")
|
||||
public Result<String> exitUserTenant(@RequestBody SysTenant sysTenant,HttpServletRequest request){
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
//验证用户是否已存在
|
||||
Integer count = relationService.userTenantIzExist(sysUser.getId(),sysTenant.getId());
|
||||
if (count == 0) {
|
||||
@ -900,7 +901,7 @@ public class SysTenantController {
|
||||
public Result<IPage<SysTenant>> getTenantPageListByUserId(SysUserTenantVo sysUserTenantVo,
|
||||
@RequestParam(name="pageNo", defaultValue="1") Integer pageNo,
|
||||
@RequestParam(name="pageSize", defaultValue="10") Integer pageSize) {
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
List<String> list = null;
|
||||
String userTenantStatus = sysUserTenantVo.getUserTenantStatus();
|
||||
if (oConvertUtils.isNotEmpty(userTenantStatus)) {
|
||||
@ -918,7 +919,7 @@ public class SysTenantController {
|
||||
public Result<String> agreeOrRefuseJoinTenant(@RequestParam("tenantId") Integer tenantId,
|
||||
@RequestParam("status") String status){
|
||||
//是否开启系统管理模块的多租户数据隔离【SAAS多租户模式】
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
String userId = sysUser.getId();
|
||||
SysTenant tenant = sysTenantService.getById(tenantId);
|
||||
if(null == tenant){
|
||||
@ -969,7 +970,7 @@ public class SysTenantController {
|
||||
public Result<Map<String,Object>> getCurrentUserTenantForFile() {
|
||||
Result<Map<String,Object>> result = new Result<Map<String,Object>>();
|
||||
try {
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
List<SysTenant> tenantList = sysTenantService.getTenantListByUserId(sysUser.getId());
|
||||
Map<String,Object> map = new HashMap<>(5);
|
||||
//在开启saas租户隔离的时候并且租户数据不为空,则返回租户信息
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
package org.jeecg.modules.system.controller;
|
||||
|
||||
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
import cn.dev33.satoken.annotation.SaCheckRole;
|
||||
import cn.hutool.core.util.RandomUtil;
|
||||
import com.alibaba.fastjson.JSON;
|
||||
import com.alibaba.fastjson.JSONArray;
|
||||
@ -12,8 +14,6 @@ import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.commons.lang.StringUtils;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import org.apache.shiro.authz.annotation.RequiresRoles;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.aspect.annotation.PermissionData;
|
||||
import org.jeecg.common.base.BaseMap;
|
||||
@ -30,6 +30,7 @@ import org.jeecg.common.util.*;
|
||||
import org.jeecg.config.JeecgBaseConfig;
|
||||
import org.jeecg.config.mybatis.MybatisPlusSaasConfig;
|
||||
import org.jeecg.modules.base.service.BaseCommonService;
|
||||
import org.jeecg.modules.jmreport.common.annotation.RequiresRoles;
|
||||
import org.jeecg.modules.system.entity.*;
|
||||
import org.jeecg.modules.system.excelstyle.ExcelExportSysUserStyle;
|
||||
import org.jeecg.modules.system.model.DepartIdModel;
|
||||
@ -147,7 +148,7 @@ public class SysUserController {
|
||||
* @param req
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:user:listAll")
|
||||
@SaCheckPermission("system:user:listAll")
|
||||
@RequestMapping(value = "/listAll", method = RequestMethod.GET)
|
||||
public Result<IPage<SysUser>> queryAllPageList(SysUser user, @RequestParam(name = "pageNo", defaultValue = "1") Integer pageNo,
|
||||
@RequestParam(name = "pageSize", defaultValue = "10") Integer pageSize, HttpServletRequest req) {
|
||||
@ -155,7 +156,7 @@ public class SysUserController {
|
||||
return sysUserService.queryPageList(req, queryWrapper, pageSize, pageNo);
|
||||
}
|
||||
|
||||
@RequiresPermissions("system:user:add")
|
||||
@SaCheckPermission("system:user:add")
|
||||
@RequestMapping(value = "/add", method = RequestMethod.POST)
|
||||
public Result<SysUser> add(@RequestBody JSONObject jsonObject) {
|
||||
Result<SysUser> result = new Result<SysUser>();
|
||||
@ -186,7 +187,7 @@ public class SysUserController {
|
||||
return result;
|
||||
}
|
||||
|
||||
@RequiresPermissions("system:user:edit")
|
||||
@SaCheckPermission("system:user:edit")
|
||||
@RequestMapping(value = "/edit", method = {RequestMethod.PUT,RequestMethod.POST})
|
||||
public Result<SysUser> edit(@RequestBody JSONObject jsonObject) {
|
||||
Result<SysUser> result = new Result<SysUser>();
|
||||
@ -231,7 +232,7 @@ public class SysUserController {
|
||||
* @param jsonObject
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:user:addTenantUser")
|
||||
@SaCheckPermission("system:user:addTenantUser")
|
||||
@RequestMapping(value = "/addTenantUser", method = RequestMethod.POST)
|
||||
public Result<SysUser> addTenantUser(@RequestBody JSONObject jsonObject) {
|
||||
Result<SysUser> result = new Result<SysUser>();
|
||||
@ -264,7 +265,7 @@ public class SysUserController {
|
||||
/**
|
||||
* 删除用户
|
||||
*/
|
||||
@RequiresPermissions("system:user:delete")
|
||||
@SaCheckPermission("system:user:delete")
|
||||
@RequestMapping(value = "/delete", method = RequestMethod.DELETE)
|
||||
public Result<?> delete(@RequestParam(name="id",required=true) String id) {
|
||||
baseCommonService.addLog("删除用户,id: " +id ,CommonConstant.LOG_TYPE_2, 3);
|
||||
@ -280,7 +281,7 @@ public class SysUserController {
|
||||
/**
|
||||
* 批量删除用户
|
||||
*/
|
||||
@RequiresPermissions("system:user:deleteBatch")
|
||||
@SaCheckPermission("system:user:deleteBatch")
|
||||
@RequestMapping(value = "/deleteBatch", method = RequestMethod.DELETE)
|
||||
public Result<?> deleteBatch(@RequestParam(name="ids",required=true) String ids) {
|
||||
baseCommonService.addLog("批量删除用户, ids: " +ids ,CommonConstant.LOG_TYPE_2, 3);
|
||||
@ -299,7 +300,7 @@ public class SysUserController {
|
||||
* @param jsonObject
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:user:frozenBatch")
|
||||
@SaCheckPermission("system:user:frozenBatch")
|
||||
@RequestMapping(value = "/frozenBatch", method = RequestMethod.PUT)
|
||||
public Result<SysUser> frozenBatch(@RequestBody JSONObject jsonObject) {
|
||||
Result<SysUser> result = new Result<SysUser>();
|
||||
@ -327,8 +328,8 @@ public class SysUserController {
|
||||
* @param usernames
|
||||
* @return
|
||||
*/
|
||||
@RequiresRoles({"admin"})
|
||||
@RequiresPermissions("system:user:resetPassword")
|
||||
@SaCheckRole({"admin"})
|
||||
@SaCheckPermission("system:user:resetPassword")
|
||||
@RequestMapping(value = "/resetPassword", method = RequestMethod.PUT)
|
||||
public Result<SysUser> resetPassword(@RequestParam(name = "usernames") String usernames) {
|
||||
Result<SysUser> result = new Result<SysUser>();
|
||||
@ -343,7 +344,7 @@ public class SysUserController {
|
||||
|
||||
}
|
||||
|
||||
@RequiresPermissions("system:user:queryById")
|
||||
@SaCheckPermission("system:user:queryById")
|
||||
@RequestMapping(value = "/queryById", method = RequestMethod.GET)
|
||||
public Result<SysUser> queryById(@RequestParam(name = "id", required = true) String id) {
|
||||
Result<SysUser> result = new Result<SysUser>();
|
||||
@ -357,7 +358,7 @@ public class SysUserController {
|
||||
return result;
|
||||
}
|
||||
|
||||
@RequiresPermissions("system:user:queryUserRole")
|
||||
@SaCheckPermission("system:user:queryUserRole")
|
||||
@RequestMapping(value = "/queryUserRole", method = RequestMethod.GET)
|
||||
public Result<List<String>> queryUserRole(@RequestParam(name = "userid", required = true) String userid) {
|
||||
Result<List<String>> result = new Result<>();
|
||||
@ -410,7 +411,7 @@ public class SysUserController {
|
||||
/**
|
||||
* 修改密码
|
||||
*/
|
||||
@RequiresPermissions("system:user:changepwd")
|
||||
@SaCheckPermission("system:user:changepwd")
|
||||
@RequestMapping(value = "/changePassword", method = RequestMethod.PUT)
|
||||
public Result<?> changePassword(@RequestBody SysUser sysUser, HttpServletRequest request) {
|
||||
//-------------------------------------------------------------------------------------
|
||||
@ -427,7 +428,7 @@ public class SysUserController {
|
||||
}
|
||||
sysUser.setId(u.getId());
|
||||
// 代码逻辑说明: [VUEN-234]修改密码添加敏感日志------------
|
||||
LoginUser loginUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser loginUser = LoginUserUtils.getSessionUser();
|
||||
baseCommonService.addLog("修改用户 "+sysUser.getUsername()+" 的密码,操作人: " +loginUser.getUsername() ,CommonConstant.LOG_TYPE_2, 2);
|
||||
return sysUserService.changePassword(sysUser);
|
||||
}
|
||||
@ -540,7 +541,7 @@ public class SysUserController {
|
||||
* @param request
|
||||
* @param sysUser
|
||||
*/
|
||||
@RequiresPermissions("system:user:export")
|
||||
@SaCheckPermission("system:user:export")
|
||||
@RequestMapping(value = "/exportXls")
|
||||
public ModelAndView exportXls(SysUser sysUser,HttpServletRequest request) {
|
||||
// Step.1 组装查询条件
|
||||
@ -576,7 +577,7 @@ public class SysUserController {
|
||||
//导出文件名称
|
||||
mv.addObject(NormalExcelConstants.FILE_NAME, "用户列表");
|
||||
mv.addObject(NormalExcelConstants.CLASS, SysUserExportVo.class);
|
||||
LoginUser user = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser user = LoginUserUtils.getSessionUser();
|
||||
ExportParams exportParams = new ExportParams("导入规则:\n" +
|
||||
"1. 用户名为必填项,仅支持新增数据导入;\n" +
|
||||
"2. 多个部门、角色或负责部门请用英文分号 ; 分隔,如:财务部;研发部;\n" +
|
||||
@ -607,7 +608,7 @@ public class SysUserController {
|
||||
* @param response
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:user:import")
|
||||
@SaCheckPermission("system:user:import")
|
||||
@RequestMapping(value = "/importExcel", method = RequestMethod.POST)
|
||||
public Result<?> importExcel(HttpServletRequest request, HttpServletResponse response)throws IOException {
|
||||
//return ImportOldUserUtil.importOldSysUser(request);
|
||||
@ -662,14 +663,14 @@ public class SysUserController {
|
||||
/**
|
||||
* 首页用户重置密码
|
||||
*/
|
||||
@RequiresPermissions("system:user:updatepwd")
|
||||
@SaCheckPermission("system:user:updatepwd")
|
||||
@RequestMapping(value = "/updatePassword", method = RequestMethod.PUT)
|
||||
public Result<?> updatePassword(@RequestBody JSONObject json) {
|
||||
String username = json.getString("username");
|
||||
String oldpassword = json.getString("oldpassword");
|
||||
String password = json.getString("password");
|
||||
String confirmpassword = json.getString("confirmpassword");
|
||||
LoginUser sysUser = (LoginUser)SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
if(!sysUser.getUsername().equals(username)){
|
||||
return Result.error("只允许修改自己的密码!");
|
||||
}
|
||||
@ -678,7 +679,7 @@ public class SysUserController {
|
||||
return Result.error("用户不存在!");
|
||||
}
|
||||
// 代码逻辑说明: [VUEN-234]修改密码添加敏感日志------------
|
||||
LoginUser loginUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser loginUser = LoginUserUtils.getSessionUser();
|
||||
baseCommonService.addLog("修改密码,username: " +loginUser.getUsername() ,CommonConstant.LOG_TYPE_2, 2);
|
||||
return sysUserService.resetPassword(username,oldpassword,password,confirmpassword);
|
||||
}
|
||||
@ -703,7 +704,7 @@ public class SysUserController {
|
||||
* @param
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:user:addUserRole")
|
||||
@SaCheckPermission("system:user:addUserRole")
|
||||
@RequestMapping(value = "/addSysUserRole", method = RequestMethod.POST)
|
||||
public Result<String> addSysUserRole(@RequestBody SysUserRoleVO sysUserRoleVO) {
|
||||
Result<String> result = new Result<String>();
|
||||
@ -735,7 +736,7 @@ public class SysUserController {
|
||||
* @param
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:user:deleteRole")
|
||||
@SaCheckPermission("system:user:deleteRole")
|
||||
@RequestMapping(value = "/deleteUserRole", method = RequestMethod.DELETE)
|
||||
public Result<SysUserRole> deleteUserRole(@RequestParam(name="roleId") String roleId,
|
||||
@RequestParam(name="userId",required=true) String userId
|
||||
@ -759,7 +760,7 @@ public class SysUserController {
|
||||
* @param
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:user:deleteRoleBatch")
|
||||
@SaCheckPermission("system:user:deleteRoleBatch")
|
||||
@RequestMapping(value = "/deleteUserRoleBatch", method = RequestMethod.DELETE)
|
||||
public Result<SysUserRole> deleteUserRoleBatch(
|
||||
@RequestParam(name="roleId") String roleId,
|
||||
@ -791,7 +792,7 @@ public class SysUserController {
|
||||
List<String> subDepids = new ArrayList<>();
|
||||
//部门id为空时,查询我的部门下所有用户
|
||||
if(oConvertUtils.isEmpty(depId)){
|
||||
LoginUser user = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser user = LoginUserUtils.getSessionUser();
|
||||
int userIdentity = user.getUserIdentity() != null?user.getUserIdentity():CommonConstant.USER_IDENTITY_1;
|
||||
// 代码逻辑说明: [QQYUN-10775]验证码可以复用 #7674------------
|
||||
if(oConvertUtils.isNotEmpty(userIdentity) && userIdentity == CommonConstant.USER_IDENTITY_2
|
||||
@ -939,7 +940,7 @@ public class SysUserController {
|
||||
/**
|
||||
* 给指定部门添加对应的用户
|
||||
*/
|
||||
@RequiresPermissions("system:user:editDepartWithUser")
|
||||
@SaCheckPermission("system:user:editDepartWithUser")
|
||||
@RequestMapping(value = "/editSysDepartWithUser", method = RequestMethod.POST)
|
||||
public Result<String> editSysDepartWithUser(@RequestBody SysDepartUsersVO sysDepartUsersVO) {
|
||||
Result<String> result = new Result<String>();
|
||||
@ -974,7 +975,7 @@ public class SysUserController {
|
||||
/**
|
||||
* 删除指定机构的用户关系
|
||||
*/
|
||||
@RequiresPermissions("system:user:deleteUserInDepart")
|
||||
@SaCheckPermission("system:user:deleteUserInDepart")
|
||||
@RequestMapping(value = "/deleteUserInDepart", method = RequestMethod.DELETE)
|
||||
public Result<SysUserDepart> deleteUserInDepart(@RequestParam(name="depId") String depId,
|
||||
@RequestParam(name="userId",required=true) String userId
|
||||
@ -1006,7 +1007,7 @@ public class SysUserController {
|
||||
/**
|
||||
* 批量删除指定机构的用户关系
|
||||
*/
|
||||
@RequiresPermissions("system:user:deleteUserInDepartBatch")
|
||||
@SaCheckPermission("system:user:deleteUserInDepartBatch")
|
||||
@RequestMapping(value = "/deleteUserInDepartBatch", method = RequestMethod.DELETE)
|
||||
public Result<SysUserDepart> deleteUserInDepartBatch(
|
||||
@RequestParam(name="depId") String depId,
|
||||
@ -1038,7 +1039,7 @@ public class SysUserController {
|
||||
public Result<Map<String,Object>> getCurrentUserDeparts() {
|
||||
Result<Map<String,Object>> result = new Result<Map<String,Object>>();
|
||||
try {
|
||||
LoginUser sysUser = (LoginUser)SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
List<SysDepart> list = this.sysDepartService.queryUserDeparts(sysUser.getId());
|
||||
Map<String,Object> map = new HashMap(5);
|
||||
map.put("list", list);
|
||||
@ -1419,7 +1420,7 @@ public class SysUserController {
|
||||
* @param userIds 被删除的用户ID,多个id用半角逗号分割
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:user:deleteRecycleBin")
|
||||
@SaCheckPermission("system:user:deleteRecycleBin")
|
||||
@RequestMapping(value = "/deleteRecycleBin", method = RequestMethod.DELETE)
|
||||
public Result deleteRecycleBin(@RequestParam("userIds") String userIds) {
|
||||
if (StringUtils.isNotBlank(userIds)) {
|
||||
@ -1434,7 +1435,7 @@ public class SysUserController {
|
||||
* @param jsonObject
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("system:user:app:edit")
|
||||
@SaCheckPermission("system:user:app:edit")
|
||||
@RequestMapping(value = "/appEdit", method = {RequestMethod.PUT,RequestMethod.POST})
|
||||
public Result<SysUser> appEdit(HttpServletRequest request,@RequestBody JSONObject jsonObject) {
|
||||
Result<SysUser> result = new Result<SysUser>();
|
||||
@ -1801,7 +1802,7 @@ public class SysUserController {
|
||||
* @return
|
||||
*/
|
||||
@PostMapping("/login/setting/userEdit")
|
||||
@RequiresPermissions("system:user:setting:edit")
|
||||
@SaCheckPermission("system:user:setting:edit")
|
||||
public Result<String> userEdit(@RequestBody SysUser sysUser, HttpServletRequest request) {
|
||||
String username = JwtUtil.getUserNameByToken(request);
|
||||
SysUser user = sysUserService.getById(sysUser.getId());
|
||||
@ -1913,7 +1914,7 @@ public class SysUserController {
|
||||
public Result<?> changeLoginTenantId(@RequestBody SysUser sysUser){
|
||||
Result<String> result = new Result<>();
|
||||
Integer tenantId = sysUser.getLoginTenantId();
|
||||
LoginUser loginUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser loginUser = LoginUserUtils.getSessionUser();
|
||||
String userId = loginUser.getId();
|
||||
|
||||
// 判断 指定的租户ID是不是当前登录用户的租户
|
||||
|
||||
@ -1,28 +1,23 @@
|
||||
package org.jeecg.modules.system.controller;
|
||||
|
||||
import cn.dev33.satoken.session.SaSession;
|
||||
import cn.dev33.satoken.stp.StpUtil;
|
||||
import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.commons.lang.StringUtils;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.constant.CacheConstant;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.system.util.JwtUtil;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.jeecg.common.util.RedisUtil;
|
||||
import org.jeecg.common.util.oConvertUtils;
|
||||
import org.jeecg.modules.base.service.BaseCommonService;
|
||||
import org.jeecg.modules.system.service.ISysUserService;
|
||||
import org.jeecg.modules.system.service.impl.SysBaseApiImpl;
|
||||
import org.jeecg.modules.system.vo.SysUserOnlineVO;
|
||||
import org.springframework.beans.BeanUtils;
|
||||
import org.springframework.beans.factory.annotation.Autowired;
|
||||
import org.springframework.data.redis.core.RedisTemplate;
|
||||
import org.springframework.web.bind.annotation.*;
|
||||
|
||||
import jakarta.annotation.Resource;
|
||||
import java.util.ArrayList;
|
||||
import java.util.Collection;
|
||||
import java.util.Collections;
|
||||
import java.util.List;
|
||||
|
||||
@ -39,41 +34,58 @@ public class SysUserOnlineController {
|
||||
|
||||
@Autowired
|
||||
private RedisUtil redisUtil;
|
||||
@Autowired
|
||||
public RedisTemplate redisTemplate;
|
||||
@Autowired
|
||||
public ISysUserService userService;
|
||||
@Autowired
|
||||
private SysBaseApiImpl sysBaseApi;
|
||||
@Resource
|
||||
private BaseCommonService baseCommonService;
|
||||
|
||||
/**
|
||||
* 获取在线用户列表(使用Sa-Token)
|
||||
*/
|
||||
@RequestMapping(value = "/list", method = RequestMethod.GET)
|
||||
public Result<Page<SysUserOnlineVO>> list(@RequestParam(name="username", required=false) String username,
|
||||
@RequestParam(name="pageNo", defaultValue="1") Integer pageNo,@RequestParam(name="pageSize", defaultValue="10") Integer pageSize) {
|
||||
Collection<String> keys = redisUtil.scan(CommonConstant.PREFIX_USER_TOKEN + "*");
|
||||
List<SysUserOnlineVO> onlineList = new ArrayList<SysUserOnlineVO>();
|
||||
for (String key : keys) {
|
||||
String token = (String)redisUtil.get(key);
|
||||
if (StringUtils.isNotEmpty(token)) {
|
||||
SysUserOnlineVO online = new SysUserOnlineVO();
|
||||
online.setToken(token);
|
||||
//TODO 改成一次性查询
|
||||
LoginUser loginUser = sysBaseApi.getUserByName(JwtUtil.getUsername(token));
|
||||
if (loginUser != null && !"_reserve_user_external".equals(loginUser.getUsername())) {
|
||||
//验证用户名是否与传过来的用户名相同
|
||||
boolean isMatchUsername=true;
|
||||
//判断用户名是否为空,并且当前循环的用户不包含传过来的用户名,那么就设成false
|
||||
if(oConvertUtils.isNotEmpty(username) && !loginUser.getUsername().contains(username)){
|
||||
isMatchUsername = false;
|
||||
@RequestParam(name="pageNo", defaultValue="1") Integer pageNo,
|
||||
@RequestParam(name="pageSize", defaultValue="10") Integer pageSize) {
|
||||
List<SysUserOnlineVO> onlineList = new ArrayList<>();
|
||||
|
||||
try {
|
||||
// 使用Sa-Token获取所有在线用户的session ID列表
|
||||
List<String> sessionIdList = StpUtil.searchSessionId("", 0, -1, false);
|
||||
|
||||
for (String sessionId : sessionIdList) {
|
||||
try {
|
||||
// 获取session
|
||||
SaSession session = StpUtil.getSessionBySessionId(sessionId);
|
||||
if (session == null) {
|
||||
continue;
|
||||
}
|
||||
if(isMatchUsername){
|
||||
BeanUtils.copyProperties(loginUser, online);
|
||||
onlineList.add(online);
|
||||
|
||||
// 从session中获取用户信息
|
||||
LoginUser loginUser = (LoginUser) session.get("loginUser");
|
||||
if (loginUser != null && !"_reserve_user_external".equals(loginUser.getUsername())) {
|
||||
// 用户名筛选
|
||||
if (oConvertUtils.isEmpty(username) || loginUser.getUsername().contains(username)) {
|
||||
SysUserOnlineVO online = new SysUserOnlineVO();
|
||||
BeanUtils.copyProperties(loginUser, online);
|
||||
|
||||
// 获取该用户的token(loginId现在是username)
|
||||
try {
|
||||
String token = StpUtil.getTokenValueByLoginId(loginUser.getUsername());
|
||||
online.setToken(token);
|
||||
} catch (Exception e) {
|
||||
log.debug("获取用户token失败: {}", e.getMessage());
|
||||
}
|
||||
|
||||
onlineList.add(online);
|
||||
}
|
||||
}
|
||||
} catch (Exception e) {
|
||||
// 旧的Session数据可能导致反序列化失败,记录debug级别日志即可
|
||||
log.debug("获取session失败(可能是旧数据): {}", e.getMessage());
|
||||
}
|
||||
}
|
||||
} catch (Exception e) {
|
||||
log.error("获取在线用户列表失败: {}", e.getMessage(), e);
|
||||
}
|
||||
|
||||
Collections.reverse(onlineList);
|
||||
|
||||
Page<SysUserOnlineVO> page = new Page<SysUserOnlineVO>(pageNo, pageSize);
|
||||
@ -98,30 +110,33 @@ public class SysUserOnlineController {
|
||||
}
|
||||
|
||||
/**
|
||||
* 强退用户
|
||||
* 强退用户(使用Sa-Token)
|
||||
*/
|
||||
@RequestMapping(value = "/forceLogout",method = RequestMethod.POST)
|
||||
public Result<Object> forceLogout(@RequestBody SysUserOnlineVO online) {
|
||||
//用户退出逻辑
|
||||
if(oConvertUtils.isEmpty(online.getToken())) {
|
||||
return Result.error("退出登录失败!");
|
||||
}
|
||||
String username = JwtUtil.getUsername(online.getToken());
|
||||
LoginUser sysUser = sysBaseApi.getUserByName(username);
|
||||
if(sysUser!=null) {
|
||||
baseCommonService.addLog("强制: "+sysUser.getRealname()+"退出成功!", CommonConstant.LOG_TYPE_1, null,sysUser);
|
||||
log.info(" 强制 "+sysUser.getRealname()+"退出成功! ");
|
||||
//清空用户登录Token缓存
|
||||
redisUtil.del(CommonConstant.PREFIX_USER_TOKEN + online.getToken());
|
||||
//清空用户登录Shiro权限缓存
|
||||
redisUtil.del(CommonConstant.PREFIX_USER_SHIRO_CACHE + sysUser.getId());
|
||||
//清空用户的缓存信息(包括部门信息),例如sys:cache:user::<username>
|
||||
redisUtil.del(String.format("%s::%s", CacheConstant.SYS_USERS_CACHE, sysUser.getUsername()));
|
||||
//调用shiro的logout
|
||||
SecurityUtils.getSubject().logout();
|
||||
try {
|
||||
// 验证参数
|
||||
if (oConvertUtils.isEmpty(online.getToken())) {
|
||||
return Result.error("Token不能为空!");
|
||||
}
|
||||
|
||||
// 使用Sa-Token通过token强制退出登录
|
||||
StpUtil.logoutByTokenValue(online.getToken());
|
||||
|
||||
// 清空用户的缓存信息(如果有用户名)
|
||||
if (oConvertUtils.isNotEmpty(online.getUsername())) {
|
||||
redisUtil.del(String.format("%s::%s", CacheConstant.SYS_USERS_CACHE, online.getUsername()));
|
||||
}
|
||||
|
||||
// 记录日志
|
||||
String username = oConvertUtils.isNotEmpty(online.getUsername()) ? online.getUsername() : "未知用户";
|
||||
baseCommonService.addLog("强制: " + username + " 退出成功!", CommonConstant.LOG_TYPE_1, null);
|
||||
log.info("强制 {} 退出成功!", username);
|
||||
|
||||
return Result.ok("退出登录成功!");
|
||||
}else {
|
||||
return Result.error("Token无效!");
|
||||
} catch (Exception e) {
|
||||
log.error("强制退出失败: {}", e.getMessage(), e);
|
||||
return Result.error("退出登录失败:" + e.getMessage());
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
@ -5,8 +5,8 @@ import com.alibaba.fastjson.JSONObject;
|
||||
import com.baomidou.mybatisplus.core.conditions.query.LambdaQueryWrapper;
|
||||
import com.jeecg.dingtalk.api.core.response.Response;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
import org.jeecg.common.api.dto.message.MessageDTO;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.config.TenantContext;
|
||||
@ -424,7 +424,7 @@ public class ThirdAppController {
|
||||
* @return
|
||||
*/
|
||||
@DeleteMapping(value = "/deleteThirdAppConfig")
|
||||
@RequiresPermissions("system:third:config:delete")
|
||||
@SaCheckPermission("system:third:config:delete")
|
||||
public Result<String> deleteThirdAppConfig(@RequestParam(name="id",required=true) String id) {
|
||||
Result<String> result = new Result<>();
|
||||
SysThirdAppConfig config = appConfigService.getById(id);
|
||||
@ -504,7 +504,7 @@ public class ThirdAppController {
|
||||
*/
|
||||
@GetMapping("/getThirdAccountByUserId")
|
||||
public Result<List<SysThirdAccount>> getThirdAccountByUserId(@RequestParam(name="thirdType") String thirdType){
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
LambdaQueryWrapper<SysThirdAccount> query = new LambdaQueryWrapper<>();
|
||||
//根据id查询
|
||||
query.eq(SysThirdAccount::getSysUserId,sysUser.getId());
|
||||
@ -535,7 +535,7 @@ public class ThirdAppController {
|
||||
*/
|
||||
@DeleteMapping("/deleteThirdAccount")
|
||||
public Result<String> deleteThirdAccountById(@RequestBody SysThirdAccount sysThirdAccount){
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
if(!sysUser.getId().equals(sysThirdAccount.getSysUserId())){
|
||||
return Result.error("无权修改他人信息");
|
||||
}
|
||||
|
||||
@ -17,7 +17,9 @@ import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.constant.enums.MessageTypeEnum;
|
||||
import org.jeecg.common.system.api.ISysBaseAPI;
|
||||
import org.jeecg.common.system.util.JwtUtil;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.jeecg.common.util.*;
|
||||
import org.springframework.beans.BeanUtils;
|
||||
import org.jeecg.modules.base.service.BaseCommonService;
|
||||
import org.jeecg.modules.system.entity.SysDepart;
|
||||
import org.jeecg.modules.system.entity.SysThirdAccount;
|
||||
@ -206,12 +208,10 @@ public class ThirdLoginController {
|
||||
}
|
||||
|
||||
private String saveToken(SysUser user) {
|
||||
// 生成token
|
||||
String token = JwtUtil.sign(user.getUsername(), user.getPassword(), CommonConstant.CLIENT_TYPE_PC);
|
||||
redisUtil.set(CommonConstant.PREFIX_USER_TOKEN + token, token);
|
||||
// 设置超时时间
|
||||
redisUtil.expire(CommonConstant.PREFIX_USER_TOKEN + token, JwtUtil.EXPIRE_TIME * 2 / 1000);
|
||||
return token;
|
||||
// 使用封装方法:一步完成登录和设置用户信息
|
||||
LoginUser loginUser = new LoginUser();
|
||||
BeanUtils.copyProperties(user, loginUser);
|
||||
return LoginUserUtils.doLogin(loginUser);
|
||||
}
|
||||
|
||||
/**
|
||||
@ -228,7 +228,7 @@ public class ThirdLoginController {
|
||||
Result<JSONObject> result = new Result<JSONObject>();
|
||||
String username = JwtUtil.getUsername(token);
|
||||
// 代码逻辑说明: [QQYUN-11021]三方登录接口通过token获取用户信息漏洞修复------------
|
||||
if (!TokenUtils.verifyToken(token, sysBaseAPI, redisUtil)) {
|
||||
if (!TokenUtils.verifyToken(token, sysBaseAPI)) {
|
||||
return Result.noauth("token验证失败");
|
||||
}
|
||||
//1. 校验用户是否有效
|
||||
|
||||
@ -7,7 +7,7 @@ import lombok.Data;
|
||||
import lombok.EqualsAndHashCode;
|
||||
import lombok.experimental.Accessors;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.config.mqtoken.UserTokenContext;
|
||||
import org.jeecg.common.system.util.JwtUtil;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
@ -94,7 +94,7 @@ public class SysDataLog implements Serializable {
|
||||
*/
|
||||
public void autoSetCreateName() {
|
||||
try {
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
this.setCreateName(sysUser.getRealname());
|
||||
} catch (Exception e) {
|
||||
// QQYUN-13669 进一步优化:解决某些异步场景下获取用户信息为空的问题
|
||||
|
||||
@ -8,7 +8,7 @@ import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.commons.compress.archivers.zip.Zip64Mode;
|
||||
import org.apache.commons.compress.archivers.zip.ZipArchiveOutputStream;
|
||||
import org.apache.commons.lang3.StringUtils;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.jeecg.common.util.FileDownloadUtils;
|
||||
@ -164,7 +164,7 @@ public class SysAnnouncementServiceImpl extends ServiceImpl<SysAnnouncementMappe
|
||||
|
||||
@Override
|
||||
public void completeAnnouncementSendInfo() {
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
String userId = sysUser.getId();
|
||||
List<String> announcementIds = this.getNotSendedAnnouncementlist(userId);
|
||||
List<SysAnnouncementSend> sysAnnouncementSendList = new ArrayList<>();
|
||||
@ -214,8 +214,8 @@ public class SysAnnouncementServiceImpl extends ServiceImpl<SysAnnouncementMappe
|
||||
// completeAnnouncementSendInfo();
|
||||
// });
|
||||
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
log.debug(" 获取登录人 LoginUser id: {}", sysUser.getId());
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
log.info(" 获取登录人 LoginUser id: {}", sysUser.getId());
|
||||
Page<SysAnnouncement> page = new Page<SysAnnouncement>(pageNo,pageSize);
|
||||
List<SysAnnouncement> list = baseMapper.queryAllMessageList(page, sysUser.getId(), fromUser, starFlag, busType, msgCategory,beginDate, endDate, noticeType);
|
||||
return list;
|
||||
@ -223,13 +223,13 @@ public class SysAnnouncementServiceImpl extends ServiceImpl<SysAnnouncementMappe
|
||||
|
||||
@Override
|
||||
public void updateReaded(List<String> annoceIdList) {
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
sysAnnouncementSendMapper.updateReaded(sysUser.getId(), annoceIdList);
|
||||
}
|
||||
|
||||
@Override
|
||||
public void clearAllUnReadMessage() {
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
sysAnnouncementSendMapper.clearAllUnReadMessage(sysUser.getId());
|
||||
}
|
||||
|
||||
|
||||
@ -20,7 +20,7 @@ import freemarker.template.TemplateException;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.commons.lang.StringUtils;
|
||||
import org.apache.commons.lang3.ObjectUtils;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.api.dto.AiragFlowDTO;
|
||||
import org.jeecg.common.api.dto.DataLogDTO;
|
||||
import org.jeecg.common.api.dto.OnlineAuthDTO;
|
||||
@ -669,7 +669,7 @@ public class SysBaseApiImpl implements ISysBaseAPI {
|
||||
public void updateSysAnnounReadFlag(String busType, String busId) {
|
||||
SysAnnouncement announcement = sysAnnouncementMapper.selectOne(new QueryWrapper<SysAnnouncement>().eq("bus_type",busType).eq("bus_id",busId));
|
||||
if(announcement != null){
|
||||
LoginUser sysUser = (LoginUser)SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
String userId = sysUser.getId();
|
||||
LambdaUpdateWrapper<SysAnnouncementSend> updateWrapper = new UpdateWrapper().lambda();
|
||||
updateWrapper.set(SysAnnouncementSend::getReadFlag, CommonConstant.HAS_READ_FLAG);
|
||||
|
||||
@ -13,7 +13,7 @@ import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
import com.baomidou.mybatisplus.extension.service.impl.ServiceImpl;
|
||||
import io.netty.util.internal.StringUtil;
|
||||
import org.apache.commons.lang.StringUtils;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.config.TenantContext;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.constant.FillRuleConstant;
|
||||
@ -1004,7 +1004,7 @@ public class SysDepartServiceImpl extends ServiceImpl<SysDepartMapper, SysDepart
|
||||
*/
|
||||
@Override
|
||||
public List<SysDepart> getMyDepartList() {
|
||||
LoginUser user = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser user = LoginUserUtils.getSessionUser();
|
||||
String userId = user.getId();
|
||||
//字典code集合
|
||||
List<String> list = new ArrayList<>();
|
||||
|
||||
@ -2,7 +2,7 @@ package org.jeecg.modules.system.service.impl;
|
||||
import cn.hutool.core.collection.CollectionUtil;
|
||||
import cn.hutool.core.util.RandomUtil;
|
||||
import com.baomidou.mybatisplus.core.conditions.query.LambdaQueryWrapper;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.constant.SymbolConstant;
|
||||
import org.jeecg.common.constant.TenantConstant;
|
||||
@ -13,7 +13,6 @@ import org.jeecg.modules.aop.TenantLog;
|
||||
import org.jeecg.modules.system.entity.SysPackPermission;
|
||||
import org.jeecg.modules.system.entity.SysTenantPack;
|
||||
import org.jeecg.modules.system.entity.SysTenantPackUser;
|
||||
import org.jeecg.modules.system.entity.SysUserTenant;
|
||||
import org.jeecg.modules.system.mapper.*;
|
||||
import org.jeecg.modules.system.service.ISysTenantPackService;
|
||||
import org.springframework.beans.BeanUtils;
|
||||
@ -221,7 +220,7 @@ public class SysTenantPackServiceImpl extends ServiceImpl<SysTenantPackMapper, S
|
||||
packId = sysTenantPackSuperAdmin.getId();
|
||||
}
|
||||
//step.1.2 补充人员与套餐包的关系数据
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
SysTenantPackUser packUser = new SysTenantPackUser(tenantId, packId, sysUser.getId());
|
||||
packUser.setRealname(sysUser.getRealname());
|
||||
packUser.setPackName(superAdminPack.getPackName());
|
||||
|
||||
@ -8,7 +8,7 @@ import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
import com.baomidou.mybatisplus.extension.service.impl.ServiceImpl;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.commons.collections.CollectionUtils;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.api.dto.message.BusMessageDTO;
|
||||
import org.jeecg.common.api.dto.message.MessageDTO;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
@ -32,11 +32,8 @@ import org.jeecg.modules.system.service.ISysTenantPackService;
|
||||
import org.jeecg.modules.system.service.ISysTenantService;
|
||||
import org.jeecg.modules.system.service.ISysUserService;
|
||||
import org.jeecg.modules.system.vo.tenant.*;
|
||||
import org.springframework.beans.BeanUtils;
|
||||
import org.springframework.beans.factory.NoSuchBeanDefinitionException;
|
||||
import org.springframework.beans.factory.annotation.Autowired;
|
||||
import org.springframework.cache.annotation.CacheEvict;
|
||||
import org.springframework.context.annotation.Lazy;
|
||||
import org.springframework.stereotype.Service;
|
||||
|
||||
import java.util.*;
|
||||
@ -156,7 +153,7 @@ public class SysTenantServiceImpl extends ServiceImpl<SysTenantMapper, SysTenant
|
||||
* @param id
|
||||
*/
|
||||
private void sendInvitationTenantMessage(SysUser user, String id) {
|
||||
LoginUser sysUser = (LoginUser)SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
// 发消息
|
||||
SysTenant sysTenant = this.baseMapper.querySysTenant((Integer.valueOf(id)));
|
||||
MessageDTO messageDTO = new MessageDTO();
|
||||
@ -217,7 +214,7 @@ public class SysTenantServiceImpl extends ServiceImpl<SysTenantMapper, SysTenant
|
||||
this.save(sysTenant);
|
||||
//代码逻辑说明:【QQYUN-5723】1、把当前创建人加入到租户关系里面------------
|
||||
//当前登录人的id
|
||||
LoginUser loginUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser loginUser = LoginUserUtils.getSessionUser();
|
||||
this.saveTenantRelation(sysTenant.getId(),loginUser.getId());
|
||||
}
|
||||
|
||||
@ -408,7 +405,7 @@ public class SysTenantServiceImpl extends ServiceImpl<SysTenantMapper, SysTenant
|
||||
@Override
|
||||
public Result<String> invitationUser(String phone, String departId) {
|
||||
Result<String> result = new Result<>();
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
|
||||
//1、查询用户信息,判断用户是否存在
|
||||
SysUser userByPhone = userService.getUserByPhone(phone);
|
||||
@ -470,7 +467,7 @@ public class SysTenantServiceImpl extends ServiceImpl<SysTenantMapper, SysTenant
|
||||
}
|
||||
|
||||
TenantDepartAuthInfo info = new TenantDepartAuthInfo();
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
String userId = sysUser.getId();
|
||||
boolean superAdmin = false;
|
||||
// 查询pack表
|
||||
@ -660,7 +657,7 @@ public class SysTenantServiceImpl extends ServiceImpl<SysTenantMapper, SysTenant
|
||||
// 发消息
|
||||
SysUser user = userService.getById(sysTenantPackUser.getUserId());
|
||||
SysTenant sysTenant = this.baseMapper.querySysTenant(sysTenantPackUser.getTenantId());
|
||||
LoginUser loginUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser loginUser = LoginUserUtils.getSessionUser();
|
||||
MessageDTO messageDTO = new MessageDTO();
|
||||
messageDTO.setToAll(false);
|
||||
messageDTO.setToUser(user.getUsername());
|
||||
@ -831,7 +828,7 @@ public class SysTenantServiceImpl extends ServiceImpl<SysTenantMapper, SysTenant
|
||||
|
||||
@Override
|
||||
public Long getApplySuperAdminCount() {
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
int tenantId = oConvertUtils.getInt(TenantContext.getTenant(), 0);
|
||||
return baseMapper.getApplySuperAdminCount(sysUser.getId(),tenantId);
|
||||
}
|
||||
@ -896,7 +893,7 @@ public class SysTenantServiceImpl extends ServiceImpl<SysTenantMapper, SysTenant
|
||||
//被删除人的密码
|
||||
String password = sysUser.getPassword();
|
||||
//当前登录用户
|
||||
LoginUser user = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser user = LoginUserUtils.getSessionUser();
|
||||
//step1 判断当前用户是否为当前租户的管理员(只有超级管理员和账号管理员可以删除)
|
||||
Long isHaveAdmin = sysTenantPackUserMapper.izHaveBuyAuth(user.getId(), tenantId);
|
||||
if(null == isHaveAdmin || 0 == isHaveAdmin){
|
||||
@ -938,7 +935,7 @@ public class SysTenantServiceImpl extends ServiceImpl<SysTenantMapper, SysTenant
|
||||
}
|
||||
//step1 验证创建时间
|
||||
//当前登录用户
|
||||
LoginUser user = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser user = LoginUserUtils.getSessionUser();
|
||||
Date createTime = sysUser.getCreateTime();
|
||||
boolean sameDay = DateUtils.isSameDay(createTime, new Date());
|
||||
if(!sameDay){
|
||||
@ -965,7 +962,7 @@ public class SysTenantServiceImpl extends ServiceImpl<SysTenantMapper, SysTenant
|
||||
//被删除人的密码
|
||||
String password = sysUser.getPassword();
|
||||
//当前登录用户
|
||||
LoginUser user = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser user = LoginUserUtils.getSessionUser();
|
||||
//step1 判断当前用户是否为当前租户的创建者才可以删除
|
||||
SysTenant sysTenant = this.getById(tenantId);
|
||||
if(null == sysTenant || !user.getUsername().equals(sysTenant.getCreateBy())){
|
||||
|
||||
@ -7,7 +7,7 @@ import com.jeecg.dingtalk.api.core.response.Response;
|
||||
import com.jeecg.dingtalk.api.core.vo.AccessToken;
|
||||
import com.jeecg.dingtalk.api.user.JdtUserAPI;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.exception.JeecgBootException;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
@ -188,7 +188,7 @@ public class SysThirdAccountServiceImpl extends ServiceImpl<SysThirdAccountMappe
|
||||
String thirdUserUuid = sysThirdAccount.getThirdUserUuid();
|
||||
String thirdType = sysThirdAccount.getThirdType();
|
||||
//获取当前登录用户
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
//当前第三方用户已被其他用户所绑定
|
||||
SysThirdAccount oneByThirdUserId = this.getOneByUuidAndThirdType(thirdUserUuid, thirdType,CommonConstant.TENANT_ID_DEFAULT_VALUE, null);
|
||||
if(null != oneByThirdUserId){
|
||||
|
||||
@ -6,11 +6,10 @@ import com.baomidou.mybatisplus.core.metadata.IPage;
|
||||
import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
import com.baomidou.mybatisplus.extension.service.impl.ServiceImpl;
|
||||
import org.apache.commons.lang3.StringUtils;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.config.TenantContext;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.constant.SymbolConstant;
|
||||
import org.jeecg.common.constant.enums.DepartCategoryEnum;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.jeecg.common.util.oConvertUtils;
|
||||
import org.jeecg.config.mybatis.MybatisPlusSaasConfig;
|
||||
@ -247,7 +246,7 @@ public class SysUserDepartServiceImpl extends ServiceImpl<SysUserDepartMapper, S
|
||||
IPage<SysUser> pageList = null;
|
||||
// 部门ID不存在 直接查询用户表即可
|
||||
Page<SysUser> page = new Page<>(pageNo, pageSize);
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
if(oConvertUtils.isEmpty(departId)){
|
||||
LambdaQueryWrapper<SysUser> query = new LambdaQueryWrapper<>();
|
||||
query.eq(SysUser::getStatus,Integer.parseInt(CommonConstant.STATUS_1));
|
||||
@ -284,7 +283,7 @@ public class SysUserDepartServiceImpl extends ServiceImpl<SysUserDepartMapper, S
|
||||
IPage<SysUser> pageList = null;
|
||||
// 部门ID不存在 直接查询用户表即可
|
||||
Page<SysUser> page = new Page<>(pageNo, pageSize);
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
|
||||
List<String> userIdList = new ArrayList<>();
|
||||
List<String> inUsernameList = new ArrayList<>();
|
||||
|
||||
@ -7,7 +7,6 @@ import com.alibaba.fastjson.JSONObject;
|
||||
import com.aliyuncs.exceptions.ClientException;
|
||||
import com.baomidou.mybatisplus.core.conditions.query.LambdaQueryWrapper;
|
||||
import com.baomidou.mybatisplus.core.conditions.query.QueryWrapper;
|
||||
import com.baomidou.mybatisplus.core.conditions.update.LambdaUpdateWrapper;
|
||||
import com.baomidou.mybatisplus.core.conditions.update.UpdateWrapper;
|
||||
import com.baomidou.mybatisplus.core.metadata.IPage;
|
||||
import com.baomidou.mybatisplus.core.toolkit.CollectionUtils;
|
||||
@ -16,7 +15,7 @@ import com.baomidou.mybatisplus.extension.service.impl.ServiceImpl;
|
||||
import lombok.extern.slf4j.Slf4j;
|
||||
import org.apache.commons.lang.StringUtils;
|
||||
import org.apache.commons.lang3.ObjectUtils;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.api.dto.message.MessageDTO;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.config.TenantContext;
|
||||
@ -186,7 +185,7 @@ public class SysUserServiceImpl extends ServiceImpl<SysUserMapper, SysUser> impl
|
||||
// Object bean = ResourceUtil.getImplementationClass(DataEnhanceEnum.getClassPath(tenantId,lowAppId));
|
||||
// if(null != bean){
|
||||
// UserFilterEnhance userEnhanceService = (UserFilterEnhance) bean;
|
||||
// LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
// LoginUser sysUser = LoginUserUtils.getLoginUser();
|
||||
// List<String> userIds = userEnhanceService.getUserIds(sysUser.getId());
|
||||
// if(CollectionUtil.isNotEmpty(userIds)){
|
||||
// queryWrapper.in("id", userIds);
|
||||
@ -1658,7 +1657,7 @@ public class SysUserServiceImpl extends ServiceImpl<SysUserMapper, SysUser> impl
|
||||
//导出文件名称
|
||||
mv.addObject(NormalExcelConstants.FILE_NAME, "用户列表");
|
||||
mv.addObject(NormalExcelConstants.CLASS, AppExportUserVo.class);
|
||||
LoginUser user = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser user = LoginUserUtils.getSessionUser();
|
||||
ExportParams exportParams = new ExportParams("导入规则:\n" +
|
||||
"1、存在用户编号时,数据会根据用户编号进行匹配,匹配成功后只会更新职位和工号;\n" +
|
||||
"2、不存在用户编号时,支持手机号、邮箱、姓名、部们、职位、工号导入,其中手机号必填;\n" +
|
||||
@ -2040,7 +2039,7 @@ public class SysUserServiceImpl extends ServiceImpl<SysUserMapper, SysUser> impl
|
||||
userTenant.setStatus(CommonConstant.USER_TENANT_INVITE);
|
||||
userTenantMapper.insert(userTenant);
|
||||
//发送系统消息通知
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
MessageDTO messageDTO = new MessageDTO();
|
||||
String title = sysUser.getRealname() + " 邀请您加入 " + tenantName + "。";
|
||||
messageDTO.setTitle(title);
|
||||
@ -2707,7 +2706,7 @@ public class SysUserServiceImpl extends ServiceImpl<SysUserMapper, SysUser> impl
|
||||
|
||||
@Override
|
||||
public void updatePasswordNotBindPhone(String oldPassword, String password, String username) {
|
||||
LoginUser sysUser = (LoginUser)SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getSessionUser();
|
||||
//step1 只能修改自己的密码
|
||||
if(!sysUser.getUsername().equals(username)){
|
||||
throw new JeecgBootBizTipException("只允许修改自己的密码!");
|
||||
|
||||
@ -4,7 +4,7 @@ import com.baomidou.mybatisplus.core.conditions.query.LambdaQueryWrapper;
|
||||
import com.baomidou.mybatisplus.core.metadata.IPage;
|
||||
import com.baomidou.mybatisplus.extension.plugins.pagination.Page;
|
||||
import org.apache.commons.lang.StringUtils;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.constant.CacheConstant;
|
||||
import org.jeecg.common.constant.CommonConstant;
|
||||
import org.jeecg.common.constant.SymbolConstant;
|
||||
|
||||
@ -37,7 +37,7 @@ import com.alibaba.fastjson.JSON;
|
||||
import io.swagger.v3.oas.annotations.tags.Tag;
|
||||
import io.swagger.v3.oas.annotations.Operation;
|
||||
import org.jeecg.common.aspect.annotation.AutoLog;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
<#assign bpm_flag=false>
|
||||
<#assign has_multi_query_field=false>
|
||||
<#list originalColumns as po>
|
||||
@ -126,7 +126,7 @@ public class ${entityName}Controller extends JeecgController<${entityName}, I${e
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-添加")
|
||||
@Operation(summary="${tableVo.ftlDescription}-添加")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:add")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:add")
|
||||
@PostMapping(value = "/add")
|
||||
public Result<String> add(@RequestBody ${entityName} ${entityName?uncap_first}) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
@ -161,7 +161,7 @@ public class ${entityName}Controller extends JeecgController<${entityName}, I${e
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-编辑")
|
||||
@Operation(summary="${tableVo.ftlDescription}-编辑")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:edit")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:edit")
|
||||
@RequestMapping(value = "/edit", method = {RequestMethod.PUT,RequestMethod.POST})
|
||||
public Result<String> edit(@RequestBody ${entityName} ${entityName?uncap_first}) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
@ -192,7 +192,7 @@ public class ${entityName}Controller extends JeecgController<${entityName}, I${e
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-通过id删除")
|
||||
@Operation(summary="${tableVo.ftlDescription}-通过id删除")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:delete")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:delete")
|
||||
@DeleteMapping(value = "/delete")
|
||||
public Result<String> delete(@RequestParam(name="id",required=true) String id) {
|
||||
${entityName?uncap_first}Service.removeById(id);
|
||||
@ -207,7 +207,7 @@ public class ${entityName}Controller extends JeecgController<${entityName}, I${e
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-批量删除")
|
||||
@Operation(summary="${tableVo.ftlDescription}-批量删除")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:deleteBatch")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:deleteBatch")
|
||||
@DeleteMapping(value = "/deleteBatch")
|
||||
public Result<String> deleteBatch(@RequestParam(name="ids",required=true) String ids) {
|
||||
this.${entityName?uncap_first}Service.removeByIds(Arrays.asList(ids.split(",")));
|
||||
@ -237,7 +237,7 @@ public class ${entityName}Controller extends JeecgController<${entityName}, I${e
|
||||
* @param request
|
||||
* @param ${entityName?uncap_first}
|
||||
*/
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:exportXls")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:exportXls")
|
||||
@RequestMapping(value = "/exportXls")
|
||||
public ModelAndView exportXls(HttpServletRequest request, ${entityName} ${entityName?uncap_first}) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
@ -258,7 +258,7 @@ public class ${entityName}Controller extends JeecgController<${entityName}, I${e
|
||||
* @param response
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:importExcel")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:importExcel")
|
||||
@RequestMapping(value = "/importExcel", method = RequestMethod.POST)
|
||||
public Result<?> importExcel(HttpServletRequest request, HttpServletResponse response) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
|
||||
@ -18,7 +18,7 @@ import org.jeecgframework.poi.excel.entity.ExportParams;
|
||||
import org.jeecgframework.poi.excel.entity.ImportParams;
|
||||
import org.jeecgframework.poi.excel.view.JeecgEntityExcelView;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.system.query.QueryGenerator;
|
||||
import org.jeecg.common.util.oConvertUtils;
|
||||
@ -46,7 +46,7 @@ import com.alibaba.fastjson.JSON;
|
||||
import io.swagger.v3.oas.annotations.tags.Tag;
|
||||
import io.swagger.v3.oas.annotations.Operation;
|
||||
import org.jeecg.common.aspect.annotation.AutoLog;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
<#assign bpm_flag=false>
|
||||
<#list originalColumns as po>
|
||||
<#if po.fieldDbName=='bpm_status'>
|
||||
@ -102,7 +102,7 @@ public class ${entityName}Controller {
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-添加")
|
||||
@Operation(summary="${tableVo.ftlDescription}-添加")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:add")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:add")
|
||||
@PostMapping(value = "/add")
|
||||
public Result<String> add(@RequestBody ${entityName}Page ${entityName?uncap_first}Page) {
|
||||
${entityName} ${entityName?uncap_first} = new ${entityName}();
|
||||
@ -122,7 +122,7 @@ public class ${entityName}Controller {
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-编辑")
|
||||
@Operation(summary="${tableVo.ftlDescription}-编辑")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:edit")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:edit")
|
||||
@RequestMapping(value = "/edit", method = {RequestMethod.PUT,RequestMethod.POST})
|
||||
public Result<String> edit(@RequestBody ${entityName}Page ${entityName?uncap_first}Page) {
|
||||
${entityName} ${entityName?uncap_first} = new ${entityName}();
|
||||
@ -143,7 +143,7 @@ public class ${entityName}Controller {
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-通过id删除")
|
||||
@Operation(summary="${tableVo.ftlDescription}-通过id删除")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:delete")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:delete")
|
||||
@DeleteMapping(value = "/delete")
|
||||
public Result<String> delete(@RequestParam(name="id",required=true) String id) {
|
||||
${entityName?uncap_first}Service.delMain(id);
|
||||
@ -158,7 +158,7 @@ public class ${entityName}Controller {
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-批量删除")
|
||||
@Operation(summary="${tableVo.ftlDescription}-批量删除")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:deleteBatch")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:deleteBatch")
|
||||
@DeleteMapping(value = "/deleteBatch")
|
||||
public Result<String> deleteBatch(@RequestParam(name="ids",required=true) String ids) {
|
||||
this.${entityName?uncap_first}Service.delBatchMain(Arrays.asList(ids.split(",")));
|
||||
@ -205,12 +205,12 @@ public class ${entityName}Controller {
|
||||
* @param request
|
||||
* @param ${entityName?uncap_first}
|
||||
*/
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:exportXls")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:exportXls")
|
||||
@RequestMapping(value = "/exportXls")
|
||||
public ModelAndView exportXls(HttpServletRequest request, ${entityName} ${entityName?uncap_first}) {
|
||||
// Step.1 组装查询条件查询数据
|
||||
QueryWrapper<${entityName}> queryWrapper = QueryGenerator.initQueryWrapper(${entityName?uncap_first}, request.getParameterMap());
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getLoginUser();
|
||||
|
||||
//配置选中数据查询条件
|
||||
String selections = request.getParameter("selections");
|
||||
@ -249,7 +249,7 @@ public class ${entityName}Controller {
|
||||
* @param response
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:importExcel")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:importExcel")
|
||||
@RequestMapping(value = "/importExcel", method = RequestMethod.POST)
|
||||
public Result<?> importExcel(HttpServletRequest request, HttpServletResponse response) {
|
||||
MultipartHttpServletRequest multipartRequest = (MultipartHttpServletRequest) request;
|
||||
|
||||
@ -36,7 +36,7 @@ import com.alibaba.fastjson.JSON;
|
||||
import io.swagger.v3.oas.annotations.tags.Tag;
|
||||
import io.swagger.v3.oas.annotations.Operation;
|
||||
import org.jeecg.common.aspect.annotation.AutoLog;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
|
||||
/**
|
||||
* @Description: ${tableVo.ftlDescription}
|
||||
@ -227,7 +227,7 @@ public class ${entityName}Controller extends JeecgController<${entityName}, I${e
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-添加")
|
||||
@Operation(summary="${tableVo.ftlDescription}-添加")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:add")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:add")
|
||||
@PostMapping(value = "/add")
|
||||
public Result<String> add(@RequestBody ${entityName} ${entityName?uncap_first}) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
@ -258,7 +258,7 @@ public class ${entityName}Controller extends JeecgController<${entityName}, I${e
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-编辑")
|
||||
@Operation(summary="${tableVo.ftlDescription}-编辑")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:edit")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:edit")
|
||||
@RequestMapping(value = "/edit", method = {RequestMethod.PUT,RequestMethod.POST})
|
||||
public Result<String> edit(@RequestBody ${entityName} ${entityName?uncap_first}) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
@ -289,7 +289,7 @@ public class ${entityName}Controller extends JeecgController<${entityName}, I${e
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-通过id删除")
|
||||
@Operation(summary="${tableVo.ftlDescription}-通过id删除")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:delete")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:delete")
|
||||
@DeleteMapping(value = "/delete")
|
||||
public Result<String> delete(@RequestParam(name="id",required=true) String id) {
|
||||
${entityName?uncap_first}Service.delete${entityName}(id);
|
||||
@ -304,7 +304,7 @@ public class ${entityName}Controller extends JeecgController<${entityName}, I${e
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-批量删除")
|
||||
@Operation(summary="${tableVo.ftlDescription}-批量删除")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:deleteBatch")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:deleteBatch")
|
||||
@DeleteMapping(value = "/deleteBatch")
|
||||
public Result<String> deleteBatch(@RequestParam(name="ids",required=true) String ids) {
|
||||
this.${entityName?uncap_first}Service.removeByIds(Arrays.asList(ids.split(",")));
|
||||
@ -334,7 +334,7 @@ public class ${entityName}Controller extends JeecgController<${entityName}, I${e
|
||||
* @param request
|
||||
* @param ${entityName?uncap_first}
|
||||
*/
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:exportXls")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:exportXls")
|
||||
@RequestMapping(value = "/exportXls")
|
||||
public ModelAndView exportXls(HttpServletRequest request, ${entityName} ${entityName?uncap_first}) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
@ -355,7 +355,7 @@ public class ${entityName}Controller extends JeecgController<${entityName}, I${e
|
||||
* @param response
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:importExcel")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:importExcel")
|
||||
@RequestMapping(value = "/importExcel", method = RequestMethod.POST)
|
||||
public Result<?> importExcel(HttpServletRequest request, HttpServletResponse response) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
|
||||
@ -28,7 +28,7 @@ import ${bussiPackage}.${entityPackage}.service.I${sub.entityName}Service;
|
||||
import io.swagger.v3.oas.annotations.tags.Tag;
|
||||
import io.swagger.v3.oas.annotations.Operation;
|
||||
import org.jeecg.common.aspect.annotation.AutoLog;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.jeecgframework.poi.excel.ExcelImportUtil;
|
||||
import org.jeecgframework.poi.excel.def.NormalExcelConstants;
|
||||
@ -41,7 +41,7 @@ import java.io.IOException;
|
||||
import java.util.List;
|
||||
import java.util.Map;
|
||||
import java.util.stream.Collectors;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
<#assign has_multi_query_field=false>
|
||||
<#list originalColumns as po>
|
||||
<#if po.isQuery=='Y' && (po.classType=='list' || po.classType=='list_multi' || po.classType=='radio' || po.classType=='checkbox')>
|
||||
@ -131,7 +131,7 @@ public class ${entityName}Controller extends JeecgController<${entityName}, I${e
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-添加")
|
||||
@Operation(summary="${tableVo.ftlDescription}-添加")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:add")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:add")
|
||||
@PostMapping(value = "/add")
|
||||
public Result<String> add(@RequestBody ${entityName} ${entityName?uncap_first}) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
@ -161,7 +161,7 @@ public class ${entityName}Controller extends JeecgController<${entityName}, I${e
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-编辑")
|
||||
@Operation(summary="${tableVo.ftlDescription}-编辑")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:edit")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:edit")
|
||||
@RequestMapping(value = "/edit", method = {RequestMethod.PUT,RequestMethod.POST})
|
||||
public Result<String> edit(@RequestBody ${entityName} ${entityName?uncap_first}) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
@ -191,7 +191,7 @@ public class ${entityName}Controller extends JeecgController<${entityName}, I${e
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-通过id删除")
|
||||
@Operation(summary="${tableVo.ftlDescription}-通过id删除")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:delete")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:delete")
|
||||
@DeleteMapping(value = "/delete")
|
||||
public Result<String> delete(@RequestParam(name="id",required=true) String id) {
|
||||
${entityName?uncap_first}Service.delMain(id);
|
||||
@ -205,7 +205,7 @@ public class ${entityName}Controller extends JeecgController<${entityName}, I${e
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-批量删除")
|
||||
@Operation(summary="${tableVo.ftlDescription}-批量删除")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:deleteBatch")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:deleteBatch")
|
||||
@DeleteMapping(value = "/deleteBatch")
|
||||
public Result<String> deleteBatch(@RequestParam(name="ids",required=true) String ids) {
|
||||
this.${entityName?uncap_first}Service.delBatchMain(Arrays.asList(ids.split(",")));
|
||||
@ -216,7 +216,7 @@ public class ${entityName}Controller extends JeecgController<${entityName}, I${e
|
||||
* 导出
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:exportXls")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:exportXls")
|
||||
@RequestMapping(value = "/exportXls")
|
||||
public ModelAndView exportXls(HttpServletRequest request, ${entityName} ${entityName?uncap_first}) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
@ -234,7 +234,7 @@ public class ${entityName}Controller extends JeecgController<${entityName}, I${e
|
||||
* 导入
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:importExcel")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:importExcel")
|
||||
@RequestMapping(value = "/importExcel", method = RequestMethod.POST)
|
||||
public Result<?> importExcel(HttpServletRequest request, HttpServletResponse response) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
@ -329,7 +329,7 @@ public class ${entityName}Controller extends JeecgController<${entityName}, I${e
|
||||
public ModelAndView export${sub.entityName}(HttpServletRequest request, ${sub.entityName} ${sub.entityName?uncap_first}) {
|
||||
// Step.1 组装查询条件
|
||||
QueryWrapper<${sub.entityName}> queryWrapper = QueryGenerator.initQueryWrapper(${sub.entityName?uncap_first}, request.getParameterMap());
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getLoginUser();
|
||||
|
||||
// Step.2 获取导出数据
|
||||
List<${sub.entityName}> pageList = ${sub.entityName?uncap_first}Service.list(queryWrapper);
|
||||
|
||||
@ -19,7 +19,7 @@ import org.jeecgframework.poi.excel.entity.ExportParams;
|
||||
import org.jeecgframework.poi.excel.entity.ImportParams;
|
||||
import org.jeecgframework.poi.excel.view.JeecgEntityExcelView;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.system.query.QueryGenerator;
|
||||
import org.jeecg.common.system.query.QueryRuleEnum;
|
||||
@ -48,7 +48,7 @@ import com.alibaba.fastjson.JSON;
|
||||
import io.swagger.v3.oas.annotations.tags.Tag;
|
||||
import io.swagger.v3.oas.annotations.Operation;
|
||||
import org.jeecg.common.aspect.annotation.AutoLog;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
<#assign has_multi_query_field=false>
|
||||
<#list originalColumns as po>
|
||||
<#if po.isQuery=='Y' && (po.classType=='list' || po.classType=='list_multi' || po.classType=='radio' || po.classType=='checkbox')>
|
||||
@ -135,7 +135,7 @@ public class ${entityName}Controller {
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-添加")
|
||||
@Operation(summary="${tableVo.ftlDescription}-添加")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:add")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:add")
|
||||
@PostMapping(value = "/add")
|
||||
public Result<String> add(@RequestBody ${entityName}Page ${entityName?uncap_first}Page) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
@ -168,7 +168,7 @@ public class ${entityName}Controller {
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-编辑")
|
||||
@Operation(summary="${tableVo.ftlDescription}-编辑")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:edit")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:edit")
|
||||
@RequestMapping(value = "/edit", method = {RequestMethod.PUT,RequestMethod.POST})
|
||||
public Result<String> edit(@RequestBody ${entityName}Page ${entityName?uncap_first}Page) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
@ -205,7 +205,7 @@ public class ${entityName}Controller {
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-通过id删除")
|
||||
@Operation(summary="${tableVo.ftlDescription}-通过id删除")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:delete")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:delete")
|
||||
@DeleteMapping(value = "/delete")
|
||||
public Result<String> delete(@RequestParam(name="id",required=true) String id) {
|
||||
${entityName?uncap_first}Service.delMain(id);
|
||||
@ -220,7 +220,7 @@ public class ${entityName}Controller {
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-批量删除")
|
||||
@Operation(summary="${tableVo.ftlDescription}-批量删除")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:deleteBatch")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:deleteBatch")
|
||||
@DeleteMapping(value = "/deleteBatch")
|
||||
public Result<String> deleteBatch(@RequestParam(name="ids",required=true) String ids) {
|
||||
this.${entityName?uncap_first}Service.delBatchMain(Arrays.asList(ids.split(",")));
|
||||
@ -271,7 +271,7 @@ public class ${entityName}Controller {
|
||||
* @param request
|
||||
* @param ${entityName?uncap_first}
|
||||
*/
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:exportXls")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:exportXls")
|
||||
@RequestMapping(value = "/exportXls")
|
||||
public ModelAndView exportXls(HttpServletRequest request, ${entityName} ${entityName?uncap_first}) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
@ -284,7 +284,7 @@ public class ${entityName}Controller {
|
||||
</#if>
|
||||
// Step.1 组装查询条件查询数据
|
||||
QueryWrapper<${entityName}> queryWrapper = QueryGenerator.initQueryWrapper(${entityName?uncap_first}, request.getParameterMap());
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getLoginUser();
|
||||
|
||||
//配置选中数据查询条件
|
||||
String selections = request.getParameter("selections");
|
||||
@ -323,7 +323,7 @@ public class ${entityName}Controller {
|
||||
* @param response
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:importExcel")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:importExcel")
|
||||
@RequestMapping(value = "/importExcel", method = RequestMethod.POST)
|
||||
public Result<?> importExcel(HttpServletRequest request, HttpServletResponse response) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
|
||||
@ -19,7 +19,7 @@ import org.jeecgframework.poi.excel.entity.ExportParams;
|
||||
import org.jeecgframework.poi.excel.entity.ImportParams;
|
||||
import org.jeecgframework.poi.excel.view.JeecgEntityExcelView;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.system.query.QueryGenerator;
|
||||
import org.jeecg.common.system.query.QueryRuleEnum;
|
||||
@ -48,7 +48,7 @@ import com.alibaba.fastjson.JSON;
|
||||
import io.swagger.v3.oas.annotations.tags.Tag;
|
||||
import io.swagger.v3.oas.annotations.Operation;
|
||||
import org.jeecg.common.aspect.annotation.AutoLog;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
|
||||
<#assign bpm_flag=false>
|
||||
<#assign has_multi_query_field=false>
|
||||
@ -144,7 +144,7 @@ public class ${entityName}Controller {
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-添加")
|
||||
@Operation(summary="${tableVo.ftlDescription}-添加")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:add")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:add")
|
||||
@PostMapping(value = "/add")
|
||||
public Result<String> add(@RequestBody ${entityName}Page ${entityName?uncap_first}Page) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
@ -180,7 +180,7 @@ public class ${entityName}Controller {
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-编辑")
|
||||
@Operation(summary="${tableVo.ftlDescription}-编辑")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:edit")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:edit")
|
||||
@RequestMapping(value = "/edit", method = {RequestMethod.PUT,RequestMethod.POST})
|
||||
public Result<String> edit(@RequestBody ${entityName}Page ${entityName?uncap_first}Page) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
@ -217,7 +217,7 @@ public class ${entityName}Controller {
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-通过id删除")
|
||||
@Operation(summary="${tableVo.ftlDescription}-通过id删除")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:delete")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:delete")
|
||||
@DeleteMapping(value = "/delete")
|
||||
public Result<String> delete(@RequestParam(name="id",required=true) String id) {
|
||||
${entityName?uncap_first}Service.delMain(id);
|
||||
@ -232,7 +232,7 @@ public class ${entityName}Controller {
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-批量删除")
|
||||
@Operation(summary="${tableVo.ftlDescription}-批量删除")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:deleteBatch")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:deleteBatch")
|
||||
@DeleteMapping(value = "/deleteBatch")
|
||||
public Result<String> deleteBatch(@RequestParam(name="ids",required=true) String ids) {
|
||||
this.${entityName?uncap_first}Service.delBatchMain(Arrays.asList(ids.split(",")));
|
||||
@ -279,7 +279,7 @@ public class ${entityName}Controller {
|
||||
* @param request
|
||||
* @param ${entityName?uncap_first}
|
||||
*/
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:exportXls")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:exportXls")
|
||||
@RequestMapping(value = "/exportXls")
|
||||
public ModelAndView exportXls(HttpServletRequest request, ${entityName} ${entityName?uncap_first}) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
@ -293,7 +293,7 @@ public class ${entityName}Controller {
|
||||
|
||||
// Step.1 组装查询条件查询数据
|
||||
QueryWrapper<${entityName}> queryWrapper = QueryGenerator.initQueryWrapper(${entityName?uncap_first}, request.getParameterMap());
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getLoginUser();
|
||||
|
||||
//配置选中数据查询条件
|
||||
String selections = request.getParameter("selections");
|
||||
@ -332,7 +332,7 @@ public class ${entityName}Controller {
|
||||
* @param response
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:importExcel")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:importExcel")
|
||||
@RequestMapping(value = "/importExcel", method = RequestMethod.POST)
|
||||
public Result<?> importExcel(HttpServletRequest request, HttpServletResponse response) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
|
||||
@ -19,7 +19,7 @@ import org.jeecgframework.poi.excel.entity.ExportParams;
|
||||
import org.jeecgframework.poi.excel.entity.ImportParams;
|
||||
import org.jeecgframework.poi.excel.view.JeecgEntityExcelView;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecg.common.api.vo.Result;
|
||||
import org.jeecg.common.system.query.QueryGenerator;
|
||||
import org.jeecg.common.system.query.QueryRuleEnum;
|
||||
@ -48,7 +48,7 @@ import com.alibaba.fastjson.JSON;
|
||||
import io.swagger.v3.oas.annotations.tags.Tag;
|
||||
import io.swagger.v3.oas.annotations.Operation;
|
||||
import org.jeecg.common.aspect.annotation.AutoLog;
|
||||
import org.apache.shiro.authz.annotation.RequiresPermissions;
|
||||
import cn.dev33.satoken.annotation.SaCheckPermission;
|
||||
<#assign has_multi_query_field=false>
|
||||
<#list originalColumns as po>
|
||||
<#if po.isQuery=='Y' && (po.classType=='list' || po.classType=='list_multi' || po.classType=='radio' || po.classType=='checkbox')>
|
||||
@ -135,7 +135,7 @@ public class ${entityName}Controller {
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-添加")
|
||||
@Operation(summary="${tableVo.ftlDescription}-添加")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:add")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:add")
|
||||
@PostMapping(value = "/add")
|
||||
public Result<String> add(@RequestBody ${entityName}Page ${entityName?uncap_first}Page) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
@ -168,7 +168,7 @@ public class ${entityName}Controller {
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-编辑")
|
||||
@Operation(summary="${tableVo.ftlDescription}-编辑")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:edit")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:edit")
|
||||
@RequestMapping(value = "/edit", method = {RequestMethod.PUT,RequestMethod.POST})
|
||||
public Result<String> edit(@RequestBody ${entityName}Page ${entityName?uncap_first}Page) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
@ -205,7 +205,7 @@ public class ${entityName}Controller {
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-通过id删除")
|
||||
@Operation(summary="${tableVo.ftlDescription}-通过id删除")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:delete")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:delete")
|
||||
@DeleteMapping(value = "/delete")
|
||||
public Result<String> delete(@RequestParam(name="id",required=true) String id) {
|
||||
${entityName?uncap_first}Service.delMain(id);
|
||||
@ -220,7 +220,7 @@ public class ${entityName}Controller {
|
||||
*/
|
||||
@AutoLog(value = "${tableVo.ftlDescription}-批量删除")
|
||||
@Operation(summary="${tableVo.ftlDescription}-批量删除")
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:deleteBatch")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:deleteBatch")
|
||||
@DeleteMapping(value = "/deleteBatch")
|
||||
public Result<String> deleteBatch(@RequestParam(name="ids",required=true) String ids) {
|
||||
this.${entityName?uncap_first}Service.delBatchMain(Arrays.asList(ids.split(",")));
|
||||
@ -267,7 +267,7 @@ public class ${entityName}Controller {
|
||||
* @param request
|
||||
* @param ${entityName?uncap_first}
|
||||
*/
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:exportXls")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:exportXls")
|
||||
@RequestMapping(value = "/exportXls")
|
||||
public ModelAndView exportXls(HttpServletRequest request, ${entityName} ${entityName?uncap_first}) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
@ -281,7 +281,7 @@ public class ${entityName}Controller {
|
||||
|
||||
// Step.1 组装查询条件查询数据
|
||||
QueryWrapper<${entityName}> queryWrapper = QueryGenerator.initQueryWrapper(${entityName?uncap_first}, request.getParameterMap());
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getLoginUser();
|
||||
|
||||
//配置选中数据查询条件
|
||||
String selections = request.getParameter("selections");
|
||||
@ -320,7 +320,7 @@ public class ${entityName}Controller {
|
||||
* @param response
|
||||
* @return
|
||||
*/
|
||||
@RequiresPermissions("${entityPackage}:${tableName}:importExcel")
|
||||
@SaCheckPermission("${entityPackage}:${tableName}:importExcel")
|
||||
@RequestMapping(value = "/importExcel", method = RequestMethod.POST)
|
||||
public Result<?> importExcel(HttpServletRequest request, HttpServletResponse response) {
|
||||
<#if enhanceJavaList?size gt 0>
|
||||
|
||||
@ -11,7 +11,7 @@ import java.util.Map;
|
||||
import jakarta.servlet.http.HttpServletRequest;
|
||||
import jakarta.servlet.http.HttpServletResponse;
|
||||
import org.jeecg.common.system.vo.LoginUser;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecgframework.poi.excel.ExcelImportUtil;
|
||||
import org.jeecgframework.poi.excel.def.NormalExcelConstants;
|
||||
import org.jeecgframework.poi.excel.entity.ExportParams;
|
||||
@ -185,7 +185,7 @@ public class ${entityName}Controller {
|
||||
public ModelAndView exportXls(HttpServletRequest request, ${entityName} ${entityName?uncap_first}) {
|
||||
// Step.1 组装查询条件
|
||||
QueryWrapper<${entityName}> queryWrapper = QueryGenerator.initQueryWrapper(${entityName?uncap_first}, request.getParameterMap());
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getLoginUser();
|
||||
|
||||
//Step.2 获取导出数据
|
||||
List<${entityName}Page> pageList = new ArrayList<${entityName}Page>();
|
||||
|
||||
@ -10,7 +10,7 @@ import java.util.Map;
|
||||
|
||||
import jakarta.servlet.http.HttpServletRequest;
|
||||
import jakarta.servlet.http.HttpServletResponse;
|
||||
import org.apache.shiro.SecurityUtils;
|
||||
import org.jeecg.common.util.LoginUserUtils;
|
||||
import org.jeecgframework.poi.excel.ExcelImportUtil;
|
||||
import org.jeecgframework.poi.excel.def.NormalExcelConstants;
|
||||
import org.jeecgframework.poi.excel.entity.ExportParams;
|
||||
@ -273,7 +273,7 @@ ${sub.entityName?uncap_first}.get${key}()!=null<#rt/>
|
||||
public ModelAndView exportXls(HttpServletRequest request, ${entityName} ${entityName?uncap_first}) {
|
||||
// Step.1 组装查询条件
|
||||
QueryWrapper<${entityName}> queryWrapper = QueryGenerator.initQueryWrapper(${entityName?uncap_first}, request.getParameterMap());
|
||||
LoginUser sysUser = (LoginUser) SecurityUtils.getSubject().getPrincipal();
|
||||
LoginUser sysUser = LoginUserUtils.getLoginUser();
|
||||
|
||||
//Step.2 获取导出数据
|
||||
List<${entityName}Page> pageList = new ArrayList<${entityName}Page>();
|
||||
|
||||
@ -37,6 +37,7 @@
|
||||
<artifactId>spring-boot-properties-migrator</artifactId>
|
||||
<scope>runtime</scope>
|
||||
</dependency>
|
||||
|
||||
<dependency>
|
||||
<groupId>jakarta.servlet</groupId>
|
||||
<artifactId>jakarta.servlet-api</artifactId>
|
||||
|
||||
@ -19,6 +19,31 @@ management:
|
||||
exposure:
|
||||
include: metrics,httpexchanges,jeecghttptrace
|
||||
|
||||
################ Sa-Token 配置 (文档: https://sa-token.cc) ################
|
||||
sa-token:
|
||||
# token 名称(同时也是 cookie 名称)
|
||||
token-name: X-Access-Token
|
||||
# token 有效期(单位:秒) 默认30天,-1 代表永久有效
|
||||
timeout: 2592000
|
||||
# token 最低活跃频率(单位:秒),如果 token 超过此时间没有访问系统就会被冻结,默认-1 代表不限制,永不冻结
|
||||
active-timeout: -1
|
||||
# 是否允许同一账号多地同时登录 (为 true 时允许一起登录, 为 false 时新登录挤掉旧登录)
|
||||
is-concurrent: true
|
||||
# 在多人登录同一账号时,是否共用一个 token (为 true 时所有登录共用一个 token, 为 false 时每次登录新建一个 token)
|
||||
is-share: false
|
||||
# token 风格(使用jwt-simple保持与原JWT token格式一致)
|
||||
token-style: jwt-simple
|
||||
# 是否输出操作日志
|
||||
is-log: false
|
||||
# 是否从 cookie 中读取 token
|
||||
is-read-cookie: false
|
||||
# 是否从 head 中读取 token
|
||||
is-read-header: true
|
||||
# 是否从请求体(URL参数)里读取 token
|
||||
is-read-body: true
|
||||
# jwt秘钥(重要:请修改为你自己的秘钥,确保足够复杂)
|
||||
jwt-secret-key: "dd05f1c54d63749eda95f9fa6d49v442a"
|
||||
|
||||
spring:
|
||||
# main:
|
||||
# # 启动加速 (建议开发环境,开启后flyway自动升级失效)
|
||||
@ -211,8 +236,6 @@ jeecg:
|
||||
dataSourceSafe: false
|
||||
# 低代码模式(dev:开发模式,prod:发布模式——关闭所有在线开发配置能力)
|
||||
lowCodeMode: dev
|
||||
# 是否允许同一账号多地同时登录 (为 true 时允许一起登录, 为 false 时新登录挤掉旧登录)
|
||||
is-concurrent: true
|
||||
# 签名密钥串(前后端要一致,正式发布请自行修改)
|
||||
signatureSecret: dd05f1c54d63749eda95f9fa6d49v442a
|
||||
#签名拦截接口
|
||||
|
||||
Some files were not shown because too many files have changed in this diff Show More
Reference in New Issue
Block a user